Is your organization prepared for the surge of cyber threats in 2026? With just one overlooked vulnerability, the consequences could amount to millions lost in damages or trust. In a world where risks and compliance demands are growing daily, a cyber security audit is no longer optional—it is essential.
This friendly guide will walk you through the entire cyber security audit process. We will explain what it is, why it matters, and how you can use it to protect your business, stay compliant, and build trust. Ready to take control of your security future? Let’s get started together.
What is a Cyber Security Audit?
Understanding what a cyber security audit is can feel overwhelming, but let’s break it down together. At its core, a cyber security audit is your organization’s deep-dive checkup, ensuring everything is secure and compliant. Think of it as a health assessment for your digital environment, helping us spot issues before they become costly problems.
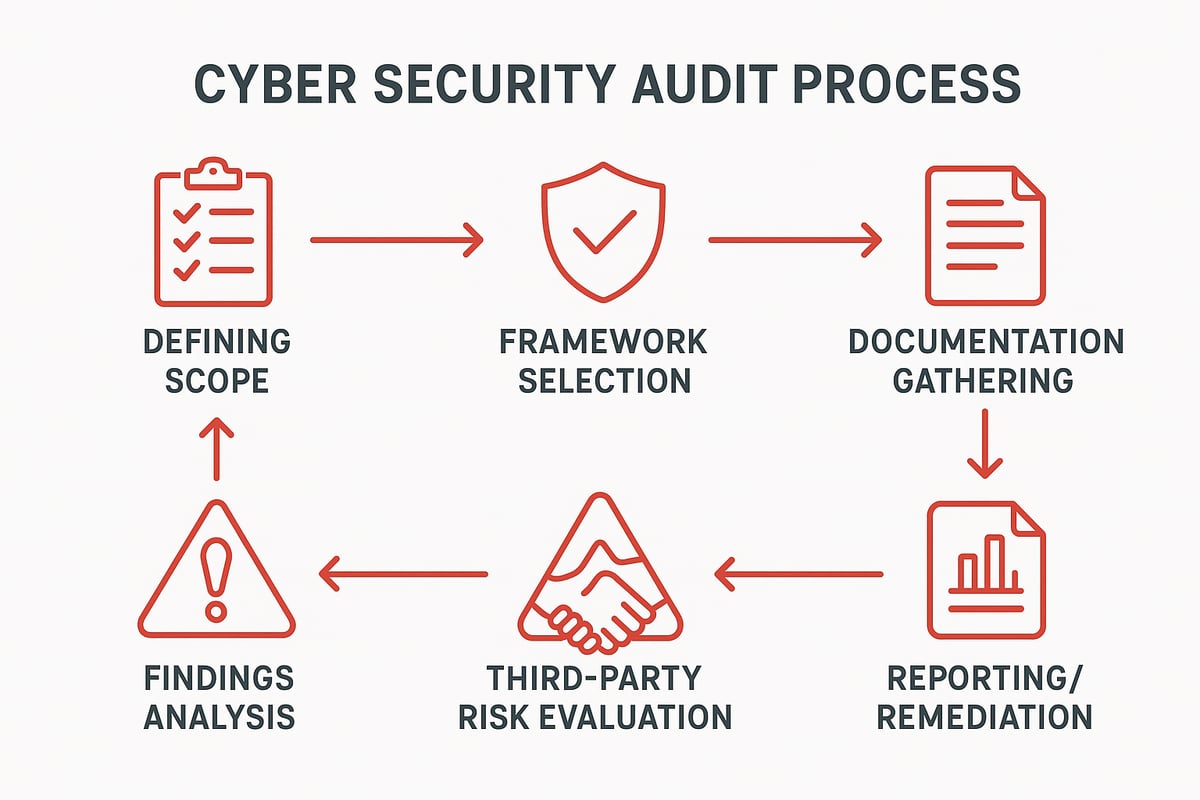
Defining a Cyber Security Audit
A cyber security audit is a formal, systematic evaluation of your organization’s security controls, policies, and procedures. It is designed to identify vulnerabilities, spot compliance gaps, and assess your risk exposure at a specific point in time. Audits can be performed by your internal team or by third-party experts. For many organizations, external audits are required to meet regulatory frameworks such as GDPR, HIPAA, or NIST.
Choosing the right audit framework is crucial, and resources like the best cybersecurity frameworks for audits can guide you in selecting standards like NIST or ISO 27001 to structure your process.
Audit vs. Cybersecurity Assessment
Although a cyber security audit and a cybersecurity assessment sound similar, they serve different purposes. An audit is typically checklist-based, validating that specific controls exist and confirming compliance. For example, it might check that a firewall is in place.
On the other hand, a cybersecurity assessment tests how well those controls actually work, focusing on ongoing risk evaluation. While audits are often required for certifications, assessments help us drive continuous improvement. Think of an audit as verifying the locks are on your doors, while an assessment checks if those locks can really keep intruders out.
Core Objectives of a Cyber Security Audit
The main goal of a cyber security audit is to help us find and fix vulnerabilities before attackers do. Other key objectives include:
- Validating compliance with legal, regulatory, and industry standards
- Confirming the presence and effectiveness of security controls
- Building trust with customers, partners, and stakeholders
- Maintaining and continuously improving our organization’s security posture
By meeting these objectives, we not only protect our data but also strengthen our reputation and resilience.
Types of Cyber Security Audits
There are several types of cyber security audits, each with its own focus:
- Internal audits are conducted by in-house teams, often as a pre-check before an official review.
- External audits are carried out by certified third parties to obtain formal certifications.
- Compliance audits focus on regulatory requirements, such as SOX or PCI DSS.
- Operational audits evaluate the effectiveness of our day-to-day security processes.
For instance, many organizations complete an annual ISO 27001 certification audit to maintain their credentials and assure stakeholders of their commitment to security.
Why Are Cyber Security Audits Essential in 2026?
As we look toward 2026, the digital world is evolving faster than ever. Organizations face new and complex threats every day. A single cyber attack can impact not only finances but also trust and reputation. This is where a cyber security audit becomes a critical safeguard. By regularly auditing your security controls and processes, you can spot vulnerabilities before they become costly incidents.
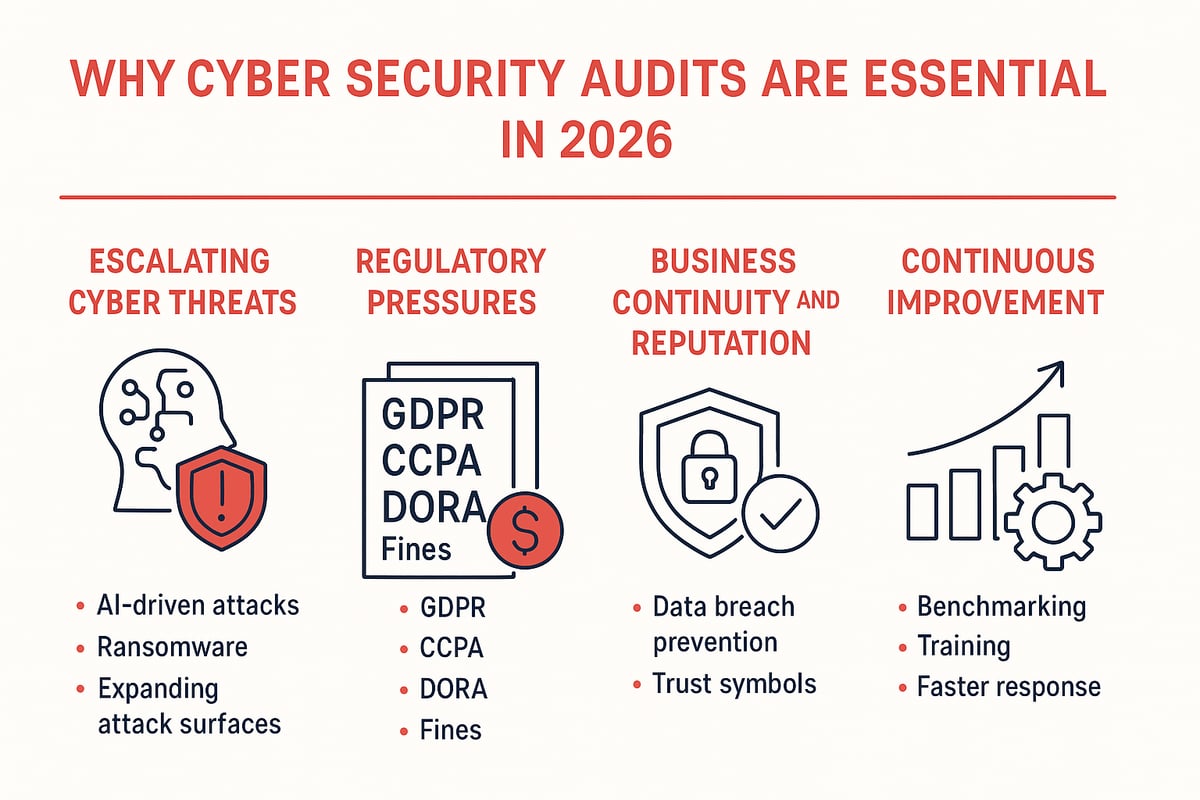
Escalating Cyber Threat Landscape
The threat landscape in 2026 is more aggressive and unpredictable than ever. Cyber criminals are harnessing artificial intelligence to automate attacks, making threats faster and harder to detect. Ransomware is now targeting organizations of all sizes, while remote work and IoT devices have expanded the attack surface.
Recent reports highlight that cybercrime damages are projected to reach $10.5 trillion annually by 2026. For more on the magnitude and nature of these risks, see the Cybersecurity and Data Security Risks in 2026. A cybersecurity audit helps organizations keep pace with these changes, ensuring that new vulnerabilities are quickly identified and managed.
Regulatory and Compliance Pressures
Global regulations are growing stricter, and keeping up is a challenge for every business. Laws like GDPR, CCPA, and DORA demand rigorous data protection and privacy standards. Failing to meet these requirements can result in significant fines and lasting reputational harm.
A cyber security audit is essential for validating compliance with these regulations. By systematically reviewing your controls, you can demonstrate due diligence and avoid penalties. Audits also help you prepare for official inspections and certifications, giving peace of mind to leadership and stakeholders.
Business Continuity and Reputation Management
Every organization relies on digital systems to operate smoothly. A single breach or prolonged downtime can disrupt business and erode customer trust. Regular cybersecurity audit efforts help prevent such scenarios by identifying risks before they escalate.
Audits support business continuity planning, ensuring that critical data and systems are protected. They also build confidence among partners and customers, showing that you take security seriously. In a world where trust is currency, a strong audit record can set you apart.
Continuous Improvement and Security Maturity
A cybersecurity audit is not just a checkbox exercise. Instead, it provides valuable benchmarks for your security program. By comparing results over time, you can measure progress and spot areas for improvement.
Audits also inform ongoing risk management, staff training, and technology investments. Organizations that embrace regular audits tend to have fewer incidents and respond more effectively when issues arise. This proactive approach fosters a culture of security, making your business resilient in the face of new threats.
The Cyber Security Audit Process: Step-by-Step for 2026
Embarking on a cybersecurity audit in 2026 can feel overwhelming, but breaking down the process into clear, manageable steps helps demystify it. By following this structured approach, we ensure every critical area is covered, and your organization is set up for success. Let’s walk through each stage together to build a future-ready cybersecurity audit strategy.
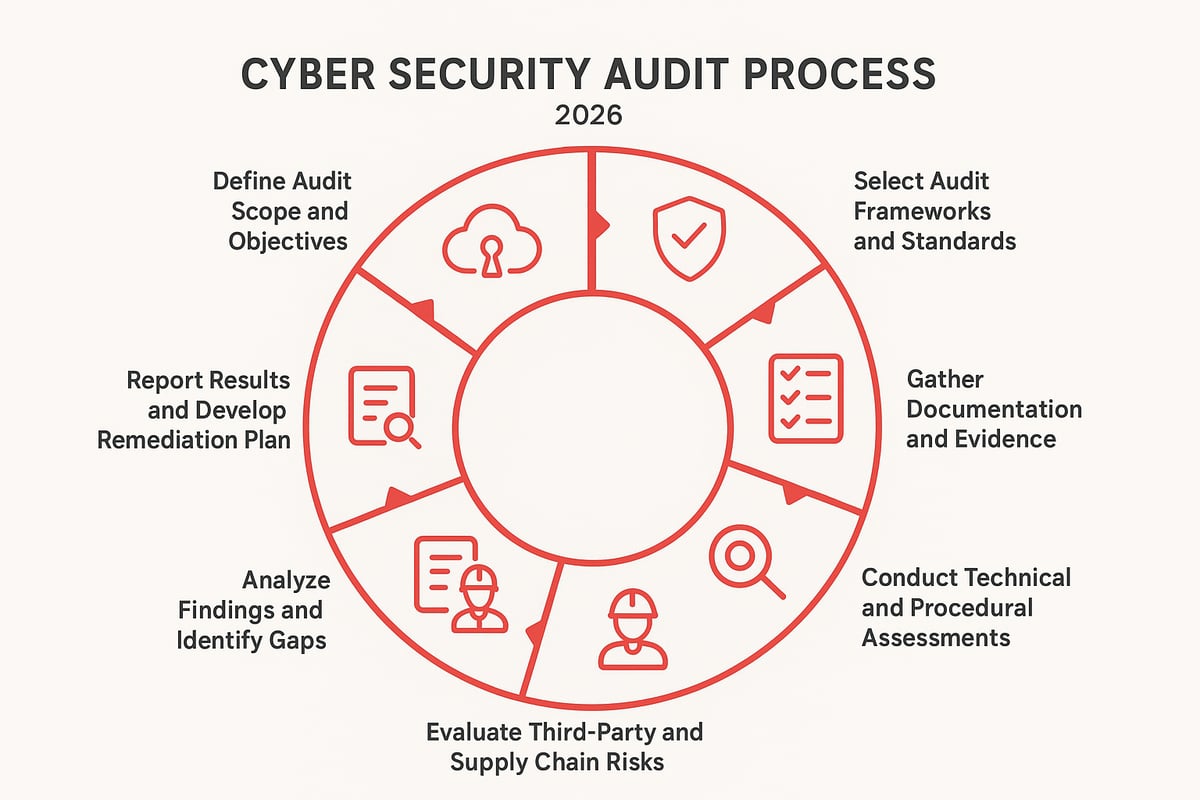
Step 1: Define Audit Scope and Objectives
The first step in any cybersecurity audit is to clearly define the scope and objectives. Decide which systems, processes, and data will be included. Consider business priorities, regulatory needs, and potential risks. Engage stakeholders from IT, compliance, and business units early, ensuring everyone understands what will be reviewed and why.
For example, your audit scope might cover cloud platforms, remote endpoints, and all third-party integrations. Defining the audit boundaries at the start helps focus efforts and avoids surprises later. A well-scoped cybersecurity audit is the foundation for effective risk management and compliance.
Step 2: Select Audit Frameworks and Standards
Next, select the appropriate frameworks and standards to guide your cybersecurity audit. Popular options include NIST, ISO 27001, and industry-specific standards such as HIPAA for healthcare. Map your compliance requirements to a detailed audit checklist. This mapping ensures you meet both legal obligations and internal goals.
It’s also wise to reference resources like Governance and compliance essentials for deeper insights into aligning your audit with regulatory mandates. Selecting the right frameworks sets the stage for a thorough and effective cybersecurity audit, tailored to your sector’s unique needs.
Step 3: Gather Documentation and Evidence
Once your frameworks are set, gather all necessary documentation and evidence for your cybersecurity audit. Collect up-to-date security policies, incident response plans, access control lists, and asset inventories. Prepare technical evidence such as logs, configuration files, and vulnerability scan reports.
Ensure everything is current and accessible. Well-organized documentation streamlines the audit process and makes it easier for auditors to verify compliance. Remember, a cybersecurity audit relies on both policies and proof, so thorough preparation here saves time and reduces stress down the line.
Step 4: Conduct Technical and Procedural Assessments
With the documentation in hand, proceed to the technical and procedural assessments. This part of the cybersecurity audit examines network security, data protection, access controls, and endpoint defenses. Test for vulnerabilities, misconfigurations, and outdated software.
Don’t overlook the human element. Assess employee security awareness and training programs through simulations like phishing tests. Technical and procedural reviews ensure your cyber security audit covers both technology and people, providing a holistic view of your organization’s defenses.
Step 5: Evaluate Third-Party and Supply Chain Risks
Modern organizations rely on a wide network of vendors and partners, making third-party risk evaluation a vital step in the cybersecurity audit process. Review the security controls and compliance status of all third-party providers. Assess contractual obligations and monitor for supply chain vulnerabilities.
Recent industry reports reveal that 60 percent of breaches in 2025 involved third-party vendors. By addressing these external risks during your cybersecurity audit, you reduce the chance of hidden threats slipping through the cracks and protect your organization’s reputation and data.
Step 6: Analyze Findings and Identify Gaps
After assessments, it’s time to analyze the results. Document all vulnerabilities, non-compliance areas, and process weaknesses uncovered during your cybersecurity audit. Prioritize identified risks based on their likelihood and potential impact.
Provide clear, actionable recommendations for remediation. This step ensures you not only find problems but also lay out a roadmap for fixing them. A thorough analysis transforms your cybersecurity audit from a checklist exercise into a strategic tool for continuous improvement.
Step 7: Report Results and Develop Remediation Plans
Finally, compile your findings into clear, executive-level reports as well as technical summaries for IT teams. Your cybersecurity audit report should outline vulnerabilities, compliance gaps, and prioritized remediation steps. Assign responsibilities and set realistic timelines for each action item.
Schedule follow-up audits to confirm improvements are made. For example, a remediation plan might require addressing critical vulnerabilities within 30 days. Transparent reporting and structured remediation help build trust across your organization and with external stakeholders, completing the cybersecurity audit cycle.
Key Areas and Best Practices for Cyber Security Audits in 2026
Ready to strengthen your organization’s defenses? Focusing on the right areas during a cybersecurity audit can make all the difference. Let’s walk through the most important practices for 2026, so you can build a resilient, future-proof security program.
Data Security and Privacy Controls
Protecting sensitive data is the foundation of any cybersecurity audit. In 2026, organizations must ensure robust privacy by default.
- Use strong encryption for both data at rest and in transit.
- Enforce least privilege through granular access controls.
- Regularly review and audit data locations, flows, and retention policies.
- Leverage automated data discovery and classification tools.
A comprehensive cybersecurity audit will spotlight where data lives, who can access it, and how it’s protected. This approach supports compliance and proactive risk management. For a deeper dive into effective strategies, see Cybersecurity risk management strategies.
Network and Endpoint Security
Network and endpoint protection are critical pillars in any cybersecurity audit. Segmentation and layered defenses help limit the spread of threats.
- Segment your network to contain potential breaches.
- Deploy next-generation firewalls and IDS/IPS solutions.
- Ensure all endpoints, including BYOD devices, have updated security agents.
- Monitor for anomalous activity and unauthorized access.
A cybersecurity audit should confirm that both on-premises and remote assets are covered, reducing the organization’s attack surface.
Identity and Access Management (IAM)
Identity is the new perimeter. A cybersecurity audit must verify robust IAM protocols to prevent unauthorized access.
- Require multi-factor authentication for all users.
- Periodically review and remove unnecessary permissions.
- Monitor privileged accounts for signs of misuse.
- Implement automated IAM tools for dynamic access provisioning.
Effective IAM practices uncovered during a cybersecurity audit enhance both security and user productivity.
Incident Response and Recovery Planning
How prepared is your organization for a breach? A cybersecurity audit evaluates your readiness to respond and recover.
- Keep the incident response plan (IRP) current and tested.
- Run regular tabletop exercises to practice response.
- Ensure backups are frequent, secured, and easily recoverable.
Organizations with strong IRPs identified during a cybersecurity audit typically recover faster and significantly reduce breach costs.
Security Awareness and Training
People remain a top vulnerability. A cybersecurity audit should assess how well your team understands and resists threats.
- Offer ongoing training tailored to emerging risks.
- Simulate phishing and social engineering attacks.
- Track and improve employee response rates to threats.
An effective cybersecurity audit reveals gaps in awareness and helps shape a culture of security.
Continuous Monitoring and Automation
Manual processes simply can’t keep pace with modern threats. During a cybersecurity audit, prioritize automation and real-time monitoring.
- Deploy automated vulnerability scanners and threat detection systems.
- Use SIEM and SOAR platforms for continuous oversight.
- Integrate compliance monitoring into daily operations.
A cybersecurity audit that leverages automation uncovers issues faster and drives continuous improvement.
Third-Party Risk Management
Vendors and partners can introduce hidden risks. A thorough cybersecurity audit must address third-party exposure.
- Assess the security posture of all vendors regularly.
- Require up-to-date compliance certifications from partners.
- Monitor third-party access and data sharing.
Including third-party reviews in your cybersecurity audit ensures no weak links in your supply chain.
Emerging Trends and Technologies Shaping Cyber Security Audits in 2026
As we look toward 2026, the cybersecurity audit landscape is rapidly evolving. New technologies, shifting work environments, and regulatory changes are reshaping how organizations approach audits. Staying ahead means understanding these trends and adapting your audit strategy to remain resilient and compliant. Let’s explore the most impactful developments shaping cybersecurity audit practices for the future.
AI and Machine Learning in Auditing
Artificial intelligence and machine learning are transforming the cybersecurity audit process. These technologies automate evidence collection, analyze vast amounts of log data, and identify subtle threats that might go unnoticed by traditional methods. With AI, auditors can:
- Detect anomalies in real time
- Predict and prioritize risks using adaptive models
- Speed up compliance checks with smart automation
AI-driven tools are now essential for any modern cybersecurity audit. According to the 2026 Cybersecurity Outlook by PwC, organizations leveraging machine learning see faster responses and more accurate findings. Embracing these tools helps us stay proactive and confident in our security programs.
Zero Trust Architecture
Zero Trust principles are now at the heart of every effective cybersecurity audit. This approach means that no user or device is trusted by default, whether inside or outside the organization. Audits now focus on:
- Continuous verification of user and device identities
- Micro-segmentation of networks to restrict access
- Dynamic access controls that adapt to changing risk
By embedding Zero Trust into the cybersecurity audit framework, we ensure that threats are contained quickly and privileges are always justified. This shift builds a stronger, more flexible security foundation for our teams and partners.
Cloud Security and Remote Work Challenges
The rise of remote work and multi-cloud environments has greatly expanded the scope of the cybersecurity audit. Auditors now assess:
- Security controls across public, private, and hybrid clouds
- Endpoint protection for remote employees and devices
- Shared responsibility models with cloud providers
A robust cybersecurity audit must examine SaaS platforms, remote endpoints, and how data flows between them. As more of us work from anywhere, understanding these risks and controls is crucial for keeping our data secure and our operations smooth.
Regulatory Evolution and Globalization
Regulatory requirements are growing more complex every year. In 2026, a cybersecurity audit must address global mandates, cross-border data transfers, and sector-specific laws. Key developments include:
- New regulations like DORA and updates to CCPA
- Heightened focus on data governance and privacy
- Mandatory reporting and transparency standards
According to Gartner’s 2026 Audit Plan Hot Spots, internal auditors are prioritizing cybersecurity and compliance more than ever. By staying informed and adjusting our cybersecurity audit approach, we can confidently meet these challenges and protect our reputation.
Expert Insights and Resources for Effective Cyber Security Audits
Navigating the world of cybersecurity audit strategies can feel daunting, but you are not alone. Let us tap into collective wisdom and proven resources that help organizations like yours master every stage of the audit process.
Lessons from Industry Leaders
Industry leaders agree that a successful cybersecurity audit starts with executive support and clear communication. CISOs and audit professionals often highlight the importance of avoiding pitfalls like incomplete documentation or siloed teams. Real-world examples show that organizations with ongoing monitoring and regular audits respond faster to incidents.
Cross-functional collaboration is another key lesson. By involving IT, compliance, and business units, you build a shared sense of accountability. This approach not only improves your cybersecurity audit outcomes but also fosters a culture of trust and resilience within your organization.
Practical Tools, Templates, and Checklists
Streamlining your cybersecurity audit is easier with the right resources. Standardized templates for audit planning and reporting make it simple to track progress and ensure nothing gets missed. Detailed checklists help teams review technical settings, policies, and user practices consistently.
LarsBirkeland.com: Strategic Guidance for Security Leaders
When you need expert guidance tailored to your evolving needs, LarsBirkeland.com is a go-to resource. The platform provides step-by-step guides, templates, and frameworks designed explicitly for effective cybersecurity audit planning and execution.
Beyond technical content, LarsBirkeland.com fosters a supportive community through its CISO LaunchPad, where leaders share real-world insights. These resources empower IT leaders and business owners to bridge strategic and technical gaps, making every cybersecurity audit count for 2026 and beyond.
We’ve covered a lot—from breaking down what a cybersecurity audit really means to sharing the best practices you’ll need to stay resilient in 2026. But you don’t have to navigate this fast-changing landscape alone. If you’re ready to turn insights into action, or just want a supportive space to ask questions and learn from peers who get it, let’s keep the conversation going together.
Join us to connect with other security leaders committed to building stronger, more secure organizations. Welcome to the Join Cyber Launchpad Community. We’d love to have you with us!