In 2026, every organization faces a rapidly shifting landscape where protecting data goes far beyond just locking down computers. The lines between information security and cyber security have never been blurrier, making it easy to miss important details that could put your business at risk.
Understanding these two fields is not just a technical need, but a mission-critical part of leading in today’s digital world. Without clear knowledge, even the best teams can fall into common traps or overlook key vulnerabilities.
This article will break down what makes information and cyber security unique, where they overlap, and how you can use this understanding to build stronger protection for your organization. Let’s dive in together and identify the key differences that will shape your security strategy.
Defining Information Security and Cyber Security in 2026
Understanding the landscape of information and cyber security in 2026 is more important than ever. As organizations rely on a blend of digital and physical assets, knowing where each discipline starts and ends empowers us to craft smarter, safer strategies.
What is Information Security?
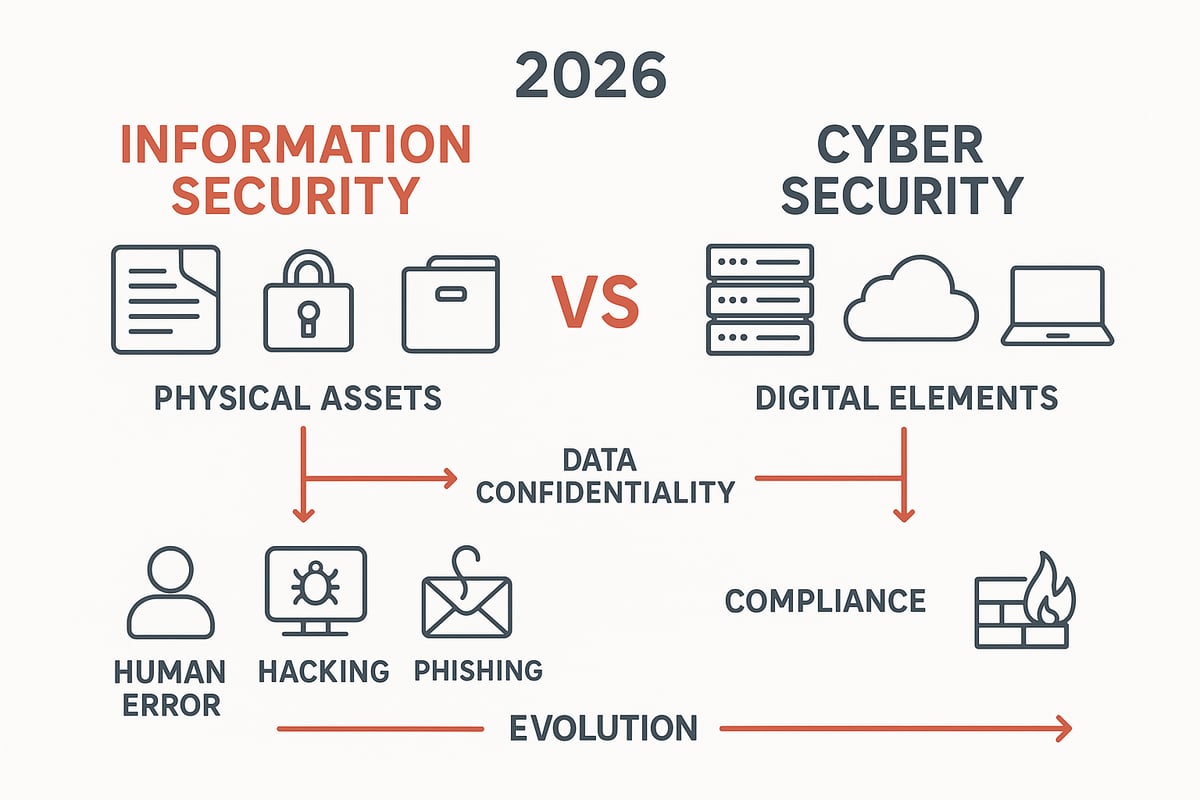
Information security is the discipline focused on protecting all types of information assets, whether digital, physical, or intellectual property. Its primary goal is to ensure the confidentiality, integrity, and availability (CIA triad) of information, regardless of its format or location.
This means that information and cyber security share common roots, but information security extends further. For example, it covers securing paper records, proprietary formulas, and even controlling who can physically access sensitive spaces. Controls range from locked filing cabinets to advanced data governance policies.
Information security addresses risks from multiple vectors, including human error, espionage, and physical theft. It plays a vital role in compliance and risk management frameworks, ensuring organizations meet legal requirements and protect their reputation. Historically, information security has evolved from simple locks and keys to robust frameworks that address both tangible and intangible threats.
Key elements of information security include:
- The CIA triad: confidentiality, integrity, and availability
- Authentication and nonrepudiation
- Physical controls, such as surveillance and badge access
- Policies for data retention and destruction
By covering all information types, information security builds a comprehensive foundation for organizational resilience.
What is Cyber Security?
Cyber security is the discipline that protects digital systems, networks, and data from cyber threats. While information and cyber security are closely related, cyber security zeroes in on internet-connected assets and the digital infrastructure that powers modern organizations.
The main focus is on preventing, detecting, and responding to threats like hacking, malware, phishing, and distributed denial-of-service (DDoS) attacks. Examples of cyber security controls include firewalls, intrusion detection systems, endpoint protection, and, more recently, AI-driven threat intelligence tools.
Cyber security has rapidly evolved. In the past, antivirus software and basic firewalls were the primary defenses. Today, organizations employ advanced analytics and real-time monitoring to stay ahead of increasingly sophisticated attackers.
Some core aspects of cyber security:
- Protection of networks, servers, and cloud environments
- Incident response and digital forensics
- Endpoint and application security
The field is also experiencing significant growth. There were 3.5 million cybersecurity job openings predicted worldwide by 2021, and the demand continues to surge in 2026.
Why the Distinction Matters in 2026
The line between information and cyber security is getting blurrier, yet the distinction is critical. In 2026, organizations face a convergence of physical and digital risks, especially as hybrid work environments and smart technologies expand.
Regulatory requirements have become more demanding, making it essential to clarify responsibilities. New attack surfaces, such as IoT devices, cloud platforms, and AI-driven systems, require precise definitions to avoid gaps in protection.
For example, a hospital might experience a breach involving both physical patient files and electronic health records. If the organization does not distinguish between information and cyber security, critical vulnerabilities could be missed.
Risk management frameworks and compliance audits now demand that organizations align their strategy, staffing, and tools with clear definitions. Misunderstandings can lead to compliance failures and costly incidents.
For a deeper dive into the nuances between these fields, see this Difference between information security and cyber security resource, which explores practical implications for today’s leaders.
Core Principles and Pillars
At their core, both information and cyber security share foundational principles, but they also have unique pillars.
Information security is built on the CIA triad, adding authentication and nonrepudiation as critical elements. These principles ensure that data is only accessible to authorized users, remains accurate, and is available when needed.
Cyber security also relies on the CIA triad, but it emphasizes rapid response, digital forensics, and ongoing threat intelligence. The operational focus is more technical, involving tools like penetration testing and security monitoring.
Both disciplines require strong governance, well-defined policies, and user education. Security audits are a key part of information security, while cyber security often involves regular vulnerability assessments and incident response drills.
Collaboration between teams is essential. In 2026, multidisciplinary approaches help organizations stay ahead of emerging threats and maintain resilience across both digital and physical domains. The integration of information and cyber security principles ensures a robust, unified defense.
Key Differences Between Information Security and Cyber Security
Understanding the key differences between information and cyber security is more important than ever in 2026. As organizations strive to protect their most valuable assets, knowing where each discipline begins and ends helps teams stay resilient. Let’s explore the core distinctions, keeping in mind that the lines can blur, but clarity drives stronger security.
Scope of Protection
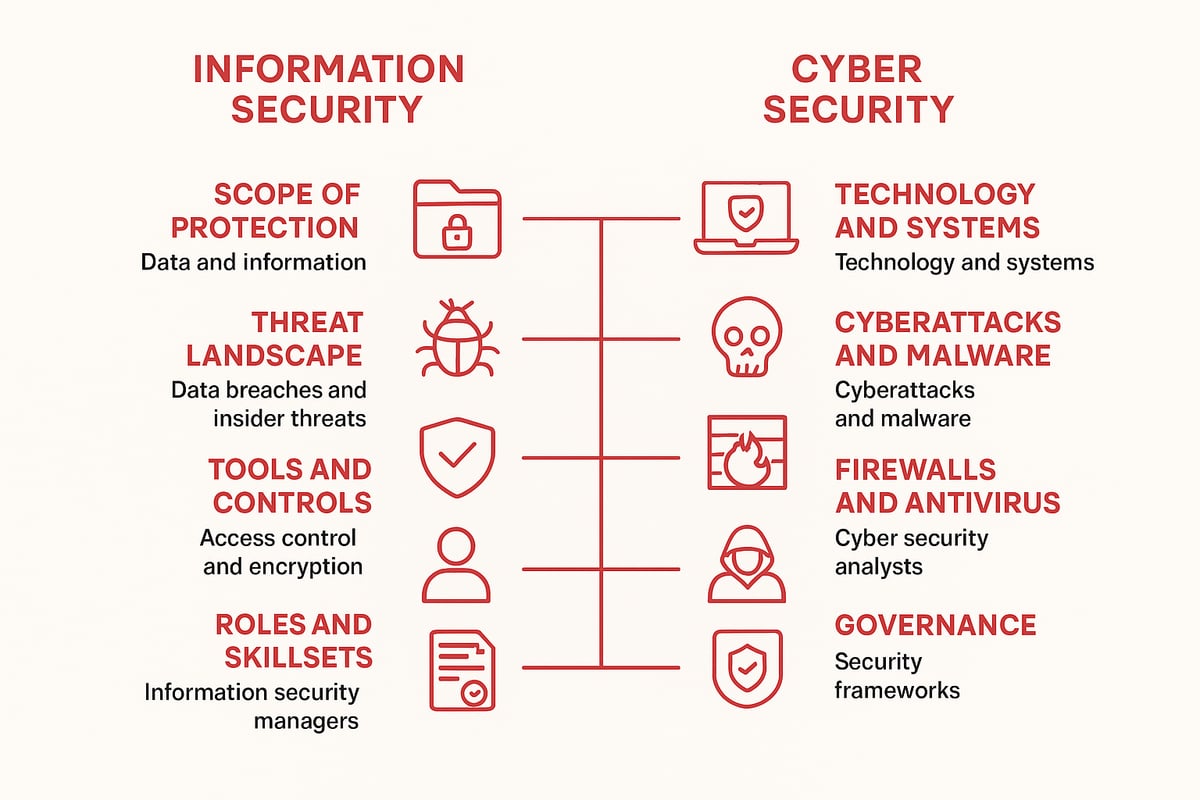
When discussing information and cyber security, scope is the first major difference. Information security covers all types of information, whether digital, physical, or even spoken. This means it includes everything from paper contracts and intellectual property to digital databases.
Cyber security, in contrast, is focused specifically on digital assets and internet-connected systems. It aims to protect networks, servers, computers, and cloud resources from cyber threats. For example, information security might involve securing a locked filing cabinet of sensitive documents, while cyber security would prioritize a firewall protecting a company’s online assets.
Consider a case where espionage occurs through physical theft of documents—that falls under information security. Meanwhile, a ransomware attack on a company’s servers is a cyber security concern. The distinction is important because information and cyber security strategies must adapt to their unique scopes.
For a deeper look at these distinctions, see this detailed analysis of information security vs. cybersecurity differences.
Threat Landscape and Attack Vectors
The threat landscape for information and cyber security is constantly evolving. Information security faces threats such as insider misuse, physical breaches, human error, and social engineering. These can come from misplaced paperwork, unauthorized building access, or even a careless conversation.
Cyber security, on the other hand, battles digital dangers like malware, phishing, zero-day exploits, and organized cybercrime groups. The attack surface is mostly digital, ranging from compromised emails to vulnerable IoT devices.
For example, a USB drop attack—where a malicious device is left for someone to plug into a computer—bridges both worlds. Phishing emails are a classic cyber security issue. In 2026, AI-driven attacks and IoT vulnerabilities are making threat landscapes more complex, pushing both fields to constantly update their defenses.
Tools, Technologies, and Controls
Information and cyber security both rely on specialized tools, but their toolkits look a bit different. Information security leans on encryption, access controls, data loss prevention, and secure storage solutions. Physical controls like locks, surveillance cameras, and shredders are also key in protecting tangible assets.
Cyber security’s arsenal includes firewalls, intrusion detection and prevention systems, endpoint protection, and security information and event management (SIEM) platforms. Network segmentation and patch management are critical for keeping digital environments safe.
A real-world example is a data center that uses badge access (physical control) and multi-factor authentication (digital control) to secure both information and cyber security needs. By combining these tools, organizations can build stronger defenses against diverse threats.
Professional Roles and Skillsets
People working in information and cyber security often have overlapping skills, but their roles can be quite distinct. Information security professionals are typically policy makers, compliance officers, and risk managers. They focus on governance, setting up frameworks, and ensuring business continuity.
Cyber security professionals include security engineers, penetration testers, and incident responders. Their expertise is technical, centered on identifying vulnerabilities, responding to attacks, and deploying countermeasures.
There is overlap, though. Both fields require strong technical knowledge and an understanding of risk. In 2026, the demand for hybrid professionals who can bridge information and cyber security is rising. For instance, an information security manager might handle policy, while a cyber security engineer addresses immediate threats.
Regulatory and Compliance Considerations
Compliance is a major driver for both information and cyber security programs. Information security is governed by regulations like GDPR, HIPAA, and SOX, which cover all forms of information. These laws require organizations to protect both digital and physical records.
Cyber security must meet standards such as PCI DSS and NIST Cybersecurity Framework, focusing on digital systems and data. Sometimes, the requirements overlap, and organizations must ensure they address both sets of rules. For example, healthcare providers must secure patient files in every format, from paper charts to electronic health records.
Regulatory scrutiny is only increasing in 2026, making it vital for organizations to understand the specific requirements for information and cyber security in their industry.
Organizational Strategy and Governance
Effective security starts with strong strategy and governance. Information security is responsible for enterprise-wide policies, risk management frameworks, and business continuity planning. These efforts are often reported at the board level to demonstrate overall risk posture.
Cyber security focuses on technical controls, incident response plans, and vulnerability management. IT Security Directors might track threat metrics and respond to emerging risks in real time.
Strategic alignment is essential. The Chief Information Security Officer (CISO) often oversees both domains, ensuring information and cyber security programs work together. When both sides collaborate, organizations are better prepared for the challenges of 2026.
Where Information Security and Cyber Security Overlap
Understanding where information and cyber security overlap is essential for building a resilient organization in 2026. While each field has its own focus, the intersection is where true protection and collaboration happen. Let’s explore how these two disciplines work hand in hand to create a unified defense.
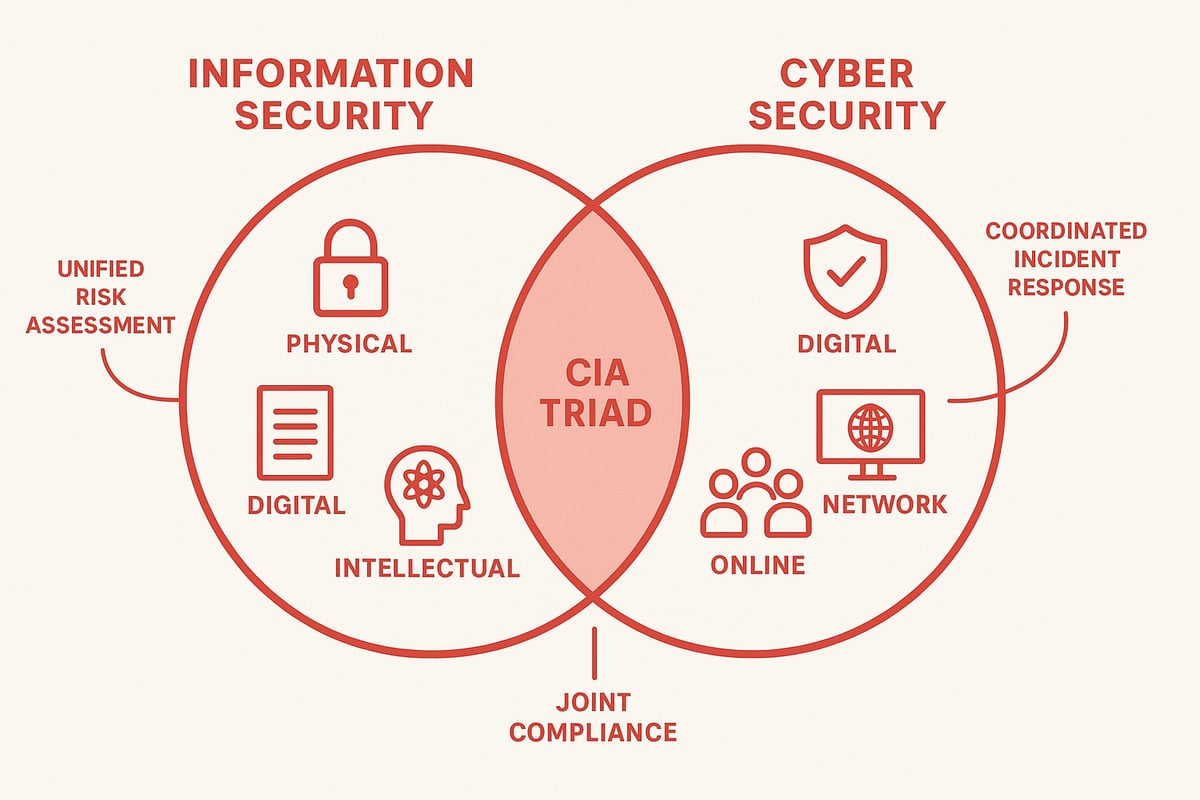
Shared Goals and Principles
At the core of both information and cyber security are the same foundational goals: safeguarding confidentiality, integrity, and availability. These pillars guide every strategy, whether you’re protecting digital files or physical records.
Both disciplines depend on:
- Strong authentication and access controls
- Continuous monitoring and alerting
- Robust backup and disaster recovery plans
Collaboration is key when incidents occur. For example, if a breach impacts both paper and electronic records, coordinated action ensures a swift, effective response. This shared commitment to resilience unites teams and helps build a security-first culture.
Integrated Risk Management
Modern organizations cannot separate physical and digital threats. That’s why integrated risk management is vital in information and cyber security. Teams work together to spot vulnerabilities, assess threats, and design unified policies.
Steps in this approach include:
- Conducting enterprise-wide risk assessments that cover both digital networks and physical locations
- Creating joint playbooks for incident scenarios
- Running cross-functional training and awareness sessions
For example, a risk register now includes threats like physical theft and ransomware side by side. As organizations grow more complex, cross-functional teams are increasingly necessary to manage risk from every angle.
Governance, Compliance, and Legal Frameworks
Meeting regulatory demands is a shared responsibility in information and cyber security. Both fields must align with overlapping standards like ISO 27001 and NIST SP 800-53, and work together on audits and reporting.
Legal requirements often span both domains. For instance, GDPR compliance requires controls for physical documents and digital data alike. Failing in one area can lead to legal and financial penalties across the board.
To dive deeper into regulatory strategies that bridge both fields, explore Governance and compliance in security. Staying proactive and unified in compliance efforts protects your organization’s reputation and bottom line.
Incident Response and Recovery
A robust incident response plan brings information and cyber security teams together, especially when a breach affects multiple asset types. Coordinated teams follow detailed playbooks covering both digital and physical incidents.
Key elements include:
- Joint investigation and digital forensics
- Root cause analysis spanning physical and network layers
- Clear communication plans for all stakeholders
Consider a data center breach: both network security and physical access controls might be compromised. When teams collaborate, recovery is faster and more effective, ensuring business continuity and learning for the future.
Real-World Applications and Case Studies
When we think about information and cyber security, it is easy to imagine complex technology and abstract threats. Yet, the true impact is seen in real-world situations that touch every industry and organization. Let us explore how these concepts play out where they matter most, from hospitals to banks and factories.
Industry-Specific Scenarios
Every sector faces unique challenges when it comes to information and cybersecurity. In healthcare, protecting patient charts means securing both digital records and paper files. Medical devices, such as infusion pumps or heart monitors, require robust cyber security to prevent tampering.
Finance is another prime example. Banks safeguard online transactions, but must also defend against physical check theft and ATM skimming. Manufacturing companies focus on intellectual property, blending information and cyber security controls to protect trade secrets and industrial control systems.
Consider a bank breach: attackers might use physical tactics, like skimming ATMs, while also launching digital fraud schemes. These situations show how information and cyber security work together to defend every layer of modern organizations.
Recent Incidents and Lessons Learned
Recent years have underscored the importance of information and cyber security. Major cyber attacks have targeted organizations like the FBI, NSA, and IRS, using advanced digital exploits. Meanwhile, insider threats remain a challenge, with employees stealing or misusing paper records.
Hybrid attacks are increasingly common. Criminals may exploit both digital and physical weaknesses, such as accessing a secured area to plant a malicious USB device. These incidents teach us that holistic security strategies are not optional—they are essential.
Interestingly, only the largest cyber breaches tend to make headlines. Many physical breaches or information leaks fly under the radar, reminding us that information and cyber security must be comprehensive, not just reactive.
Evolving Attack Techniques in 2026
Attackers are not standing still. In 2026, we see AI-driven phishing campaigns and deepfake social engineering tricks targeting both digital and physical assets. Internet of Things (IoT) devices, from smart locks to connected cameras, create new entry points that blend information and cyber security risks.
Supply chain attacks have also evolved. Hackers may compromise a vendor’s system, then use that access to infiltrate a manufacturer’s network, impacting both digital and physical operations. A notable example is a smart building hack, where cyber attackers manipulate access controls and steal sensitive data.
For a deeper look at how these threats are changing, check out Cybersecurity explained in detail. Staying ahead means understanding the full range of risks that information and cyber security professionals face.
Cross-Functional Security Teams
Modern organizations cannot afford to keep their security teams in silos. Integrated security operations centers (SOCs) now bring together experts from information and cyber security, IT, and legal departments. These cross-functional teams run joint tabletop exercises, simulating crisis scenarios that cut across physical and digital domains.
- Collaboration is key: InfoSec, CyberSec, and IT must all work together.
- Joint exercises help identify gaps before real incidents occur.
- Professionals with blended expertise are in high demand.
By combining forces, teams build resilience and ensure that information and cyber security defenses are always one step ahead. The future belongs to those who break down barriers and create a united front.
The Future: Trends, Challenges, and Skills for 2026 and Beyond
As we look beyond 2026, information and cyber security will shape the way we protect our digital and physical worlds. Rapid evolution in both threats and technologies means we need to anticipate, adapt, and build skills that keep us one step ahead. Let’s explore the trends and strategies that will define the next era for our organizations and teams.
Emerging Technologies and New Threats
The horizon for information and cyber security is expanding quickly, driven by powerful new technologies. Artificial intelligence, quantum computing, and blockchain are not just buzzwords—they are reshaping security strategies.
AI brings smarter threat detection but also enables more sophisticated attacks. Quantum computing threatens current encryption standards, making quantum-resistant methods a top priority. Blockchain offers new ways to secure transactions and identities, but it also introduces unique attack surfaces.
In 2026, organizations must prepare for:
- Cloud and edge computing risks
- IoT devices multiplying entry points
- Remote workforces increasing complexity
By staying proactive, we can keep our information and cyber security measures ready for whatever comes next.
Regulatory Evolution and Globalization
Laws and regulations around information and cyber security are growing more complex each year. Countries are introducing new privacy laws, forcing organizations to manage compliance across borders.
Non-compliance carries heavier penalties, making it essential to track evolving requirements. For example, a single business might face conflicting data rules in different regions, creating real headaches for compliance teams.
Organizations need to:
- Monitor updates to international standards
- Adapt policies for cross-border data transfers
- Build flexible frameworks for changing laws
In 2026, clear governance and up-to-date information and cyber security policies are vital for global operations.
Workforce and Skills Gap
The need for skilled professionals in information and cyber security keeps rising, but the talent gap is a real challenge. With millions of open positions worldwide, organizations compete for experts who understand both technical and strategic aspects.
Demand is growing for people who can bridge traditional InfoSec and advanced cyber roles. Multidisciplinary training, certifications, and hands-on experience are more valuable than ever.
Recent Cybersecurity workforce data and trends show that hybrid roles and ongoing development are key to closing the gap. Upskilling current staff and attracting new talent will define the next wave of success in information and cyber security.
Strategic Alignment and Leadership
Leadership plays a crucial role in aligning information and cyber security with business goals. The Chief Information Security Officer (CISO) is evolving from a technical expert to a strategic partner at the executive table.
Unified vision and communication across departments help organizations balance risk with innovation. Security leaders now guide digital transformation, ensuring resilience and agility.
Key strategies include:
- Integrating security into all business decisions
- Reporting on both risk posture and threat metrics
- Empowering teams with clear direction and support
A strong leadership approach ensures information and cyber security remains a top priority for everyone.
Building a Resilient Security Culture
A resilient security culture is more than just rules and policies—it’s about people, habits, and shared responsibility. Ongoing training, open communication, and a supportive environment help everyone stay alert and prepared.
To foster a strong culture in information and cyber security:
- Schedule regular awareness sessions
- Encourage cross-team collaboration
- Practice crisis simulations and continuous improvement
By investing in people and processes, organizations can build a lasting shield against both expected and emerging threats.
Expert Guidance and Practical Frameworks for Security Leaders
Navigating the world of information and cyber security can feel overwhelming, especially as threats evolve and responsibilities grow. That is why having access to clear, actionable guidance is essential for every security leader.
At LarsBirkeland.com, you will find step-by-step guides, leadership insights, and practical templates designed to help you build resilient security programs. If you are looking for proven information security policies and frameworks, this resource offers tools that bridge strategy with day-to-day operations.
Whether you are aligning teams, strengthening governance, or communicating risk to business leaders, you are not alone. Explore expert advice and frameworks that empower you to lead confidently in the rapidly changing landscape of information and cybersecurity.
As we’ve seen, understanding the real differences between information security and cybersecurity is crucial for making confident decisions and building truly resilient organizations in 2026. If you’re ready to go beyond theory and connect with peers facing the same challenges, I invite you to join us. Together, we can share experiences, tackle tough questions, and support each other as we navigate this fast-changing landscape. You don’t have to do it all alone.
Let’s grow, learn, and lead as a community. Join the conversation in the Join Cyber Launchpad Community.