In 2026, cyber threats are evolving at an unprecedented pace. Protecting your organization is not just an IT task—it is an absolute necessity. The stakes are higher, and network security solutions are now central to every business strategy.
This essential guide helps you make sense of the latest network security solutions. We will uncover the biggest challenges facing networks in 2026, reveal the most effective tools for defense, and give you a practical, step-by-step path to stronger protection.
Are you ready to take charge and future-proof your organization? Let us dive into the world of network security solutions together.
The 2026 Network Security Landscape: Trends and Threats
In 2026, the digital world feels like a bustling city that never sleeps. Every organization, big or small, faces an ever-changing maze of risks and opportunities. To help us all stay ahead, let’s explore the shifting landscape, the latest threats, and why network security solutions are more vital than ever.
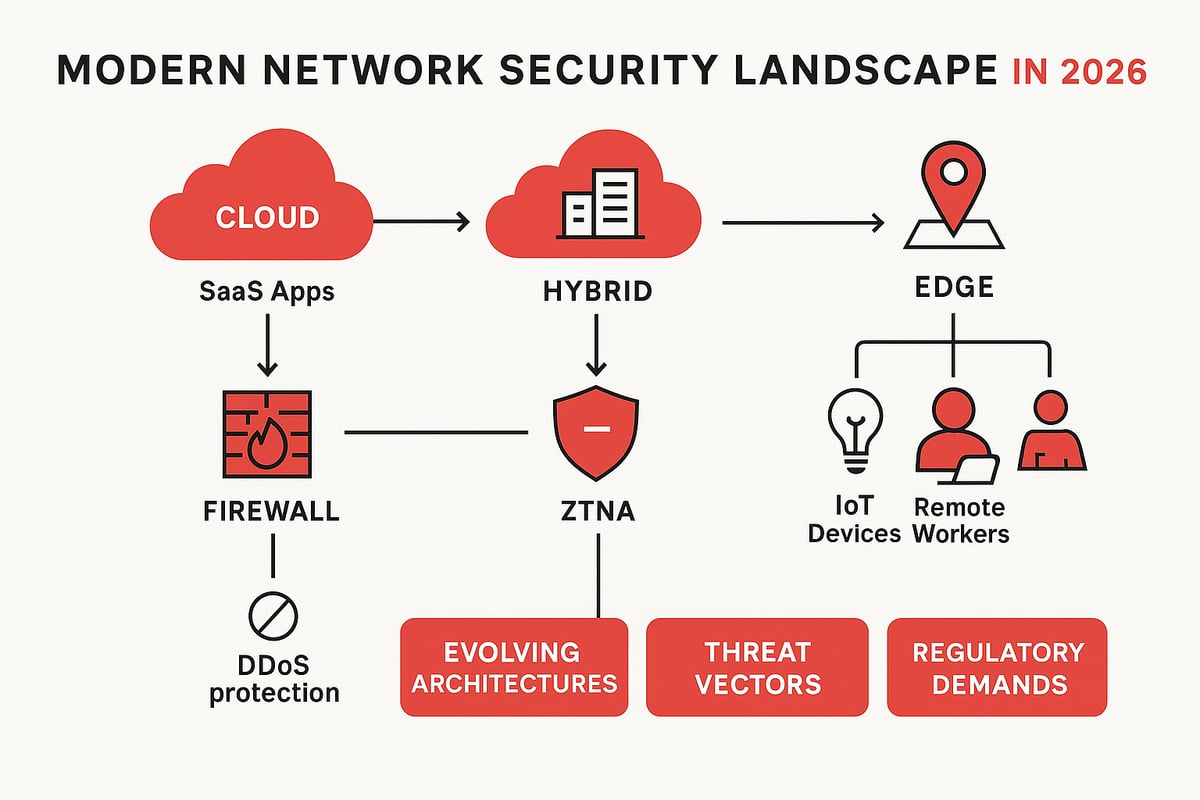
The Evolution of Network Architectures
The way we build and use networks has transformed dramatically. Organizations are moving away from traditional, perimeter-focused networks and embracing cloud-first, hybrid, and distributed models. This shift means employees, devices, and data live across multiple clouds, branch offices, and remote locations.
With the explosion of SaaS, IoT, and edge computing, the attack surface grows wider each year. Remote work and BYOD policies add further complexity, reducing the effectiveness of legacy security controls. According to Cloudflare, 80% of enterprises now operate in multi-cloud environments, which demands smarter network security solutions. For those new to these concepts, it can help to start with network security fundamentals.
Rising Threats and Attack Vectors
Attackers are more resourceful and coordinated than ever. Ransomware, phishing, and supply chain attacks have surged, targeting organizations of every size. Advanced persistent threats (APTs) now focus on critical infrastructure, while AI and automation empower attackers to craft sophisticated campaigns.
Large-scale DDoS attacks continue to set records, and Cloudflare reports a steady rise in attack volume. Insider threats and misconfigured cloud services open new doors for cybercriminals. In this fast-paced environment, network security solutions must adapt rapidly to keep pace with evolving risks.
Regulatory and Compliance Pressures
Keeping up with compliance is no small feat in 2026. New and updated data privacy laws, such as GDPR, CCPA, and emerging global standards, place strict demands on how data is handled and protected. Industry-specific mandates like HIPAA and PCI DSS add extra layers of complexity.
Organizations must maintain continuous monitoring and ensure rapid incident response to avoid hefty penalties. Network security solutions now play a crucial role in automating compliance checks and providing the visibility needed for audit readiness.
Visibility and Control Challenges
Managing security tools can feel overwhelming. Many organizations use too many point solutions, which leads to management silos and critical blind spots. Security teams often lack visibility into lateral movement within networks and struggle to monitor user behavior effectively.
Recent industry surveys reveal that 60% of organizations report poor visibility into their network traffic. Unified network security solutions are essential for breaking down silos and streamlining threat detection and response.
Key Insights
The clear message for 2026 is that security must be unified, adaptive, and able to scale as organizations grow. Proactive threat intelligence and automation are now baseline expectations, not optional extras.
Balancing performance, user experience, and security is a constant challenge. The right network security solutions empower organizations to protect assets, support innovation, and respond quickly to whatever comes next.
Core Components of Modern Network Security Solutions
Modern network security solutions are built from a blend of innovative tools and proven strategies. As we head into 2026, these components are not just nice to have—they are essential for defending your organization’s most valuable assets. Let’s break down the essential building blocks, so you can see how each piece fits into a comprehensive defense.
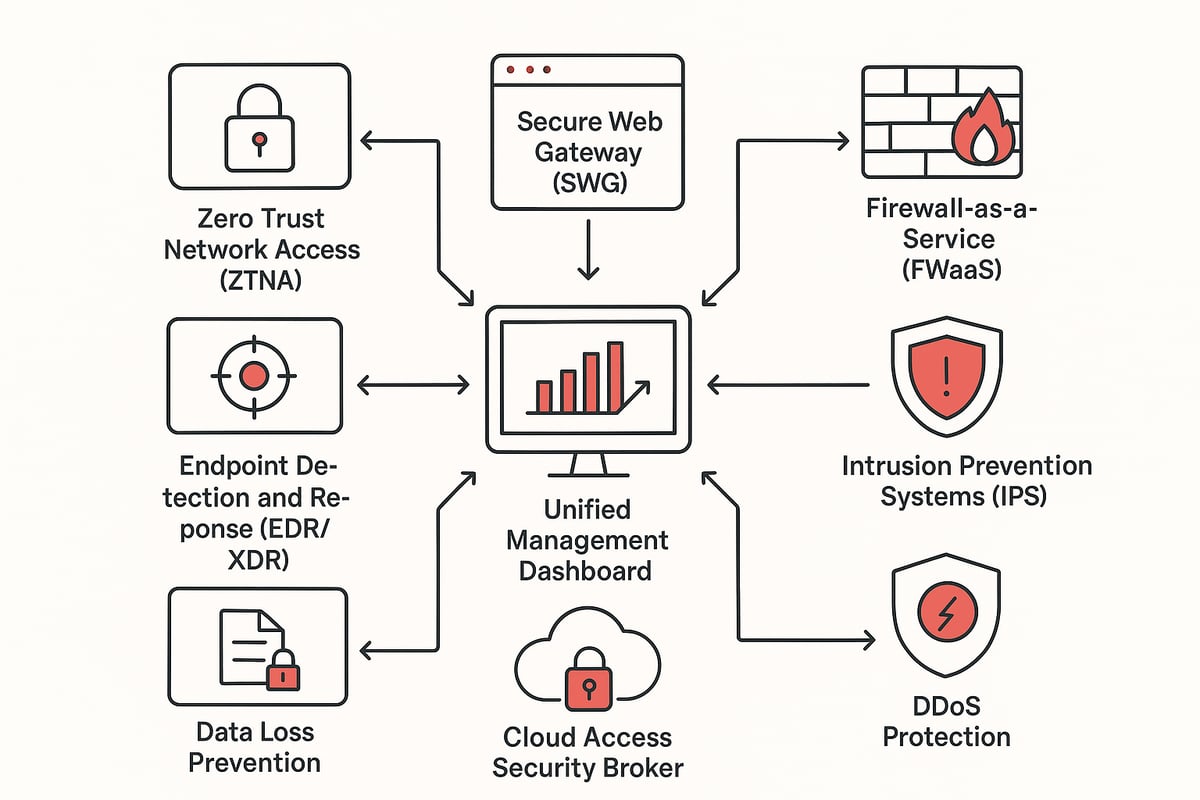
Zero Trust Network Access (ZTNA)
Zero Trust Network Access is a foundational pillar in modern network security solutions. The principle is simple: never trust, always verify, regardless of where a user or device connects from. ZTNA replaces traditional VPNs with dynamic, identity-driven policies that control access. This approach reduces risk by segmenting networks and limiting lateral movement.
- Enforces least-privilege access
- Validates user identity and device posture every session
- Integrates with multi-factor authentication
Security teams value ZTNA for its flexibility and ability to adapt to cloud, hybrid, and remote environments.
Secure Web Gateway (SWG) and Firewall-as-a-Service (FWaaS)
A Secure Web Gateway and Firewall-as-a-Service form the next layer of network security solutions, inspecting and filtering all web traffic. SWG blocks malicious sites, stops phishing, and prevents data leaks. FWaaS delivers firewall protection from the cloud, ensuring consistent security wherever users go.
- Real-time threat detection
- Policy enforcement for users and devices
- Cloud-native scalability
This combination allows organizations to protect users on any device, over any connection, without sacrificing performance or flexibility.
Intrusion Prevention Systems (IPS) and DDoS Protection
Intrusion Prevention Systems and DDoS Protection are must-haves in your network security solutions toolkit. IPS monitors traffic for known and zero-day threats, blocking attacks before they cause harm. DDoS protection automatically mitigates large-scale attacks, keeping services available.
- Real-time detection and response
- Automated blocking and alerting
- Defense against both volumetric and application-layer assaults
To dive deeper into how IPS works, check out this Intrusion prevention systems explained resource. These solutions are essential for stopping advanced threats and safeguarding uptime.
Cloud Access Security Broker (CASB) and Data Loss Prevention (DLP)
As cloud adoption grows, CASB and DLP play a vital role in network security solutions. CASB provides visibility and control over SaaS and cloud platforms, while DLP prevents sensitive data from leaving your environment.
- Monitors user activity in the cloud
- Enforces compliance with regulations
- Blocks unauthorized sharing or downloads
By integrating CASB and DLP, organizations keep data secure and meet evolving regulatory demands.
Endpoint Detection and Response (EDR/XDR)
Endpoint Detection and Response is the frontline defense for devices in any network security solutions strategy. EDR monitors endpoints for suspicious activity, responding to threats in real time. Extended Detection and Response (XDR) takes this further, correlating data across endpoints, networks, and clouds.
- Automated threat hunting
- Rapid isolation of compromised devices
- Centralized investigation tools
These technologies empower security teams to act quickly, reducing the impact of breaches.
Unified Management and Visibility
The final cornerstone of effective network security solutions is unified management and visibility. Instead of juggling multiple dashboards, teams gain a single pane of glass for policy, threat, and compliance management.
- Centralized logging and analytics
- Streamlined incident response workflows
- Reduced management overhead
Unified platforms eliminate silos, drive efficiency, and equip organizations to respond to threats faster and more confidently.
Step-by-Step: How to Implement a Future-Ready Network Security Strategy
Building a secure network in 2026 requires a transparent, phased approach. With cyber threats constantly evolving, a well-structured roadmap can help organizations confidently deploy the right network security solutions. Let’s walk through each step together, ensuring your defenses are resilient, adaptive, and ahead of the curve.
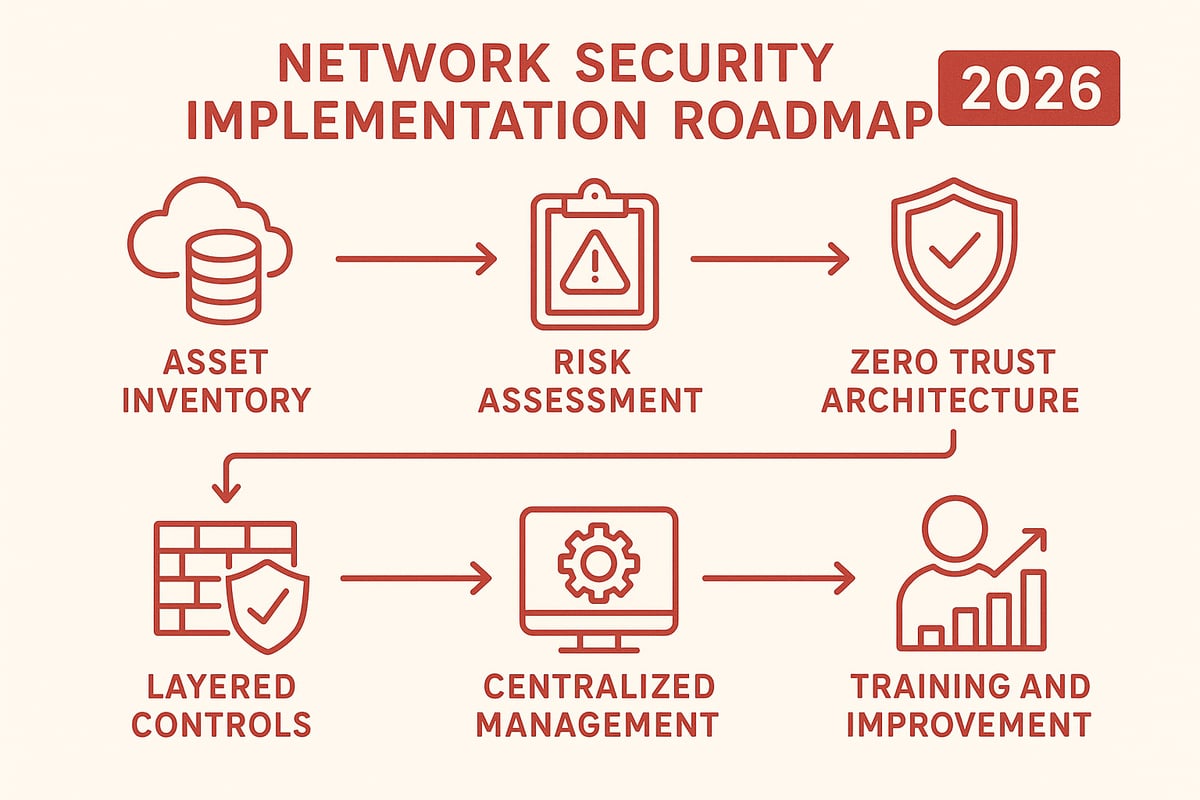
Step 1: Assess Your Current Security Posture
Start by mapping out your entire digital landscape. Inventory all assets, including hardware, software, data flows, and user roles. Pay close attention to legacy systems, shadow IT, and any unmanaged or bring-your-own devices that might bypass standard controls.
Create a checklist to identify:
- Devices (laptops, servers, IoT, mobile)
- Applications (on-premises, SaaS)
- Data repositories and flows
- User accounts and access levels
Understanding your current setup is foundational for choosing the most effective network security solutions. This baseline helps you spot vulnerabilities and prioritize what needs immediate attention.
Step 2: Define Security Objectives and Risk Tolerance
With your environment mapped, align your security goals with overall business objectives and compliance requirements. Decide which assets are mission-critical and establish your organization’s appetite for risk.
Key actions include:
- Listing regulatory obligations (GDPR, HIPAA, PCI DSS)
- Identifying “crown jewels” (sensitive data, intellectual property)
- Setting incident response procedures and acceptable risk levels
This clarity ensures that every move you make with network security solutions is purposeful, efficient, and tailored to your true needs.
Step 3: Design a Zero Trust Architecture
Zero Trust is now the gold standard for modern network security solutions. The principle is simple: never trust, always verify, no matter where users or devices connect from. Segment your networks, enforce least-privilege access, and replace or supplement VPNs with Zero Trust Network Access.
Implement these measures:
- Network segmentation to contain threats
- Identity and context-based access controls
- Continuous verification for users and devices
For comprehensive guidance, explore the “Implementing a Zero Trust Architecture: NIST Guide” which offers actionable steps for a smooth transition. Adopting Zero Trust reduces the risk of lateral movement and insider threats across your infrastructure.
Step 4: Deploy Layered Security Controls
A robust defense relies on multiple layers working in harmony. Deploy secure web gateways, firewall-as-a-service, intrusion prevention systems, and DDoS protection at your network edge. Extend cloud access security broker and data loss prevention tools to your SaaS and cloud platforms.
Don’t forget endpoint protection—EDR or XDR solutions can catch threats that slip past perimeter defenses. Each layer of network security solutions adds another hurdle for attackers, making your organization a tougher target.
Step 5: Centralize Management and Monitoring
Managing security through a patchwork of tools leads to blind spots and delays. Instead, consolidate your controls into a unified dashboard for real-time visibility and streamlined policy enforcement.
Benefits of centralized management:
- Faster threat detection and response
- Reduced alert fatigue for security teams
- Easier compliance reporting
Unified management platforms make it simpler to orchestrate your network security solutions and adapt to new risks as they arise.
Step 6: Test, Train, and Continuously Improve
No security strategy is complete without regular testing and ongoing education. Schedule penetration tests, vulnerability scans, and red team exercises to uncover weaknesses before attackers do.
Build a culture of security by:
- Training staff on phishing, incident response, and best practices
- Simulating real-world attacks to test readiness
- Using threat intelligence to update defenses proactively
Continuous improvement ensures your network security solutions stay ahead of emerging threats and regulatory changes.
Key Insights
Implementing future-ready network security solutions is a journey, not a one-time project. Taking a phased, step-by-step approach minimizes disruption and maximizes effectiveness. Real-world data shows organizations embracing Zero Trust report 50 percent fewer breaches, underlining the value of proactive, modern security.
Stay committed to evolving your defenses. By following these steps, you’ll position your business to thrive securely in 2026 and beyond.
Evaluating and Selecting Network Security Solutions in 2026
Choosing the right network security solutions in 2026 is a critical decision that impacts every aspect of your business. The landscape is crowded, and the stakes are higher than ever. Whether you are leading a global enterprise or a growing startup, knowing what to look for can help you build a safer, more resilient network.
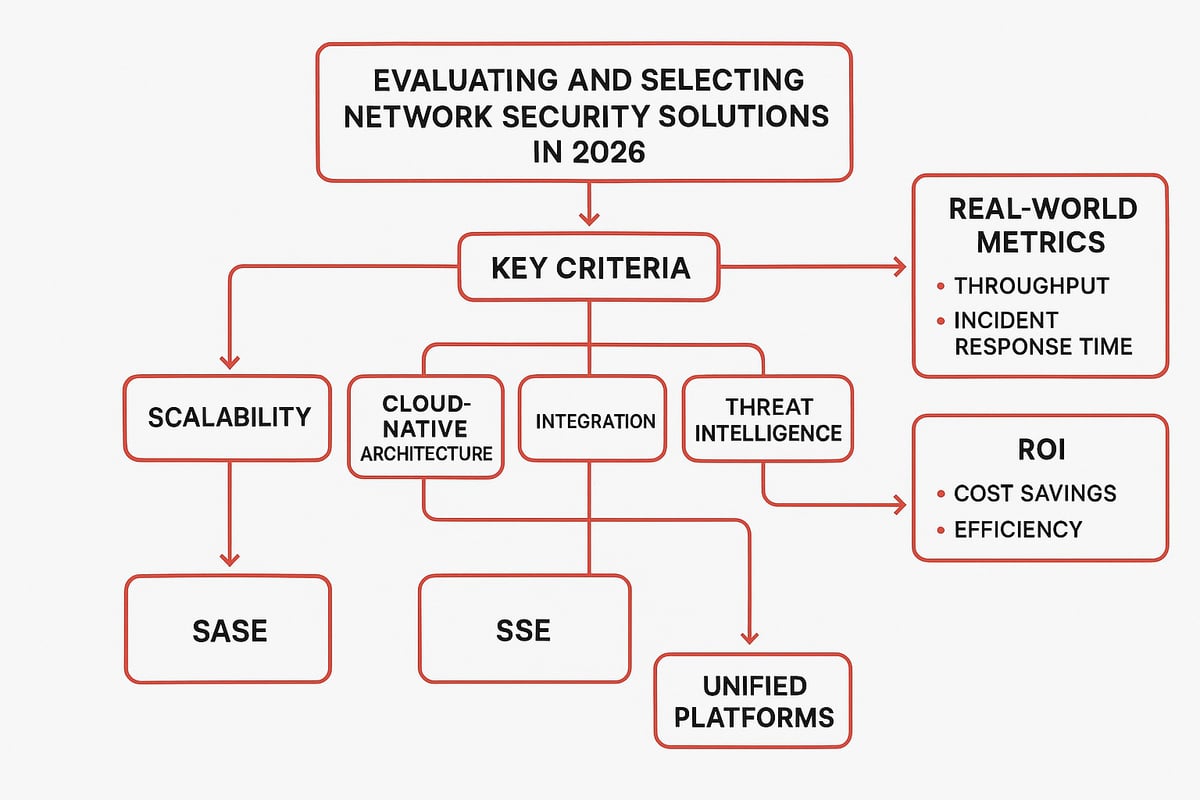
Criteria for Choosing the Right Solutions
When evaluating network security solutions, start by identifying your unique business needs and technical requirements. Scalability should be at the top of your list, especially for organizations using cloud or hybrid environments. Solutions must grow with your business and handle fluctuating workloads.
Integration is key. Your chosen platform should work seamlessly with your existing IT and security stack. Look for solutions that support real-time threat intelligence and automated responses, as these capabilities improve detection and accelerate incident response.
Vendor reputation matters. Choose partners with a strong track record for support, innovation, and reliability. Don’t overlook compliance needs, especially with evolving regulations. For a deeper dive into securing cloud and hybrid environments, check out this Cloud security strategy and policy guide.
- Scalability for hybrid and cloud networks
- Seamless integration with current systems
- Real-time intelligence and automation
- Strong vendor support and compliance alignment
The right criteria set the foundation for future-proof network security solutions.
Comparing Leading Solution Types
The market offers a variety of network security solutions, each with unique strengths. Secure Access Service Edge (SASE) combines networking and security in a unified, cloud-native model. This approach appeals to businesses seeking simplicity and scalability.
Security Service Edge (SSE) focuses on core security services, such as Zero Trust Network Access, Secure Web Gateway, and Cloud Access Security Broker. SSE provides targeted protection for users and devices, especially in distributed environments.
Point solutions address specific threats but can create management silos. Unified platforms, on the other hand, bring together multiple security layers under one dashboard, streamlining operations and reducing complexity.
- SASE: Networking and security convergence
- SSE: Advanced, focused security services
- Point solutions: Specialized, but risk silos
- Unified platforms: Centralized control, easier management
Selecting the right type of network security solutions depends on your organization’s structure, size, and risk profile.
Total Cost of Ownership and ROI
Budget considerations play a vital role in selecting network security solutions. It’s essential to look beyond initial licensing fees. Evaluate ongoing maintenance, operational costs, and the resources required for deployment and management.
Cloud-based models are becoming increasingly popular, often reducing infrastructure overhead and enabling predictable, subscription-based pricing. Many organizations report significant cost savings after shifting to SASE or unified security platforms.
- Lower hardware and infrastructure costs with cloud solutions
- Easier updates and scalability reduce long-term expenses
- Less downtime and fewer breaches improve ROI
For example, businesses moving to SASE platforms have seen up to 30 percent savings in total security spend. Investing in modern network security solutions pays off through improved efficiency and reduced risk.
Case Studies and Real-World Examples
Real-world success stories highlight the benefits of smart network security solutions. Enterprises migrating from legacy MPLS to SD-WAN with embedded security have achieved more agility and better threat protection.
Healthcare providers adopting cloud-native stacks have met strict regulatory standards like HIPAA, all while simplifying compliance management. Retailers using managed DDoS protection have cut downtime by as much as 90 percent, keeping their digital storefronts safe and available.
- Enterprise: MPLS to SD-WAN migration with security
- Healthcare: HIPAA compliance through cloud-native tools
- Retail: Dramatic DDoS downtime reduction
These examples show that with the right network security solutions, organizations can boost resilience, meet compliance goals, and protect their most valuable assets.
The Role of AI, Automation, and Threat Intelligence in 2026
Artificial intelligence and automation are now at the heart of modern network security solutions. As threats become more dynamic, organizations need smarter ways to stay ahead. In 2026, the best defense is a blend of AI-driven detection, automated responses, and real-time threat intelligence. Let us dive into how each of these elements is reshaping network security solutions.
AI-Powered Threat Detection and Response
AI and machine learning have revolutionized how network security solutions identify and neutralize threats. These systems analyze vast amounts of network data in real time, learning to spot new attack patterns as they emerge. Unlike traditional rule-based tools, AI models adapt quickly, closing gaps that attackers once exploited.
By automating detection and response, organizations cut down the time it takes to investigate incidents. In fact, AI-driven incident response can reduce investigation time by up to 70 percent, making breaches less damaging. For more on how AI is redefining security, check out “Cybersecurity Trends in 2026: AI Defense and Digital Trust”. As a result, network security solutions are more proactive, resilient, and effective than ever.
Automated Policy Management and Compliance
Managing security policies and compliance requirements is no longer a manual task. Modern network security solutions use automation to update policies on the fly, reacting to changes in user behavior and the threat landscape. This means fewer configuration errors and a stronger, more consistent security posture.
Automated compliance reporting is another game-changer. Instead of scrambling for audit data, teams can generate reports with a click. This saves time and ensures that organizations meet industry standards effortlessly. With automation embedded in network security solutions, staying compliant is easier and less stressful for everyone.
Threat Intelligence Integration
Threat intelligence is the fuel that powers effective network security solutions. In 2026, organizations tap into real-time feeds from global research labs and security networks. These insights help teams recognize zero-day exploits, phishing campaigns, and emerging vulnerabilities before they cause harm.
By integrating threat intelligence directly into their platforms, companies can automate defenses against the latest threats. Studies show that organizations with robust threat intelligence experience up to 40 percent fewer successful attacks. Clearly, threat intelligence is a core pillar of advanced network security solutions.
Self-Healing and Autonomous Security Platforms
Imagine network security solutions that can heal themselves after an attack. With self-healing systems, this is now a reality. These platforms automatically detect issues, adapt defenses, and recover without waiting for human intervention. This reduces the risk of downtime and limits the impact of breaches.
Breakthroughs in adaptive firewall technology support this evolution, as explored in “Adaptive Cybersecurity: Dynamically Retrainable Firewalls for Real-Time Network Protection”. By reducing manual tasks, self-healing platforms help organizations focus on growth, knowing their network security solutions are always learning and improving.
Best Practices and Frameworks for Building Resilient Network Security Programs
Building resilient network security solutions starts with adopting proven frameworks and best practices. In 2026, organizations face complex threats that require both structure and adaptability. Let’s explore what sets leading security programs apart.
Adopting Industry Standards and Frameworks
Industry standards like the NIST Cybersecurity Framework, ISO 27001, and CIS Controls provide a structured roadmap for network security solutions. These frameworks help organizations prioritize risks, map controls to business needs, and ensure compliance with global regulations.
Using frameworks ensures that security programs are not built on guesswork. Instead, they offer a repeatable process for assessment, implementation, and improvement. Adopting these standards also streamlines audits and demonstrates a commitment to clients and regulators.
Security Governance and Leadership
A resilient program relies on strong leadership and cross-functional collaboration. Executive buy-in is essential for securing resources and driving a culture of security. Appointing security champions within teams helps reinforce policies and keeps security top of mind.
Ongoing training and awareness programs empower staff to recognize threats and respond effectively. When leadership sets the tone, everyone understands their role in protecting network security solutions.
Incident Response and Business Continuity Planning
Preparation is key for rapid recovery from cyber incidents. Developing and regularly testing incident response playbooks ensures that teams know what to do when threats strike.
Business continuity planning minimizes downtime and protects critical assets. By having clear protocols, organizations can restore operations quickly and limit the impact of attacks. This proactive approach is a hallmark of mature network security solutions.
Continuous Improvement and Threat Hunting
The best programs never stand still. Routine vulnerability assessments and proactive threat hunting uncover weaknesses before attackers do. Red and blue team exercises simulate real-world attacks, sharpening defenses.
Continuous improvement cycles allow organizations to adapt their network security solutions as threats and technologies evolve. Staying ahead of attackers requires a commitment to learning and agility.
Metrics and Reporting
Tracking key performance indicators like mean time to detect, response rates, and user compliance helps measure progress. Effective reporting translates technical risks into business language, keeping leadership informed and engaged.
Enterprises that invest in these practices—backed by robust network security solutions such as firewalls—report faster incident resolution and higher compliance rates.
Every step, from governance to improvement, strengthens the resiliency of the security posture. Remember, technology alone is not enough. Culture, leadership, and continuous learning are the real engines behind effective network security solutions.
We’ve just covered a lot—navigating new threats, building a strategy that actually works, and making sense of network security in 2026. But you don’t have to do this alone.
If you’re looking for real-world advice, support from peers, and a space to turn insight into action, I invite you to join us in the Join Cyber Launchpad Community.
Together, we can share experiences, ask tough questions, and help each other build stronger, more resilient organizations. Let’s face the future of network security together; you belong with us.