Did you know cyberattacks and regulatory fines have soared to record highs in 2025 and 2026? As cyber threats grow more advanced and regulations become stricter, cyber risk management is now an urgent priority for every business.
Managing risk across cloud platforms, AI systems, and countless third-party partners can feel overwhelming. The landscape is changing fast, and the stakes for business continuity and reputation have never been higher.
The good news? With a unified, proactive approach, you can turn cyber risk management into a powerful business enabler. Ready to master the essential steps and tools to protect your organization in 2026? Let’s get started together.
Understanding Cyber Risk Management in 2026
Cyber risk management in 2026 is not just a technical discipline, it is a core part of how organizations thrive and stay resilient in a digital-first world. Let us break down what it really means, why it is more urgent than ever, and how teams can work together to manage risk effectively.
Defining Cyber Risk Management for the Modern Era
Cyber risk management is the ongoing process of identifying, analyzing, prioritizing, and addressing cyber risks that can threaten your organization. It is deeply woven into enterprise risk management and business strategy, helping teams make informed decisions about technology and data.
Since cyber risk can never be completely eliminated, the goal is to manage it within agreed-upon boundaries. Key stakeholders include IT, security, compliance, legal, HR, and executive leadership. For example, a healthcare breach now averages 10.1 million USD in damages, while hospitality incurs about 2.9 million USD, showing how sector and strategy affect exposure.
Modern organizations are shifting from siloed, reactive approaches to unified, organization-wide responsibility. Digital transformation and remote work have expanded the risk footprint, making cyber risk management a business enabler, not just a technical necessity. For a detailed foundation, see the Cybersecurity Risk Management Guide.
The Current Threat Landscape and Drivers for Change
The cyber risk management landscape in 2026 is shaped by a surge in cloud adoption, IoT expansion, and AI-driven attacks. Over 2,000 new vulnerabilities are added each month to the NIST National Vulnerability Database, keeping defenders on their toes.
Organizations now share data with an average of 583 vendors, increasing supply chain and third-party risks. Regulations like NIS2, GDPR, PCI DSS, and HIPAA demand new levels of oversight and accountability. High-profile breaches have made headlines, showing the cost of gaps in protection.
Remote and hybrid work have stretched attack surfaces, while boards face new expectations for direct involvement. The pace of change and complexity requires organizations to be agile and vigilant.
Why Cyber Risk Management Matters in 2026
Business continuity and reputation protection are the top reasons why cyber risk management is a boardroom priority. The cost of non-compliance, including regulatory penalties, can be staggering. Customers are more likely to trust businesses that prioritize security, giving organizations a competitive edge.
Because it is impossible to secure every asset, risk-based prioritization is critical. In one real-world case, strong risk management enabled a company to recover rapidly from a ransomware attack, minimizing downtime and losses.
Cyber insurance is increasingly used to transfer residual risk, but it is no replacement for robust controls. Data-driven decision-making helps leaders allocate resources where they matter most.
Key Principles and Evolving Best Practices
Cyber risk management is a continuous, iterative process, not a one-time project. Aligning risk appetite with business objectives ensures security investments support strategic goals.
Collaboration across business units creates a holistic view of risk. Leading frameworks like NIST CSF and ISO 27001 provide structure for policies and controls. Clear documentation and open communication are essential for audits and compliance.
Embedding risk management into digital transformation initiatives is now standard. Teams are shifting toward intelligence-led, proactive security strategies, making cyber risk management a driver of resilience and confidence.
Step-by-Step Cyber Risk Management Process for 2026
Every organization needs a structured approach to cyber risk management in 2026. By following a clear, step-by-step process, we can build resilience, maintain compliance, and respond confidently to evolving threats. Let’s explore each phase and see how these steps work together as a continuous cycle for business protection.
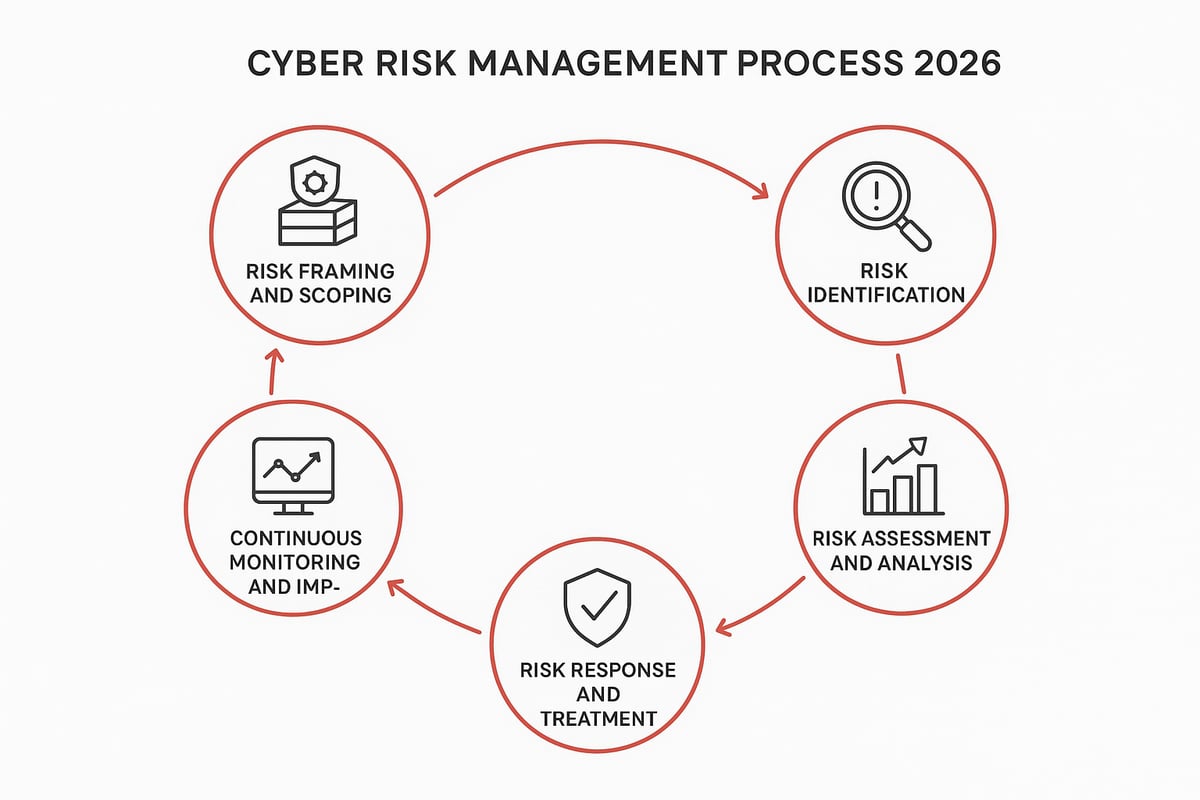
Step 1: Risk Framing and Scoping
The first step in cyber risk management is defining the boundaries of your process. Start by identifying the assets, systems, and data that matter most. Assess their criticality to business operations. Clarify what types of threats you’re most concerned about, such as cyberattacks, insider risks, or regulatory changes.
Next, align your process with organizational priorities and risk tolerance. Understand any legal, regulatory, or contractual obligations that shape your approach. For example, a fintech company must consider DORA and NIS2 requirements when framing risk.
Set clear limits on what’s included in your scope and document who is involved. This ensures that cyber risk management efforts stay focused and aligned with business goals. Collaboration across departments from the start helps drive a unified strategy.
Step 2: Risk Identification
With your scope in place, it’s time to identify potential risks. Catalog threats like phishing, ransomware, human error, and third-party vulnerabilities. Look for technical weaknesses, such as misconfigured cloud storage or outdated software. Use threat intelligence and SIEM logs to uncover both internal and external risks.
Engage cross-functional teams, including IT, security, HR, and legal, to ensure no risk is overlooked. Map identified threats to business processes and critical assets. For example, discovering a misconfigured cloud bucket containing sensitive data can highlight significant exposure.
Effective cyber risk management relies on a thorough inventory of vulnerabilities and threats. This foundation allows you to prioritize and address the most pressing risks first, improving overall protection and awareness.
Step 3: Risk Assessment and Analysis
Now, assess each identified risk for its likelihood and potential impact on your business. Use both qualitative judgment and quantitative data, such as historical incidents and industry benchmarks. Rank risks by severity in a risk register, focusing on those that could disrupt operations or damage reputation.
Conduct a business impact analysis (BIA) on your most valuable assets. For structure, consider frameworks like NIST SP 800-30. Involve senior leaders to set thresholds for acceptable risk. For practical support, explore Cyber Risk Assessment Tools that simplify data collection and scoring.
Cyber risk management at this stage is about making informed decisions. Prioritization ensures your resources go where they matter most, helping you stay resilient even as threats evolve.
Step 4: Risk Response and Treatment
Once you’ve prioritized the risks, decide how to respond. Options include mitigation (reducing risk with controls), remediation (fixing vulnerabilities), transfer (using insurance or contracts), or acceptance (for low-impact risks). Implement technical controls like MFA or privileged access management, and develop incident response plans.
Test your response plans regularly to ensure readiness. For transferred risks, such as those offset by cyber insurance, document the terms and ongoing requirements. Remediate vulnerabilities through patching, configuration changes, or retiring obsolete assets.
Cyber risk management documentation is critical here for compliance. Keep records of every action and decision. This transparency supports audits and regulatory reviews, building trust with stakeholders.
Step 5: Continuous Monitoring and Improvement
Cyber risk management is never a one-time event. Continuously monitor your controls and risk environment. Use real-time analytics, automated alerts, and threat intelligence feeds to spot new risks or weaknesses as they arise.
Regularly review and update your risk assessments and policies in response to changes in technology or the threat landscape. Adjust controls when new vulnerabilities are disclosed or when regulations change. Encourage a culture of ongoing learning and improvement, where feedback leads to stronger defenses.
By embedding continuous monitoring into daily operations, you ensure that cyber risk management adapts quickly, keeping your organization resilient in the face of uncertainty.
Step 6: Reporting, Communication, and Documentation
The final step is clear communication. Report risk status and key decisions to stakeholders, leadership, and the board. Use dashboards and visualizations to make complex information accessible. Share lessons learned from incidents and near-misses, fostering transparency and accountability.
Maintain detailed documentation for audits and regulatory reviews. Align reporting with business objectives and compliance needs. For example, use risk reports to inform strategic decisions at the board level.
Cyber risk management thrives when everyone understands their role. Open communication builds a culture of trust and shared responsibility, keeping your organization prepared and confident.
Frameworks, Standards, and Compliance Requirements
Adopting the right frameworks and standards is the backbone of effective cyber risk management. In 2026, organizations face more complexity than ever, with evolving threats and tightening regulations. Let’s explore how frameworks, compliance, and governance come together to build a resilient security posture for your business.
Overview of Leading Cyber Risk Management Frameworks
Navigating the maze of cyber risk management frameworks can feel overwhelming, but the right choice brings clarity and structure. The most widely adopted frameworks include NIST Cybersecurity Framework (CSF), ISO/IEC 27001, and NIST’s SP 800-30 and 800-53. Each framework offers a unique approach to identifying, assessing, and addressing risks.
Sector-specific mandates like PCI DSS, HIPAA, GDPR, DORA, and NIS2 bring additional requirements for certain industries. Comparing frameworks helps organizations select the best fit for their needs. For example, NIST CSF is popular among US federal agencies, while ISO 27001 is favored for global operations.
For a thorough comparison and in-depth reviews, check out the Best Cybersecurity Frameworks resource. Choosing the right framework is a foundational step in cyber risk management, ensuring audit readiness and a strong compliance baseline.
Navigating Regulatory Complexity in 2026
The regulatory environment for cyber risk management is more demanding than ever. Organizations must keep pace with a growing patchwork of global and regional regulations. This complexity is amplified by new rules targeting third-party and supply chain risks, as well as stricter enforcement.
Non-compliance can lead to steep fines and reputational damage. The expanded scope of the NIS2 Directive, for instance, brings new reporting obligations and accountability standards. Mapping compliance requirements to your business processes is essential for maintaining control.
Compliance teams now play a pivotal role in cyber risk management. Their efforts integrate regulatory needs into daily operations, making sure security controls align with evolving laws and standards.
Building a Risk Management Program for Compliance
Turning frameworks into action is the heart of an effective cyber risk management program. Start by developing policies, selecting controls, and documenting your approach. Regular compliance assessments and gap analyses help identify and fix weaknesses.
For example, using NIST SP 800-53 controls can streamline FedRAMP compliance for cloud service providers. Training and awareness for all employees ensure that everyone understands their role in protecting the organization. Automation tools can simplify tracking compliance tasks and reduce manual errors.
Vendor and third-party compliance alignment is also vital. A well-built program gives you confidence that your cyber risk management efforts are meeting both internal and external expectations.
The Role of Internal Audit and Governance
Internal audit is a key ally in cyber risk management. Auditors verify that risk management activities are effective and consistent with policies. Board-level oversight ensures risk appetite is set appropriately and that governance structures support accountability.
For instance, a failed tabletop exercise can drive meaningful improvements when audit findings are acted upon. Continuous review of policies and controls keeps your organization agile amid regulatory change.
Effective governance means aligning risk management with business strategy and reporting to regulators and stakeholders. This transparency builds trust and demonstrates a commitment to protecting critical assets.
Emerging Trends in Frameworks and Standards
Cyber risk management frameworks are rapidly evolving to address new technologies and threats. AI governance and ethical considerations are increasingly included, as are expanded controls for cloud, IoT, and OT environments.
Organizations are shifting toward continuous compliance and real-time monitoring, adopting principles like zero trust for enhanced security. Industry collaboration is leading to more standardized risk metrics and shared best practices.
Looking ahead, agility in updating frameworks and anticipating regulatory changes, such as the AI Act, will be crucial. Staying proactive ensures your cyber risk management program remains resilient and future-ready.
Critical Capabilities for Effective Cyber Risk Management
Staying ahead in cyber risk management takes more than just technology. It’s about empowering people, creating smart processes, and making the right investments. Let’s explore the essential capabilities every organization needs to build resilience, stay compliant, and adapt to the threats of 2026.
Essential People, Processes, and Technology
A successful cyber risk management program starts with the right mix of people, processes, and technology. Building cross-functional teams ensures that IT, security, compliance, and business leaders all share responsibility. Everyone should know their role, from risk owners to incident responders.
Process standardization is key. Consistent steps for risk identification, assessment, and response help avoid gaps. Ongoing training keeps teams prepared for new threats. Technology, like automation platforms and SIEM tools, boosts efficiency and ensures your cyber risk management strategy scales with your business.
- Cross-functional teams unite expertise
- Standardized processes ensure consistency
- Automation minimizes manual errors
By combining these elements, organizations can make cyber risk management a seamless part of daily operations.
The Power of Threat Intelligence and Analytics
Threat intelligence and analytics are game changers for proactive cyber risk management. Real-time data from both internal and external sources help organizations spot trends and emerging risks before they escalate. Integrating threat feeds with analytics platforms allows security teams to prioritize the most pressing threats.
AI and machine learning are increasingly critical, especially with the rise of automated attacks. According to recent reports, AI-driven cyberattacks surge is making it essential to use advanced analytics for defense. Dashboards and visual metrics keep everyone informed, enabling data-driven decisions for resource allocation.
- Real-time threat feeds for early warning
- Analytics highlight risk trends and priorities
- AI tools improve detection and response
With these capabilities, cyber risk management becomes more agile and effective.
Managing Third-Party and Supply Chain Risk
Third-party and supply chain risk is now a top priority in cyber risk management. Organizations often share data with hundreds of vendors, making it vital to assess and monitor each partner’s security posture. Vendor risk assessments, due diligence, and contract clauses for data protection are must-haves.
Continuous monitoring ensures that any changes in a vendor’s environment are quickly identified. Frameworks like NIST and ISO 27036 offer structured approaches for managing these risks. Clear communication with partners sets expectations and ensures accountability.
- Assess vendors before onboarding
- Monitor third-party security continuously
- Include incident reporting in contracts
Managing these relationships well helps protect your organization from cascading risks.
Incident Response and Business Continuity Planning
Incident response is at the heart of cyber risk management. Every organization needs robust plans to detect, contain, and recover from cyber incidents. Regular tabletop exercises and simulations ensure teams are ready when real threats strike.
Integrating response plans with business continuity and disaster recovery strategies minimizes downtime. For practical guidance, explore this Incident Response and Disaster Recovery guide, which covers planning essentials. After every incident, review lessons learned and update plans to close gaps.
- Develop and test incident response plans
- Integrate with business continuity procedures
- Review and improve after incidents
A prepared team can turn a crisis into an opportunity for growth.
Measuring and Improving Cyber Risk Maturity
Measuring your organization’s cyber risk management maturity is crucial for continuous improvement. Maturity models, like CMMI or NIST, provide benchmarks to assess where you stand and what steps to take next. Regular assessments help identify gaps and set priorities for investment.
Key performance indicators (KPIs) and metrics track progress over time. Benchmarking against industry peers highlights strengths and areas for growth. Embedding a culture of accountability ensures that everyone is invested in advancing cyber risk management maturity.
- Use maturity models for benchmarking
- Track KPIs to measure improvement
- Foster a culture of learning and accountability
By focusing on maturity, organizations build lasting resilience and stay ahead of evolving threats.
Practical Guidance and Real-World Best Practices
In 2026, putting cyber risk management into practice means more than just ticking boxes. It is about building habits, routines, and mindsets that make resilience part of your organization’s DNA. Let us explore best practices together, breaking them down into practical, actionable steps you can start using today.
Building a Unified, Organization-Wide Risk Management Culture
A strong cyber risk management culture does not happen by accident. It starts with breaking down silos between IT, security, compliance, and business teams. When everyone feels responsible, the organization becomes much more resilient.
Leadership support is key. Leaders who visibly champion cyber risk management inspire others to follow. Forming cross-functional risk committees encourages collaboration and ensures decisions reflect diverse perspectives.
- Embed risk management into strategic planning
- Offer ongoing education at all levels
- Recognize and reward risk-aware behaviors
Feedback loops keep the culture evolving. When teams share lessons learned, everyone grows stronger together.
Data-Driven Prioritization and Resource Allocation
Not all risks are created equal. Cyber risk management thrives when organizations use data to guide decisions. Business impact analysis helps you invest in controls that protect your most vital assets.
Leverage real-time threat intelligence to prioritize responses. This approach helps avoid overspending on low-value controls while ensuring critical gaps are addressed.
- Use scenario planning for high-impact risks
- Balance security with operational efficiency
- Make risk reporting transparent and accessible
When data drives your cyber risk management, leaders gain confidence that resources are focused where they matter most.
Leveraging Automation and Technology for Scale
As digital environments grow, manual processes struggle to keep up. Cyber risk management benefits greatly from automation, which streamlines assessments and compliance checks.
Integrate security tools with GRC platforms for real-time visibility. Automation reduces manual errors and frees up teams to focus on strategy. For more on how leading organizations are scaling defenses, see the 2026 cybersecurity trends.
- Automate monitoring for cloud misconfigurations
- Orchestrate incident response to speed recovery
- Continuously adapt to new threats with smart tech
Investing in automation keeps your cyber risk management program agile and future-ready.
Case Studies: Lessons from Recent Breaches and Successes
Learning from real-world incidents is essential for cyber risk management maturity. For example, a major 2025 supply chain attack showed how a single vendor breach can disrupt operations across industries.
Conversely, organizations with proactive risk management responded swiftly to ransomware, containing threats and minimizing downtime. After regulatory investigations, some firms improved by adopting NIST CSF or ISO 27001, strengthening their defenses.
- Share incident outcomes across teams
- Review and update plans after each event
- Maintain open communication during crises
Continuous improvement, driven by lived experience, is at the heart of effective cyber risk management.
LarsBirkeland.com: Practical Cyber Risk Leadership and Resources
LarsBirkeland.com is a trusted source for actionable cyber risk management resources. The site offers step-by-step guides, checklists, and frameworks developed from years of hands-on CISO experience.
You will find real-world stories that bridge technical know-how with strategic action. The CISO LaunchPad community provides peer support and knowledge sharing, making cyber risk management less overwhelming.
- Access vendor-neutral templates and advice
- Stay updated on new regulations and best practices
- Benefit from leadership lessons tailored to your challenges
Whether you are a CISO, manager, or small business leader, LarsBirkeland.com brings clarity and confidence to your cyber risk management journey.
Actionable Checklists and Templates for 2026
Practical tools make cyber risk management more effective and repeatable. Start with a 2026 cyber risk management checklist to ensure no critical steps are missed.
- Use a risk register and assessment template
- Outline your incident response plan clearly
- Deploy third-party risk questionnaires for vendors
Map compliance requirements with easy-to-use tools covering NIS2, GDPR, and industry mandates. Track progress with a metrics dashboard and regularly assess your maturity.
With these resources, you can drive continuous improvement and keep your cyber risk management program on track.
As we wrap up this essential guide, remember that navigating cyber risk management in 2026 doesn’t have to be overwhelming or lonely.
We’re all learning, adapting, and facing new challenges together, whether it’s keeping up with evolving threats, making smart decisions under pressure, or building a resilient security culture that truly sticks.
If you’re ready for real-world support, fresh perspectives, and a place to connect with peers who “get it,” I’d love for you to Join CISO Launchpad. Let’s grow, share, and build stronger organizations—side by side.








