Cyber threats are evolving at a pace we have never seen before. In 2026, organizations face relentless cyber attacks that demand more than just basic defenses.
If you want to thrive as a cyber security pro, you need strategies that go beyond the basics. This guide is designed to help IT leaders and security professionals tackle new threats, meet rising regulations, and build true resilience.
Inside, you will find the latest threat trends, advanced defense tactics, proven leadership frameworks, compliance essentials, and future-focused skills. Whether you are leading a team or building your expertise, these insights will help you stay ahead.
Are you ready to level up your defenses and lead your organization with confidence? Dive in and discover what it takes to become a cyber security pro in 2026.
The 2026 Cyber Threat Landscape: What’s Changed?
The cyber threat landscape in 2026 is more unpredictable and complex than ever. For every cyber security pro, adapting to this reality is essential. With attackers leveraging new technologies and exploiting every possible weakness, staying informed and proactive is the only way forward.
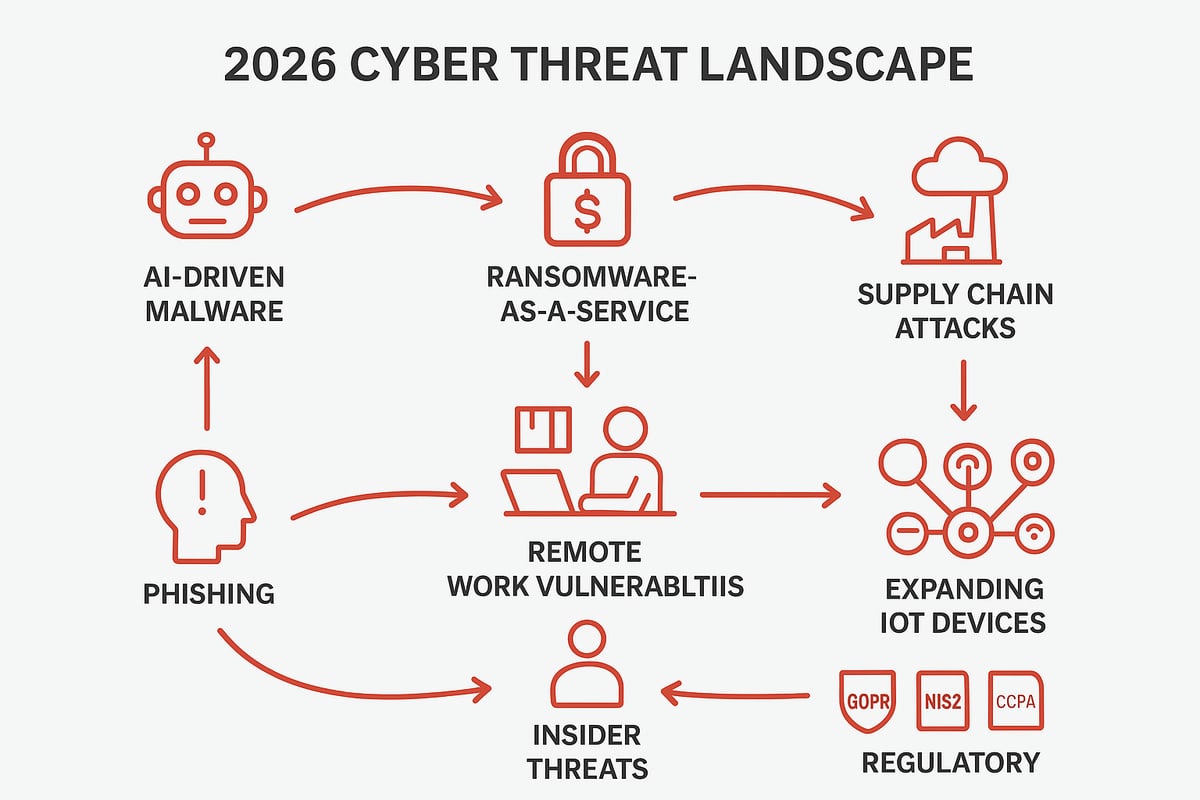
The Rise of Sophisticated Attacks
Attackers in 2026 are arming themselves with advanced tools. AI-driven malware adapts in real time, making detection harder. Ransomware-as-a-service lets even amateurs launch devastating attacks. Supply chain breaches now target trusted vendors to infiltrate networks unnoticed.
Recent industry reports reveal a dramatic increase in automated attacks, with some platforms detecting up to 36,000 scans per second. High-profile breaches in 2025 and 2026 exploited zero-day vulnerabilities, affecting global enterprises and exposing millions of records.
- AI-powered threats evolve rapidly
- Ransomware is more accessible and profitable
- Supply chain attacks bypass traditional defenses
For the cyber security pro, understanding these trends is vital. Read more about the AI-driven surge in cyberthreats shaping this new era.
Expanding Attack Surface in a Hyperconnected World
The digital world is expanding fast. Organizations are connecting more Internet of Things (IoT) devices, moving to the cloud, and embracing remote or hybrid work models. Every new connection can create a new vulnerability.
Recent surveys show over 70% of businesses now support remote or hybrid workforces. This shift has led to a spike in incidents related to unsecured endpoints and misconfigured cloud services.
- IoT devices increase entry points
- Remote work blurs network boundaries
- Cloud adoption demands new security protocols
A cyber security pro must keep up with these changes, ensuring every device and connection is protected.
Regulatory and Compliance Shifts
Laws and regulations are also changing rapidly. Updates to GDPR, NIS2, and CCPA are reshaping how organizations handle data and respond to threats. These rules now require faster breach reporting, stricter data protection, and regular audits.
Failing to comply can lead to heavy fines and reputational harm. For a cyber security pro, staying current with global and regional standards is no longer optional, but a critical part of business operations.
The Human Element: Social Engineering and Insider Threats
No matter how advanced technology becomes, people remain a key target. Social engineering attacks, like phishing and business email compromise, are growing more sophisticated. Attackers now use deepfakes to impersonate executives or trick employees.
Insider threats, whether accidental or malicious, continue to cause major incidents. Case studies from the past year highlight how a single compromised account or careless click can lead to massive data loss.
A cyber security pro must focus on training, awareness, and monitoring insider behavior to reduce these risks.
Key Arguments and Insights
In summary, 2026 brings more persistent, targeted, and automated threats than ever before. Traditional tools and reactive strategies are no longer enough.
Defensive approaches must evolve to meet the challenge. For every cyber security pro, this means adopting advanced frameworks, continuous learning, and a proactive mindset. The organizations that thrive will be those that anticipate threats and adapt quickly.
Building a Pro-Level Cyber Defense Strategy
Staying ahead as a cyber security pro in 2026 means building a defense strategy that adapts to new threats and business needs. Let’s break down the essential pillars that set true professionals apart and help us all create a safer digital world together.
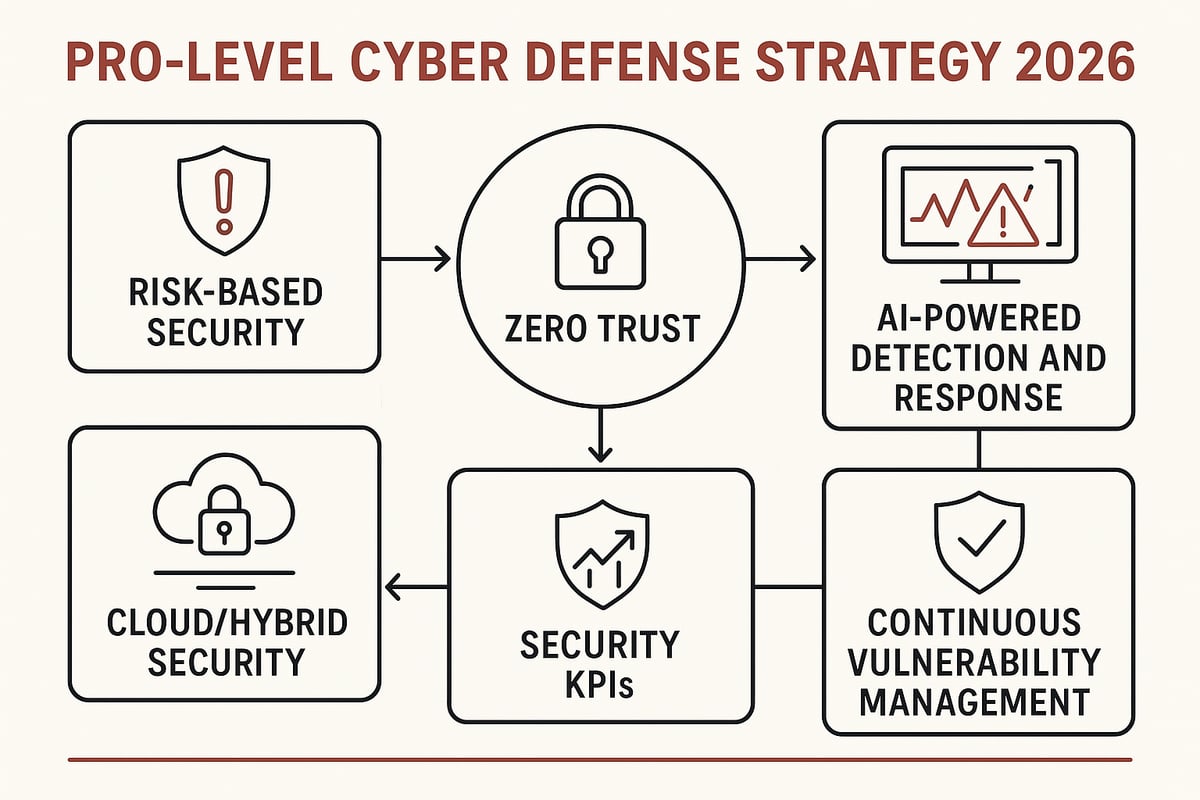
Risk-Based Security: Prioritizing What Matters
Effective cyber security pro strategies begin with risk-based security. Instead of spreading resources thin, focus on what really matters using frameworks like NIST and ISO 27001. These frameworks help you identify your most valuable assets, assess potential threats, and prioritize actions.
For example, risk quantification allows you to allocate your budget and team effort where they have the most impact. This means you can quickly spot where vulnerabilities would hurt most and address them first, ensuring your cyber security pro approach is both smart and efficient.
Zero Trust Architecture: The New Standard
The Zero Trust model is no longer optional for any cyber security pro. Its core principles are simple: never trust, always verify, and give users only the access they truly need. This mindset minimizes the risk of lateral movement if a breach does occur.
Implementing Zero Trust involves mapping your network, segmenting sensitive areas, and enforcing strict identity verification. Many organizations have seen major reductions in breach impact after adopting Zero Trust, proving its value for every cyber security pro aiming to build resilience.
Advanced Threat Detection and Response
Today’s threats are fast, automated, and often powered by AI. As a cyber security pro, you need to outpace attackers with advanced detection and response tools. Integrating AI and machine learning into your monitoring helps spot unusual activity before it becomes a full-blown incident.
Security Orchestration, Automation, and Response (SOAR) platforms are a game-changer. For example, automating incident response can cut down dwell time, allowing your cyber security pro team to respond in minutes instead of hours.
Securing the Cloud and Hybrid Environments
Cloud and hybrid environments bring flexibility but also new risks. A cyber security pro must address unique challenges like misconfigured cloud storage, identity sprawl, and complex governance.
Best practices include enforcing strong identity management, encrypting sensitive data, and setting up clear cloud governance policies. By focusing on these areas, a cyber security pro ensures business agility without compromising security in cloud and hybrid setups.
Continuous Vulnerability Management
Threats evolve daily, so continuous vulnerability management is crucial for every cyber security pro. Automated scanning tools, robust patch management, and real-time threat intelligence keep your defenses up to date.
The impact is clear: organizations with continuous vulnerability management see a significant drop in breach likelihood. Make it routine to scan, patch, and review, so your cyber security pro defenses stay one step ahead.
Metrics and KPIs for Security Maturity
Measuring your progress is key for any cyber security pro. Use metrics like mean time to detect (MTTD), mean time to respond (MTTR), and percentage of systems patched on time. These KPIs help you spot trends, prove value to leadership, and drive ongoing improvement.
If you want to assess and track your organization’s progress, the Cybersecurity Maturity Assessment provides a practical framework to evaluate your security posture and set targeted goals. With clear KPIs, every cyber security pro can demonstrate impact and guide their team toward greater maturity.
Leadership and Strategic Influence in Cybersecurity
In 2026, the role of the cyber security pro is transforming in exciting ways. Leadership is no longer about just managing threats behind the scenes. Instead, today’s security leaders are at the forefront of business strategy, guiding organizations through uncertainty and rapid change. Let’s explore how you can elevate your influence and help your team thrive.
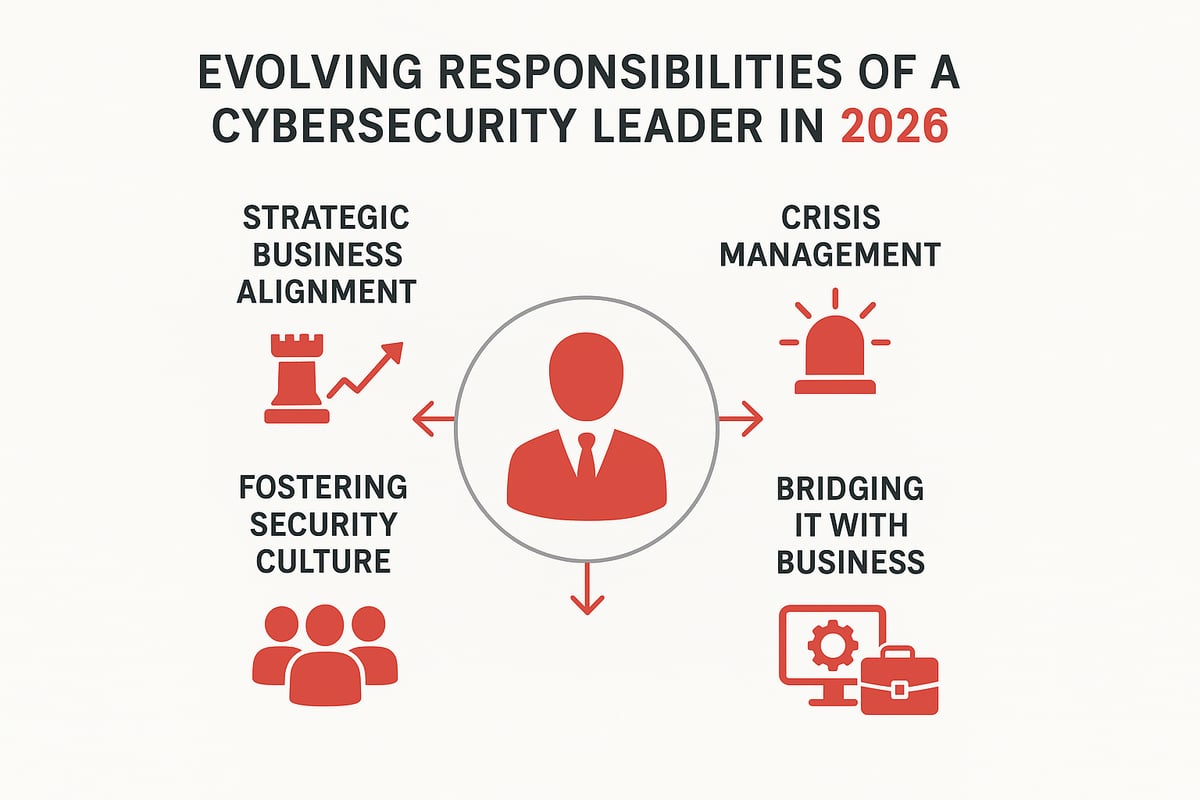
The Evolving Role of the Cybersecurity Leader
The modern cyber security pro wears many hats. Far beyond technical expertise, success now depends on your ability to communicate risks, influence decision-makers, and align security priorities with business objectives. As regulations and threats multiply, leaders must adopt a strategic mindset.
Essential skills for a cyber security pro include proactive communication, translating technical jargon into business language, and engaging with the board. Building relationships across departments is crucial. Accessing real-world guidance from resources like Security Leadership Insights can help you master these skills and drive meaningful change.
By embracing a leadership role, the cyber security pro can shape company culture and strategy, not just respond to incidents. This shift sets the stage for a more resilient, future-ready organization.
Building a Security-First Culture
A thriving security-first culture doesn’t happen by accident. It takes commitment from every cyber security pro, starting at the top and reaching every team member. Security champions within each department can help reinforce best practices and encourage shared responsibility.
Some effective tactics include:
- Launching regular security training tailored for different roles
- Recognizing and rewarding secure behaviors
- Facilitating open discussions about risks and lessons learned
When a cyber security pro models transparency and inclusivity, it’s easier to foster trust and collaboration. Over time, security becomes part of the organization’s DNA, making every person a defender.
Incident Response and Crisis Leadership
Every organization faces unexpected threats. The difference lies in how a cyber security pro leads during a crisis. Preparation is key, and so is the ability to communicate clearly when it matters most.
Steps for effective incident response include:
- Developing a detailed crisis plan and running tabletop exercises
- Assigning clear roles and responsibilities
- Keeping stakeholders informed with timely updates
A well-prepared cyber security pro can turn a potential disaster into a demonstration of resilience. Real-world scenarios show that strong leadership during incidents can prevent reputational damage and build confidence among clients and partners.
Bridging the Gap Between IT and Business
True influence happens when a cyber security pro bridges the divide between technical teams and business leaders. This means translating complex risks into business impacts that everyone understands.
For example, presenting security investments as enablers of growth or compliance can gain executive buy-in. Use case studies to highlight the value of proactive security measures and show how they protect both reputation and revenue.
By building these connections, the cyber security pro ensures that security is a strategic partner, not just a technical necessity. This partnership drives smarter investments and a more resilient future.
Mastering Compliance and Governance in 2026
Staying compliant in 2026 is more complex than ever, yet it is also more critical. As a cyber security pro, you know that regulations shift quickly, and governance frameworks must adapt. This section helps you navigate the regulatory maze, build resilient governance, and foster a culture of privacy and accountability.
Navigating Evolving Regulations
The world of compliance is always in motion. In 2026, updates to GDPR, NIS2, and CCPA have introduced new requirements for data handling, breach notification, and cross-border transfers. For a cyber security pro, keeping pace with these changes is a full-time job.
Organizations now face stricter rules around data minimization and transparency. For instance, GDPR’s latest revision emphasizes real-time breach reporting and enhanced user consent procedures. NIS2 expands the definition of critical infrastructure, pulling more sectors under regulatory scrutiny.
Staying proactive means monitoring regulatory bulletins, engaging with legal teams, and participating in industry forums to anticipate shifts. This way, you can adapt strategies before non-compliance becomes a risk.
Building a Robust Governance Framework
A strong governance framework is the backbone of resilient security. As a cyber security pro, you must ensure policies, procedures, and controls are not only documented but also lived throughout the organization.
Modern frameworks blend classic standards like ISO 27001 with agile, business-aligned approaches. GRC (Governance, Risk, and Compliance) tools help automate policy management, risk assessments, and compliance tracking.
For actionable guidance on frameworks and tools, the Governance and Compliance Essentials resource offers in-depth strategies. Embedding governance into daily operations empowers everyone to take ownership of security, reducing gaps and boosting organizational confidence.
Integrating Privacy by Design
Privacy by design is no longer optional. In 2026, every cyber security pro must champion privacy from the earliest stages of product and process development.
Start by mapping data flows and identifying risks at each lifecycle point. Collaborate with developers, product managers, and legal teams to integrate privacy-enhancing technologies and minimize data exposure.
A real-world example is a fintech company that embedded privacy controls into its customer onboarding, reducing regulatory findings and boosting user trust. By making privacy a shared value, you create a culture where compliance is second nature.
Auditing, Reporting, and Continuous Improvement
Auditing and reporting have evolved into continuous, data-driven processes. For the cyber security pro, this means preparing for more frequent and detailed regulatory reviews.
Leverage automated tools to monitor compliance, generate reports, and track remediation efforts. Establish feedback loops with stakeholders to identify weaknesses and document lessons learned.
Key metrics might include audit pass rates, incident response times, and policy adoption rates. By embracing continuous improvement, you ensure compliance is not a one-time event but a living, evolving commitment.
Third-Party and Supply Chain Risk Management
Your ecosystem is only as strong as its weakest link. Every cyber security pro must actively manage risks from vendors, partners, and supply chains.
Start with thorough due diligence: assess the security posture of each third party, review contractual obligations, and require regular attestations. Use technical controls like network segmentation and access restrictions to limit exposure.
For example, organizations often reduce risk by including clear security requirements in contracts and scheduling regular third-party audits. Taking these steps builds resilience, protects your reputation, and shows regulators your commitment to holistic security.
Future-Proofing Your Cybersecurity Skills and Team
Staying ahead as a cyber security pro means never standing still. The threat landscape is evolving fast, and so must we. Building a future-ready team is not just about tools or technology—it’s about people, adaptability, and a shared commitment to growth.
Essential Skills for 2026 and Beyond
Tomorrow’s cyber security pro needs a toolkit that blends technical expertise with adaptability. In 2026, skills in AI, automation, and cloud security are non-negotiable. Threat intelligence is also critical, as attackers use smarter tools and tactics.
According to the 2026 Cybersecurity Outlook Report, organizations face a growing skills gap, especially in cloud and AI-driven security. To stay relevant, a cyber security pro must keep pace with these trends. Are you ready to master the skills that matter most?
Continuous Learning and Professional Development
The learning journey for a cyber security pro is never over. Certifications like CISSP, CISM, and cloud-specific credentials open doors to new opportunities. Micro-credentials and hands-on labs help you build real-world expertise.
Many organizations now offer upskilling programs that close critical knowledge gaps. Prioritizing continuous learning empowers teams to respond to change and innovation confidently. By investing in your growth, you set the standard for others to follow.
Building and Retaining High-Performance Teams
A high-performing cyber security pro team is built on trust, diversity, and shared purpose. Attracting top talent means looking beyond resumes—seek candidates who show curiosity and a willingness to learn.
Retention is just as important as recruitment. Encourage development, offer clear career paths, and celebrate every win. Inclusive environments foster creativity and resilience, helping your team tackle tomorrow’s challenges with energy and unity.
Leveraging Communities and Peer Networks
No cyber security pro succeeds alone. Engaging with professional communities, forums, and mentorship programs unlocks fresh perspectives and practical advice. Peer networks are invaluable for sharing lessons learned and staying ahead of emerging threats.
Find your tribe, whether online or in person. By leaning into community, you empower yourself and your team to grow stronger together, ready to take on whatever comes next.
Step-by-Step: Implementing Expert Cybersecurity Strategies in 2026
Ready to put your cyber security pro skills into action? Let’s walk through a practical, step-by-step framework that helps you elevate your organization’s defense posture, align security with business goals, and foster continuous growth. This approach is designed for real-world impact—no matter your starting point.
Step 1: Assess Current Security Posture
The first step for every cyber security pro is to understand where you stand. Conduct a comprehensive assessment using proven frameworks like NIST or ISO 27001. This means evaluating your existing controls, identifying vulnerabilities, and measuring overall maturity.
Utilize automated tools for gap analysis and threat modeling. Collect feedback from technical teams and business units to ensure nothing slips through the cracks.
Regular self-assessments help you spot weaknesses before attackers do. By knowing your baseline, you can chart the right course forward.
Step 2: Define Strategic Objectives and KPIs
Once you know your starting point, set clear, measurable objectives. A cyber security pro aligns security goals with business priorities, making sure every initiative moves the organization closer to its vision.
Define key performance indicators (KPIs) for core areas like incident response, cloud security, and user awareness. For example, you might track the percentage of systems covered by multi-factor authentication or the average time to patch critical vulnerabilities.
Consider integrating Zero Trust principles to strengthen your objectives. The NIST guide on Implementing Zero Trust Architecture is a valuable resource for setting modern security standards.
Step 3: Develop and Execute a Roadmap
With objectives in place, a cyber security pro creates a living roadmap. Prioritize projects based on risk and business impact. Start with quick wins, then move to long-term improvements.
Break down initiatives into manageable phases. Assign responsibilities, set milestones, and monitor progress. For a detailed template, check out this Strategic Cybersecurity Roadmap to guide your planning and execution.
A well-structured roadmap ensures your team stays focused and adapts as threats evolve.
Step 4: Foster a Culture of Continuous Improvement
Security is never finished. Encourage open communication, regular training, and red teaming exercises. A cyber security pro leads by example, promoting a growth mindset and celebrating small wins.
Create feedback loops with stakeholders to learn from incidents and near-misses. Share lessons learned across teams to raise collective resilience.
This adaptive culture helps you stay ahead of new threats and regulatory changes.
Step 5: Measure, Report, and Communicate Progress
Finally, track results and keep leadership informed. Use dashboards and concise reports to communicate your cyber security pro achievements and challenges.
Highlight trends, share meaningful metrics, and align updates with business outcomes. This builds trust and justifies future investments.
By following these steps, you empower your team to protect what matters most—today and tomorrow.
We’ve covered a lot, from the latest threat trends to building real, resilient security strategies and leadership skills that make a difference. But you don’t have to figure this out alone.
If you’re ready to dive deeper, swap ideas, and connect with peers who get what you’re facing, I invite you to join us in the Join CISO Launchpad Community.
It’s a welcoming space where we share step-by-step playbooks, lessons learned, and real-world frameworks to help each other grow. Let’s keep learning, leading, and building a safer future together.