Did you know that in 2026, the average cost of a network breach soared past $6 million, with attack frequency reaching an all-time high? As organizations race toward digital transformation, the pressure to strengthen network security management has never been greater.
Every day, new threats emerge and the risks multiply for businesses of all sizes. This guide is here to help you navigate the complex world of network security management, offering clear steps and expert insights for protecting your organization.
We’ll explore the shifting threat landscape, core principles, proven frameworks, essential technologies, and future-proofing strategies. Whether you’re facing ransomware or managing hybrid cloud environments, you’ll find practical solutions to today’s toughest challenges.
Curious how to build lasting defenses and stay ahead of attackers? Let’s dive in and transform your approach to network security management together.
The Evolving Network Security Landscape in 2026
The world of network security management is changing rapidly as technology evolves and attackers become more sophisticated. In 2026, organizations face a complex mix of threats, regulations, and operational challenges as they work to protect their digital environments. Let’s explore what’s shaping the current landscape and how we can respond.
Major Threats and Attack Vectors
In 2026, network security management is challenged by a surge in ransomware-as-a-service operations and sophisticated supply chain attacks. AI-driven phishing campaigns use deepfake technology and automated social engineering to bypass traditional defenses. Recent statistics reveal that global ransomware incidents increased by 35 percent in the past year, costing businesses billions.
The rise of hybrid workforces and the explosion of IoT devices have expanded the attack surface significantly. High-profile breaches in 2025 and 2026, such as those impacting major financial institutions and healthcare providers, highlight a shift from random attacks to highly targeted campaigns. As detailed in Cybersecurity trends and predictions for 2026, identity systems and supply chains are now prime targets, demanding a proactive approach to network security management.
Regulatory and Compliance Pressures
Compliance is now a driving force in network security management. New regulations, such as NIS2 across the EU and updated CISA directives in the US, have raised the bar for data protection and incident reporting. Enhanced GDPR rules put additional focus on cross-border data flows and user privacy.
Organizations that fail to comply face steeper penalties, with fines reaching historic levels in 2026. Recent examples include energy and telecom companies that were sanctioned for not promptly disclosing breaches or securing critical infrastructure. These pressures make compliance-driven security a top priority for effective network security management.
Network Complexity and Digital Transformation
Digital transformation has reshaped network security management by introducing cloud adoption, edge computing, and a sprawl of SaaS applications. These trends have multiplied the number of endpoints and data paths, making it harder to maintain visibility and control.
Industry reports show that network complexity has grown by over 40 percent since 2024, especially in organizations running multi-cloud or hybrid environments. Security teams now struggle to monitor assets consistently and enforce policies across diverse platforms. Unified visibility and centralized management are becoming essential for robust network security management.
The Role of AI and Automation in Threats and Defenses
AI and automation have changed both the threat landscape and defense strategies in network security management. Attackers now use AI to craft convincing phishing emails, automate vulnerability scanning, and orchestrate large-scale attacks with minimal human input.
Defenders, in turn, leverage AI-powered security tools for faster threat detection, automated incident response, and predictive analytics. Industry data shows that 70 percent of organizations deployed AI-based solutions in their security operations centers by 2026. Security teams need new skills to manage these technologies and must stay agile as AI continues to evolve within network security management.
Core Principles of Effective Network Security Management
Building a resilient approach to network security management means embracing a few foundational principles. These principles help organizations stay ahead of threats, adapt to evolving risks, and foster a proactive mindset across teams.
Defense-in-Depth and Zero Trust Architectures
Defense-in-depth and Zero Trust are at the heart of modern network security management. Defense-in-depth means layering security controls throughout your network, not just at the perimeter. This makes it much harder for attackers to move laterally if they breach one layer.
Zero Trust takes this further by assuming no user or device should be trusted by default, even inside the network. In 2026, organizations are rapidly adopting Zero Trust models, guided by frameworks like NIST SP 800-207. Real-world examples include large enterprises segmenting networks and requiring continuous authentication.
If you want to dive deeper into the essentials, check out this overview of Network Security Fundamentals.
Risk Assessment and Asset Inventory
Continuous risk assessment is a cornerstone of effective network security management. You can’t protect what you can’t see, so mapping out every asset, including IoT devices and shadow IT, is critical. Start by automating asset discovery and keep inventories up to date.
Industry reports show that asset visibility gaps often lead to breaches. Use proven asset management tools and methodologies to close these gaps. Regularly reviewing and updating your asset inventory ensures you always know what needs protection.
Policy Development and Access Control
Dynamic, context-aware access control policies are vital for network security management in 2026. Static policies no longer suffice. Instead, organizations are embracing adaptive policy enforcement that responds to changing conditions.
Identity and access management (IAM) and privileged access management (PAM) play central roles here. By adopting effective frameworks and automating policy updates, you can stay ahead of evolving threats. The shift to real-time, adaptive controls helps keep your network secure as users and devices come and go.
Security Monitoring and Incident Response
Real-time monitoring and rapid incident response are non-negotiable in network security management. Integrating solutions like SIEM, SOAR, and NDR gives you comprehensive visibility and the ability to act fast.
Recent case studies show that organizations with robust monitoring and clear response plans can dramatically reduce the impact of breaches. Track key metrics like detection and response times to measure your program’s effectiveness. Continuous improvement and swift action help limit damage and maintain trust.
Strategic Frameworks and Governance for 2026
Building a resilient network security management program starts with strategic frameworks and robust governance. In 2026, organizations face a fast-changing landscape, so aligning leadership, policies, and risk strategies is essential for staying ahead of threats and ensuring compliance.
Establishing Security Governance Structures
Effective network security management begins with strong governance. Organizations are forming dedicated security committees and empowering CISOs to oversee risk and compliance. Cross-functional teams help bridge IT, security, and business units, creating a security-first culture.
Executive buy-in is crucial. When leadership prioritizes network security management, it sets the tone across the company. According to Security Governance in Organizations, clear structures and defined roles are foundational for success.
Best practices include regular board-level reviews, transparent communication, and accountability at every level. These governance structures provide the backbone for network security management in complex, evolving environments.
Developing and Enforcing Security Policies
Developing adaptive policies is core to network security management. Policies should be living documents, updated as threats and technologies change. In 2026, organizations are shifting to policy-as-code, automating enforcement across hybrid and cloud environments.
Automation reduces the risk of manual errors and ensures consistency. Regular policy reviews help identify gaps and outdated controls. Studies show that unclear or unenforced policies remain a leading cause of breaches.
Effective network security management means policies are actionable, well-communicated, and enforced through continuous monitoring. This approach helps organizations remain agile and compliant.
Risk Management and Business Alignment
Aligning network security management with business goals is more important than ever. Modern frameworks like ISO 27001 and NIST CSF provide structured approaches for identifying and prioritizing risks. These frameworks guide leaders in making informed decisions that balance security needs with organizational objectives.
Regular risk assessments uncover new threats and inform investment in network security management. By integrating risk management into business planning, organizations can allocate resources effectively and respond quickly to emerging challenges.
Clear reporting and ongoing analysis ensure that security strategies evolve alongside the business, supporting growth while minimizing risk.
Training, Awareness, and Human Factors
People remain the heart of network security management. In 2026, user errors and social engineering are still among the top causes of breaches. To combat this, organizations invest in engaging training programs, using gamification and real-time phishing simulations.
Just-in-time training delivers security awareness at critical moments, boosting retention and empowering users. Metrics show that regular, interactive education significantly reduces incidents linked to human factors.
A culture of continuous learning, supported by leadership, ensures everyone understands their role in network security management and feels confident to act.
Third-Party and Supply Chain Risk Management
Managing third-party and supply chain risks is now a non-negotiable part of network security management. As organizations depend more on vendors and partners, attackers increasingly target these relationships to gain access.
Robust due diligence, regular access reviews, and continuous monitoring of third-party connections are key. Recent high-profile supply chain attacks highlight the need for proactive risk assessments and transparent communication with partners.
Frameworks and tools designed for vendor risk management help organizations safeguard their network security management efforts, reducing exposure and ensuring compliance in an interconnected world.
Key Technologies and Tools Shaping Network Security
Today’s network security management relies on a powerful set of technologies that keep pace with evolving threats and business needs. Organizations are adopting smarter, more integrated tools to protect their digital assets and support hybrid work, cloud adoption, and IoT expansion. Let’s explore the essential technologies shaping the future of network security management.
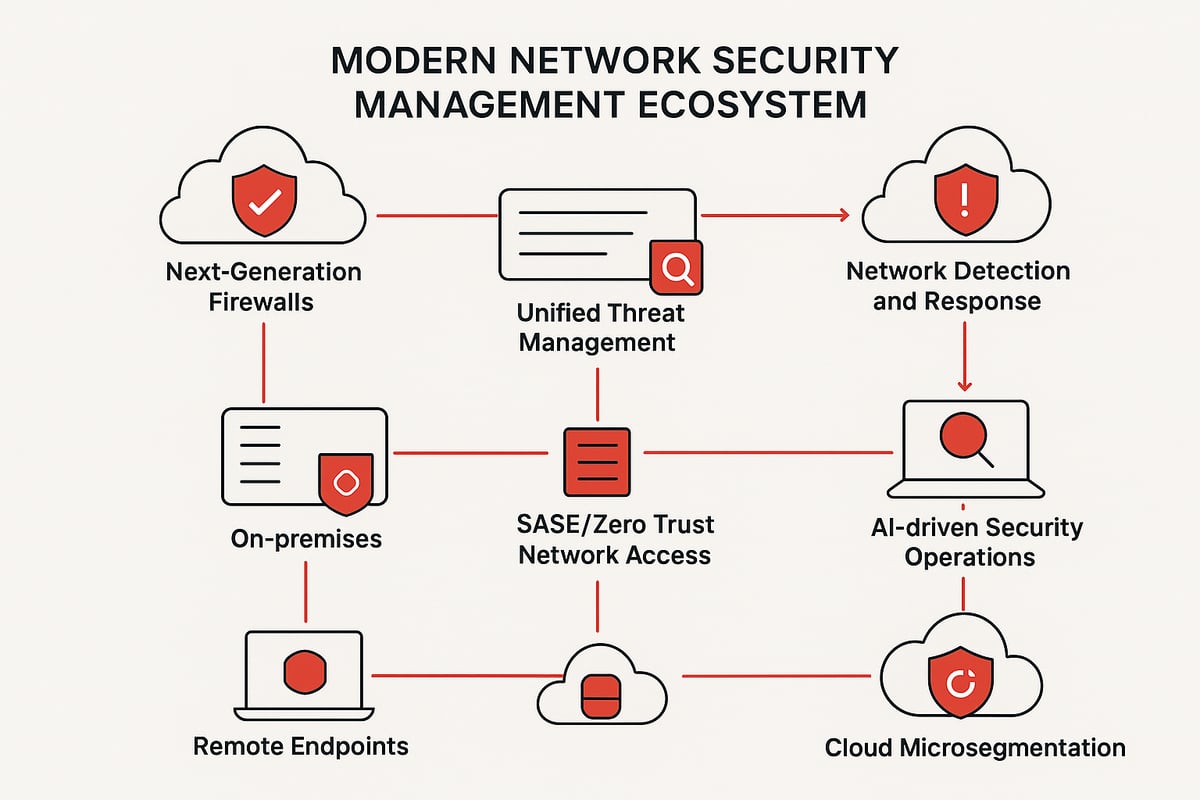
Next-Generation Firewalls and Unified Threat Management
The backbone of network security management in 2026 is the next-generation firewall (NGFW). Unlike traditional firewalls, NGFWs offer deep packet inspection, application-level control, and built-in threat intelligence. These features help organizations detect and block sophisticated attacks at the perimeter and within the network.
Unified Threat Management (UTM) platforms combine firewall, intrusion prevention, antivirus, and content filtering into a single solution. This integration streamlines administration and enhances security posture, especially in hybrid and multi-cloud environments. According to recent industry reports, over 80% of enterprises now deploy NGFWs or UTM solutions for comprehensive protection.
For a detailed look at these evolving tools, visit Network Security Solutions and Tools.
Network Detection and Response (NDR)
Network Detection and Response (NDR) has become a crucial element of network security management. NDR platforms leverage machine learning and behavioral analytics to identify abnormal activity that might indicate a breach or insider threat.
NDR tools provide continuous visibility across cloud, on-premises, and remote environments. They excel at detecting advanced persistent threats that bypass traditional defenses. Leading organizations use NDR to shorten detection and response times, reducing the window of exposure.
With network security management growing more complex, NDR’s ability to deliver actionable insights and automate threat hunting is invaluable. Early breach detection can save millions in potential losses.
Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA)
SASE and Zero Trust Network Access (ZTNA) are transforming how organizations approach network security management for remote and hybrid workforces. SASE combines networking and security functions in a single cloud-delivered service, offering secure access regardless of user location.
ZTNA enforces strict identity verification, granting access only to authorized users and devices. Integration with SD-WAN and cloud platforms enables seamless, secure connectivity. Industry analysts predict that by 2026, over 60% of organizations will have adopted SASE or ZTNA architectures.
This shift helps organizations enforce consistent security policies and reduce attack surfaces across distributed environments, advancing the maturity of network security management.
AI and Automation in Security Operations
AI and automation are revolutionizing network security management by streamlining threat detection, investigation, and response. Security Operations Centers (SOCs) now use AI-powered tools for alert triage, automated incident response, and predictive analytics.
Automated playbooks handle repetitive tasks, allowing security teams to focus on complex threats. Studies show that AI adoption can improve SOC efficiency by up to 40%, reducing mean time to detect and respond to incidents.
Despite these gains, challenges remain—organizations must ensure that AI-driven tools are properly tuned and monitored. Still, the future of network security management will undoubtedly be shaped by intelligent automation.
Cloud Security and Microsegmentation
With the explosive growth of cloud-native applications, cloud security and microsegmentation are now central to network security management. Cloud environments introduce unique risks, including misconfigurations and lateral movement by attackers.
Microsegmentation divides the network into isolated segments, limiting the impact if a breach occurs. Security teams apply granular policies to workloads, containers, and virtual machines. Industry reports highlight that organizations using microsegmentation see a significant drop in the spread of attacks.
As cloud adoption accelerates, robust network security management depends on these advanced strategies to safeguard sensitive data and maintain business continuity.
Step-by-Step Guide to Building a Resilient Network Security Program
Building a strong foundation for network security management in 2026 is not just about technology, but about creating a culture of resilience. Let’s break down the process into actionable steps that anyone can follow, no matter the size of your organization. Each step below will help you move closer to a safer, more reliable network.
Step 1: Assess and Map Your Network
Start by discovering every device, application, and data flow within your network. This is the bedrock of network security management. Use automated asset discovery tools to uncover hidden devices, shadow IT, and IoT endpoints.
Map out how data moves through your environment. Document dependencies and identify what systems are business critical. Create a living inventory that is updated regularly, not just once a year.
Common pitfalls include missing devices or outdated inventories. To avoid these, schedule regular scans and involve both IT and business units. This clarity gives you the visibility needed to protect what matters most.
Step 2: Identify and Prioritize Risks
With your environment mapped, the next step in network security management is to identify and rank risks. Use methodologies like vulnerability assessments, penetration testing, and threat intelligence feeds to spot weaknesses.
Create a risk ranking matrix based on likelihood and impact. Review this matrix often, as threats evolve quickly. Include risks from new technologies, third-party vendors, and remote work setups.
Continuous risk review is essential. Set up processes to track remediation and ensure that critical vulnerabilities are addressed first. This proactive approach makes your defenses much more robust.
Step 3: Develop Security Policies and Controls
Effective network security management requires tailored security policies. Draft policies that address your unique risks and compliance needs. Focus on areas like acceptable use, remote access, and incident response.
Select controls that match your risk profile, including both technical (firewalls, encryption) and administrative (training, audits) measures. Reference established frameworks to guide your policy development.
Policies should be living documents. Review them regularly and update as your environment or threat landscape changes. Clear communication helps ensure everyone understands their role in keeping the network secure.
Step 4: Implement Layered Defenses and Zero Trust
A multi-layered approach is key for modern network security management. Deploy defenses at the network, endpoint, and application levels. Embrace the Zero Trust model, which means never automatically trusting any user or device.
Segment your network to limit the blast radius of attacks. Apply least privilege principles, granting users and systems only the access they truly need. Continuous verification ensures only authorized entities can connect.
For more on how organizations are embracing this approach, check out the latest Zero Trust Network Access adoption statistics. Real-world examples show that Zero Trust can dramatically reduce breach risks and improve overall resilience.
Step 5: Deploy Monitoring, Detection, and Response Capabilities
You cannot protect what you cannot see. Integrate SIEM, SOAR, and Network Detection and Response solutions to create a unified view of your environment. Real-time monitoring is a cornerstone of effective network security management.
Develop a clear incident response plan, including escalation paths and communication protocols. Use metrics such as Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) to measure and improve your processes.
For hands-on guidance, explore these Network Security Monitoring Best Practices. Staying vigilant allows you to spot threats early and respond before they escalate.
Step 6: Test, Train, and Continuously Improve
Resilience is not a destination, but an ongoing journey. Regularly test your defenses with penetration tests, red teaming, and tabletop exercises. These activities ensure your network security management program is ready for real-world threats.
Invest in ongoing staff training and awareness programs. Learn from incidents through post-event reviews and always seek opportunities to improve. Adopting continuous improvement frameworks helps you stay ahead of attackers.
Remember, building a resilient security posture is a team effort. Together, we can adapt and thrive in an ever-changing digital landscape.
Best Practices and Future-Proofing Network Security Management
Staying ahead in network security management means not just reacting to threats, but actively shaping your defenses for the future. Let’s explore the best practices that help organizations thrive in this ever-changing cybersecurity landscape.
Proactive Threat Hunting and Intelligence Integration
Proactive threat hunting transforms network security management from a passive defense to an active shield. Instead of waiting for alerts, teams seek out hidden threats by analyzing unusual patterns and network behaviors.
Integrating threat intelligence feeds empowers defenders to recognize emerging tactics before they escalate. Many organizations now combine automated tools with human expertise to reduce dwell time, the period attackers remain undetected. Industry studies show that proactive hunting can cut average dwell time by over 30 percent, strengthening incident prevention.
By making threat hunting and intelligence part of your regular routine, you create a living, evolving defense system. This approach keeps your network security management sharp and ready for whatever comes next.
Security Automation and Orchestration
Security automation is revolutionizing how teams approach network security management. By automating repetitive tasks, organizations free up skilled staff to focus on higher-level analysis and strategy.
Platforms like Security Orchestration, Automation, and Response (SOAR) streamline workflows, from alert triage to incident response. Automated playbooks ensure consistent, rapid actions, reducing human error and response times. According to recent research, companies using AI-driven automation experience up to 50 percent faster threat remediation.
To explore more on this topic, check out AI-driven security automation trends. Embracing automation not only boosts efficiency but also helps scale network security management as your digital footprint grows.
Measuring and Reporting Security Effectiveness
Effective network security management relies on clear metrics and transparent reporting. Key performance indicators like Mean Time to Detect (MTTD), Mean Time to Respond (MTTR), and compliance rates provide real insight into your security posture.
Regularly sharing these results with stakeholders builds trust and demonstrates ongoing improvement. Interactive dashboards make it easy to visualize trends and identify gaps quickly. Benchmarking against industry standards helps teams understand where they stand and where to improve.
By measuring what matters and reporting it clearly, organizations can make better decisions and keep their network security management aligned with business goals.
Adapting to Emerging Technologies and Threats
The pace of technological change means network security management must be agile. Teams need to monitor trends like 5G, IoT, and the rise of quantum computing, adapting controls as new challenges arise.
One crucial innovation is quantum-safe encryption. With quantum computers on the horizon, traditional cryptography faces new risks. Organizations should follow the latest post-quantum encryption developments to stay ahead of threats.
Encouraging a culture of continuous learning ensures your team is always ready to embrace new technologies and defend against evolving tactics in network security management.
Building a Security-First Organizational Culture
A security-first culture is the foundation of resilient network security management. Leadership must prioritize security in every business decision, setting the tone for the entire organization.
Collaboration between IT, security, and business units fosters shared responsibility. Regular training, open communication, and recognition of positive security behaviors help embed security into daily routines. Data shows that companies with strong security cultures experience fewer incidents and recover faster when issues arise.
Building this culture is not a one-time effort, but a continuous journey. When everyone plays a role, network security management becomes a true team sport.
We’ve just covered a lot—real-world threats, proven frameworks, and practical steps to help you lead the way in network security management for 2026. But you don’t have to do this alone.
If you’re looking for a space where CISOs, IT leaders, and security pros share real stories, hard-won lessons, and actionable ideas, why not join us? The Join Cyber Launchpad Community is a welcoming group where we help each other grow, solve real challenges, and stay ahead in a fast-moving landscape. I’d love to see you there!