In 2026, a single security breach can threaten the very survival of a business. The stakes have never been higher, and traditional approaches are no longer enough.
This essential guide will help you navigate the complex world of security governance, breaking down what really matters for resilience, compliance, and strong leadership.
We’ll explore the core pillars of security governance, proven frameworks, actionable steps, and the latest trends shaping the digital landscape. Let’s get started on building a roadmap for confident, secure growth in the year ahead.
Understanding Security Governance: Foundations and Importance
Security governance is the backbone of every resilient organization in 2026. It goes beyond technical controls, shaping how we make decisions, allocate resources, and measure progress in protecting our most valuable assets. With the stakes higher than ever, security governance ensures that security is not just an IT concern but a core business priority.
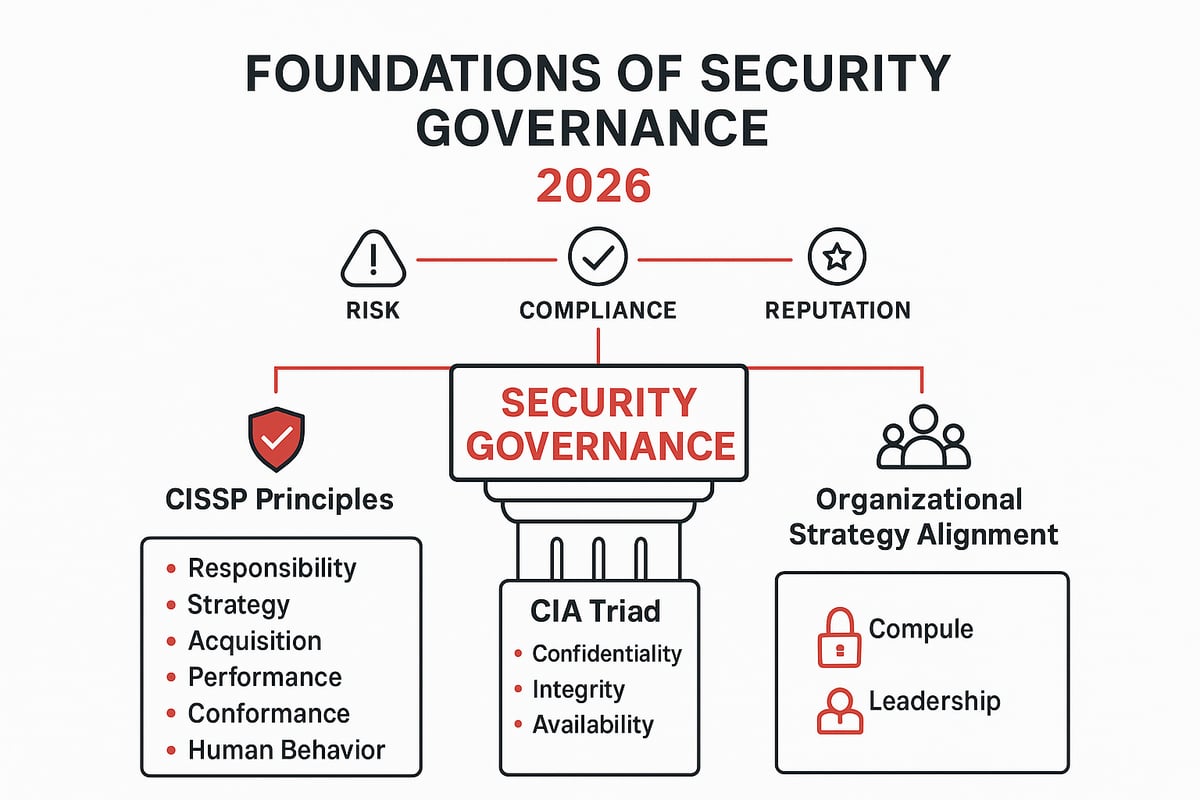
What Is Security Governance and Why Does It Matter?
Security governance is the system by which organizations direct and control their security strategies, policies, and objectives. In 2026, this means creating a framework that keeps pace with evolving threats and complex compliance demands. Security governance matters because it defines how we make decisions about risk, compliance, and business priorities. Without a strong foundation, organizations face confusion, wasted resources, and exposure to cyber incidents.
Governance vs. Management and Operations
It’s important to distinguish security governance from security management and operations. Security governance sets the direction and expectations for the entire organization. Security management translates these directions into actionable plans, while operations carry out the day-to-day tasks. By clearly separating these roles, security governance ensures everyone knows their responsibilities, reducing overlap and missed gaps.
Aligning Security Governance With Organizational Strategy
The true power of security governance lies in its ability to connect security with broader business goals. When security governance aligns with strategy, it supports innovation, protects reputation, and helps organizations adapt to change. Poor security governance leads to increased risk, regulatory penalties, and even loss of customer trust. For example, a global retailer once neglected governance, resulting in a high-profile data breach that caused financial and reputational damage.
Principles and Foundations: CISSP and the CIA Triad
Effective security governance is built on trusted principles. The CISSP framework highlights responsibility, strategy, acquisition, performance, conformance, and human behavior as keys to successful governance. These principles help us create policies, assign accountability, and measure effectiveness.
The CIA Triad, confidentiality, integrity, and availability, remains the baseline for protecting information. For organizations seeking practical steps, Security governance best practices offer actionable frameworks tailored to modern challenges.
The Evolving Threat Landscape and Real-World Consequences
Today’s threat landscape is more complex than ever. Attackers use advanced tactics, and incidents happen more frequently. Security governance must address this by staying proactive and adaptive. When organizations ignore governance, the results can be severe. Think of companies that suffered data breaches due to unclear policies or a lack of executive oversight. These failures often lead to investigations, fines, and lasting reputational harm.
Security governance is not just about compliance; it is the foundation for resilience and competitive edge in 2026.
Core Principles and Frameworks of Security Governance
Modern security governance is built on proven principles and robust frameworks. These elements create the roadmap organizations need to navigate risk, compliance, and ethical challenges. Let’s explore how these core pillars shape effective security governance and why they matter for every business in 2026.
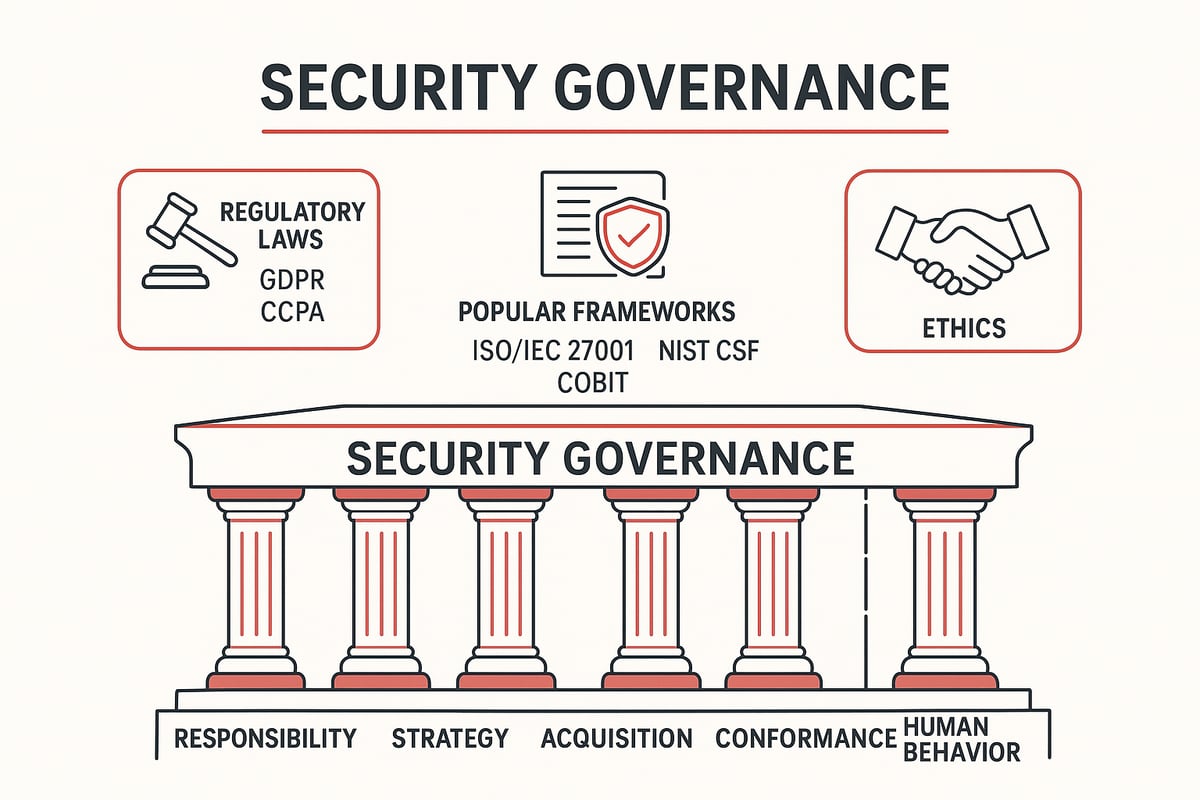
The Six CISSP Security Governance Principles
At the heart of security governance are the six CISSP principles. These guide organizations in building resilient, accountable, and ethical security programs. According to the CISSP security governance principles, the pillars include:
- Responsibility: Clear assignment of security duties to individuals and teams.
- Strategy: Alignment of security with business goals and long-term vision.
- Acquisition: Securely managing procurement, vendors, and third-party partners.
- Performance: Ongoing measurement and improvement of security effectiveness.
- Conformance: Adherence to legal, regulatory, and policy obligations.
- Human Behavior: Cultivating a culture of awareness and ethical conduct.
For example, a Fortune 500 company might embed these principles by designating accountable leaders, aligning security with business expansion, and regularly measuring progress. By weaving these values into daily operations, organizations ensure security governance is not just a policy but a living, breathing part of the culture.
Regulatory and Legal Foundations
Security governance must keep pace with an evolving legal landscape. Key laws such as the Computer Fraud and Abuse Act and the Computer Security Act set foundational standards. However, global regulations like GDPR, CCPA, and the NIS2 Directive have expanded the scope, requiring organizations to adapt quickly.
In 2026, regulatory requirements are only increasing. New privacy laws and sector-specific mandates demand continuous attention. Failing to comply can lead to severe fines, business disruptions, and reputational harm. For instance, companies that ignored GDPR updates faced penalties exceeding millions in recent years.
Integrating security governance with legal compliance is not just about avoiding penalties. It ensures business continuity and builds trust with customers and partners. Staying informed and proactive helps organizations turn compliance from a burden into a competitive advantage.
Governance Frameworks and Standards
A strong security governance program relies on established frameworks. ISO/IEC 27001 sets out requirements for an information security management system, while the NIST Cybersecurity Framework (CSF) offers flexible guidelines for risk management. COBIT, on the other hand, focuses on IT governance and aligning technology with business objectives.
Each framework has unique strengths. ISO/IEC 27001 is recognized for its structured certification process. NIST CSF is praised for its adaptability and continuous improvement cycle. COBIT is valued for bridging the gap between IT and business needs.
For example, many organizations use NIST CSF to drive ongoing improvements, track maturity, and report progress to leadership. In fact, recent surveys show that over 65% of large enterprises have adopted at least one major security governance framework. The right choice depends on your industry, objectives, and existing processes.
Ethics and Professional Conduct
Ethics is the invisible thread holding security governance together. Following codes like the CISSP Code of Ethics helps build trust with stakeholders, clients, and the public. Ethical behavior is not just a best practice; it’s a requirement for sustainable, long-term security governance.
When ethics are ignored, the fallout can be severe. Organizations have lost certifications, faced lawsuits, and suffered public backlash due to ethical lapses. A well-known incident involved an executive bypassing security controls for convenience, which led to a damaging data breach and loss of professional standing.
Embedding ethics into security governance means training, accountability, and transparency at every level. It’s about doing the right thing, even when no one is watching. In the end, ethics is the foundation that makes security governance resilient and respected.
Designing and Implementing a Security Governance Program
Building an effective security governance program can feel daunting, but breaking it down into clear, actionable steps makes it manageable for any organization. Let’s walk through the process together, step by step, so you can confidently guide your team toward greater resilience and compliance.
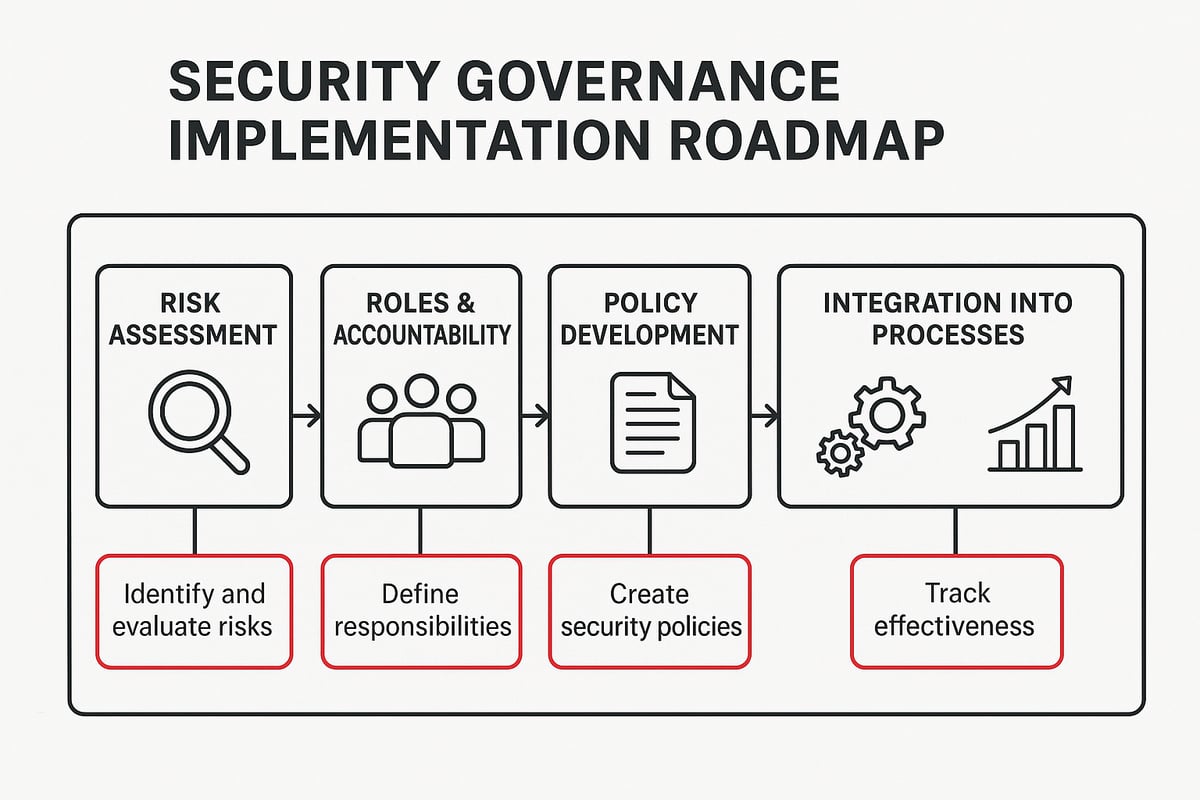
Step 1: Assessing Organizational Needs and Maturity
Every successful security governance journey begins with understanding where you stand. Start by conducting a thorough risk assessment and gap analysis. This helps you pinpoint vulnerabilities, evaluate existing controls, and understand your organization’s unique risk appetite.
Next, map your security objectives to overall business goals. This alignment ensures that security governance efforts directly support your organization’s mission, promoting buy-in from leadership and staff alike.
Use maturity models to benchmark your current security governance posture. These models help you measure progress and identify areas that need the most attention.
Engage key stakeholders from IT, business, and executive teams. Their insights and support are crucial for honest assessments and long-term success.
For example, a healthcare provider recently used a risk assessment to uncover gaps in third-party data sharing practices. By addressing these early, they avoided costly compliance issues down the road.
Want more guidance on this foundational step? Check out Cyber risk management strategies for expert tips on risk assessments and aligning governance with business priorities.
Step 2: Defining Roles, Responsibilities, and Accountability
Once you know your starting point, it’s time to clarify who does what. Defining roles and responsibilities within your security governance structure ensures everyone understands their part in keeping the organization secure.
Establish governance committees that include representatives from IT, business units, and executive leadership. Clear reporting lines and communication channels help prevent confusion during incidents or audits.
The Chief Information Security Officer (CISO) should have a direct line to the board, ensuring that security governance stays on the leadership agenda. Meanwhile, IT and business leaders need explicit accountability for implementing controls and reporting on progress.
An effective security governance board typically includes executive sponsors and subject matter experts. This structure fosters collaboration and drives results.
Clarity in roles and responsibilities not only reduces ambiguity but also empowers your team to act decisively when security issues arise.
Step 3: Policy Development and Communication
Strong policies are the backbone of security governance. Begin by drafting comprehensive security policies and standards that reflect both legal requirements and your organization’s unique needs.
Ensure these policies are aligned with industry regulations and your business objectives. This alignment avoids conflicts and ensures compliance.
Policies should be communicated clearly across the entire organization. Use training sessions, internal newsletters, and accessible policy documents to reach everyone.
For instance, when a multinational organization rolled out a new data protection policy, they held interactive workshops for every department. This approach fostered understanding and commitment at all levels.
Remember, effective security governance policies are living documents. Set a regular review schedule to keep them current as threats and business needs evolve.
Step 4: Integrating Security into Business Processes
Security governance cannot exist in a silo. It must be woven into the fabric of daily business operations. Start by embedding security controls into procurement, HR, IT, and operations workflows.
Third-party risk management is especially important. Vet vendors carefully, conduct regular assessments, and require contractual commitments to your security standards. A robust vendor risk assessment process can prevent supply chain vulnerabilities from threatening your organization.
For example, a global retailer implemented a standardized vendor onboarding process, including security questionnaires and audits. This reduced their exposure to third-party breaches and improved trust with partners.
The key takeaway: security governance should influence every business decision, from hiring to purchasing to launching new services.
Step 5: Measuring Performance and Continuous Improvement
No security governance program is complete without ongoing measurement and improvement. Establish clear KPIs and metrics to track the effectiveness of your security initiatives.
Leverage dashboards and automated reporting tools to keep leadership informed and engaged. Regular audits and reviews help you spot gaps and prioritize improvements.
Incident reviews and lessons learned are invaluable. Each event, whether a minor phishing attempt or a major breach, provides insights for refining your governance approach.
A financial institution, for example, adopted a continuous improvement cycle based on quarterly audits and real-time incident monitoring. This proactive stance helped them stay ahead of threats and regulatory changes.
According to recent studies, over 70 percent of organizations now use automated reporting for security governance, making performance tracking more efficient than ever.
Measurement drives accountability, and with the right feedback loops, your security governance program will grow stronger with every cycle.
Security Governance in the Era of Emerging Technologies
The rise of cloud computing, artificial intelligence, and remote work is reshaping how organizations approach security governance. New technologies bring fresh opportunities, but they also introduce complexity, risk, and evolving threats. To keep pace, organizations must adapt their security governance programs to be agile, resilient, and forward-looking.
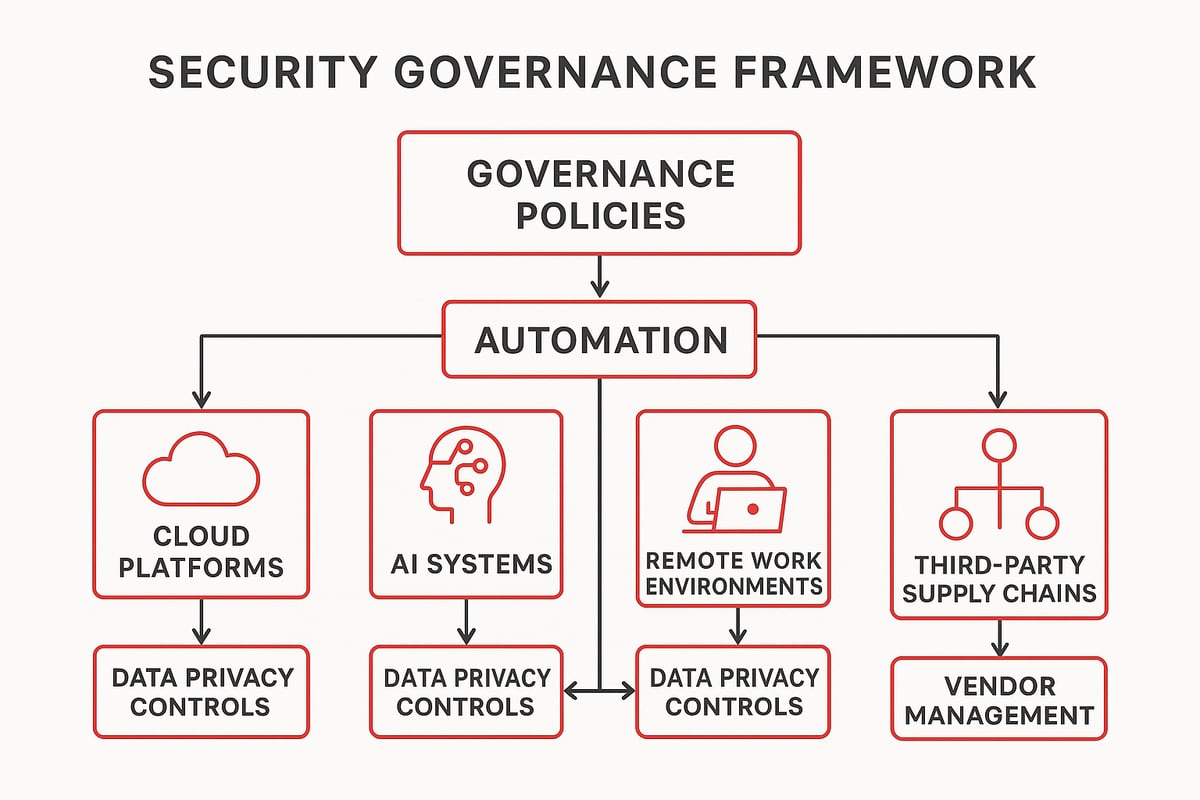
Adapting Governance for Cloud, AI, and Remote Work
Security governance must evolve quickly to address the challenges of cloud adoption, AI integration, and the realities of a distributed workforce. In cloud environments, traditional perimeter defenses no longer suffice. Governance frameworks must define access controls, cloud provider responsibilities, and data residency policies.
AI offers both promise and peril. Advanced threat detection, automated response, and risk modeling rely on AI, but so do adversaries. Security governance should set clear rules for responsible AI use, bias mitigation, and transparency.
Remote and hybrid work add another layer. Devices, networks, and identities span the globe, so governance must address endpoint security, secure collaboration, and ongoing training.
For actionable steps on aligning governance with these modern demands, see Governance and compliance essentials.
A global SaaS provider, for example, adapted its security governance by embedding cloud-specific controls, automating incident response, and updating policies for remote access. By doing so, they reduced risk and enabled secure innovation.
Managing Third-Party and Supply Chain Risk
In 2026, organizations rely more than ever on vendors, partners, and service providers. This expanded ecosystem increases the attack surface and brings new risks. Security governance must include frameworks for assessing third-party security posture, contract requirements, and ongoing monitoring.
Key steps include:
- Conducting vendor risk assessments before onboarding
- Requiring regular security attestations
- Monitoring for supply chain threats
A recent example saw a supplier breach expose sensitive data due to weak governance controls. By prioritizing third-party oversight, organizations can safeguard their assets and reputation.
Automation and Security Orchestration
Automation is transforming security governance processes. Automated policy enforcement, compliance checks, and incident response offer efficiency, consistency, and scalability. With automation, organizations can quickly identify issues and enforce standards across complex environments.
Benefits include:
- Faster response to threats
- Reduced manual errors
- Streamlined reporting to leadership
However, over-reliance on automation can introduce new risks. Human oversight remains crucial to interpret context and manage exceptions. A large enterprise used automated compliance dashboards to maintain visibility, but still required regular human review to ensure accuracy.
Data Governance and Privacy
Data is now the lifeblood of organizations, making data governance a critical pillar of security governance. As privacy regulations evolve, organizations must classify data, define retention schedules, and control access.
A healthcare organization, for example, built a data governance program that included patient data classification, automated access controls, and regular audits. This approach not only ensured compliance but also built trust with patients and regulators.
Security governance programs must integrate privacy by design, stay ahead of regulatory changes, and empower teams with clear data handling guidelines. As the perimeter disappears, strong data governance is essential to protect what matters most.
Navigating Regulatory and Compliance Challenges in 2026
In 2026, the regulatory landscape for security governance is more complex than ever. Organizations face an expanding web of global laws, including GDPR, the NIS2 Directive, and CCPA, along with sector-specific requirements in finance, healthcare, and critical infrastructure.
Each regulation brings unique obligations, and the pace of change is only accelerating. For businesses, keeping up with these shifting requirements is not just about ticking boxes. It is about protecting reputation, maintaining customer trust, and ensuring business continuity.
Staying ahead of regulatory change requires a proactive approach. Successful organizations invest in real-time monitoring of new laws and guidance, often leveraging cross-functional teams with legal, compliance, and security expertise. Industry groups and regulatory alerts help keep teams informed, while regular training ensures everyone understands their responsibilities.
Engaging with external legal counsel and participating in policy discussions can provide early warnings about emerging regulations. This way, security governance programs remain agile and responsive.
Building compliance into security governance from the ground up is essential. Instead of treating compliance as a one-off project, leading organizations embed regulatory requirements into their policies, processes, and controls. This integration ensures that compliance is always aligned with business objectives and risk appetite. By mapping controls to multiple frameworks, teams reduce duplication and simplify audits. Automating compliance checks and reporting further streamlines the process, making it easier to demonstrate due diligence to regulators and stakeholders.
Consider a financial services firm that faced mounting compliance demands from overlapping regulations. By adopting an integrated security governance model, the firm mapped legal requirements directly to security controls, unified reporting across jurisdictions, and automated evidence collection. This not only reduced the burden on staff but also improved audit outcomes and built a culture of continuous improvement.
The stakes for non-compliance are rising. According to recent industry reports, global regulatory fines for security failures increased by over 30 percent in the past year, with enforcement actions targeting both large enterprises and smaller organizations. Regulators are focusing on evidence of ongoing compliance, not just annual checklists. This trend underscores the need for robust, transparent security governance that can withstand scrutiny at any time.
Proactive compliance does more than prevent penalties. It builds trust with customers, partners, and regulators, and can even become a competitive differentiator. As regulatory harmonization efforts gain traction, especially across the EU and US, organizations that align their security governance with emerging global standards will find it easier to enter new markets and streamline operations. For deeper insights on how leadership and culture drive effective compliance, explore the Security leadership insights page.
Ultimately, compliance is just the starting line. The real goal of security governance is resilience and trust. By embedding compliance into the fabric of the organization, we not only meet legal obligations but also position ourselves to thrive in an unpredictable world. Together, we can turn regulatory challenges into opportunities for growth and leadership.
Leadership, Culture, and the Human Element in Security Governance
Building a strong culture of security awareness is at the heart of effective security governance. No matter how robust our technology or policies are, the human element remains both a powerful defense and a potential vulnerability. Organizations that prioritize open communication, shared responsibility, and ongoing dialogue about security make it easier for everyone to recognize and respond to risks. When employees from the boardroom to the front line feel empowered to speak up and take action, security becomes a shared mission, not just an IT checklist.
Leadership sets the tone for security governance. When executives and CISOs visibly champion security, it sends a clear message that protecting the organization is everyone’s responsibility. Effective leaders foster trust by listening to concerns, modeling ethical behavior, and making security a core part of business strategy. By including security on meeting agendas, celebrating positive behavior, and providing resources, leadership can inspire teams to go beyond compliance and embrace a proactive mindset.
Training and awareness programs are essential tools for bridging the gap between policy and daily practice. Regular sessions on topics like phishing, social engineering, and safe data handling help employees recognize and resist common threats.
Interactive exercises, such as simulated phishing campaigns or role-playing scenarios, can make learning engaging and memorable. According to industry reports, over 80% of breaches involve some form of human error, making ongoing education a critical pillar of security governance.
Learning from setbacks is a vital part of building resilience. Consider a manufacturing company that faced a significant breach due to shadow IT and lack of awareness. Instead of assigning blame, leaders launched a company-wide initiative to rebuild trust and improve communication. They listened to employee feedback, updated processes, and made security part of their daily conversations.
This transformation shows that a supportive culture, driven by leadership and open dialogue, can turn past failures into future strengths. In the end, technology alone cannot solve governance challenges—people and culture are the foundation of lasting security governance.
After exploring the key principles and real-world strategies for security governance in 2026, you might be wondering how to turn these insights into real change for your organization. You’re not alone—we all face the challenge of staying ahead in a fast-moving landscape.
If you’re ready to keep learning, share experiences, and get support from peers who truly get it, I invite you to join us in the Join CISO Launchpad Community. Together, we’ll turn knowledge into action and help each other build stronger, more resilient organizations. Let’s grow and lead the way—side by side.