Did you know that in just the first quarter of 2026, global cyber breaches surged by over 30 percent compared to last year? Attackers are using more advanced tactics, and the cost of a single incident is reaching record highs. For organizations everywhere, the stakes have never been higher.
In this fast-changing landscape, achieving cybersecurity maturity is now the key to building resilience and staying ahead of threats. Companies want to protect their reputation, maintain customer trust, and ensure business continuity, but the path can seem daunting.
This guide is here to help. We will walk you through each step, from understanding cybersecurity maturity models to practical assessment and ongoing improvement. Let’s secure your organization’s future, starting today.
Understanding Cybersecurity Maturity in 2026
Cybersecurity maturity is the secret ingredient that sets resilient organizations apart in our fast-changing digital world. As we approach 2026, attackers are becoming more sophisticated, using everything from ransomware to supply chain attacks. Let’s dive into what cybersecurity maturity means, why it matters more than ever, and how it shapes a safer, more agile business.
Defining Cybersecurity Maturity
Cybersecurity maturity is a holistic measure of how ready and resilient an organization is to prevent, detect, respond to, and recover from cyber threats. Unlike simple compliance checklists, cybersecurity maturity reflects the depth of your security capabilities and how well they align with your business goals and risk appetite.
For example, a company may face ransomware or multi-vector attacks that target both IT systems and supply chains. Organizations with higher cybersecurity maturity anticipate these challenges, adapt policies, and recover faster.
Competitors note that threats are now persistent and multifaceted, making a maturity-based approach vital.
Why Cybersecurity Maturity Matters Now
Recent years have seen a dramatic rise in breach costs and attack frequency. According to CYE’s cost of breach estimator, the average incident can cost millions, not to mention hefty regulatory fines. Low cybersecurity maturity exposes organizations to legal, reputational, and operational risks.
Every sector feels the impact, from healthcare to retail and critical infrastructure. Boards and executives now scrutinize cyber risk as a top business concern. Investing in cybersecurity maturity means building trust, securing customer loyalty, and standing out in the market for your reliability.
Key Elements of Maturity
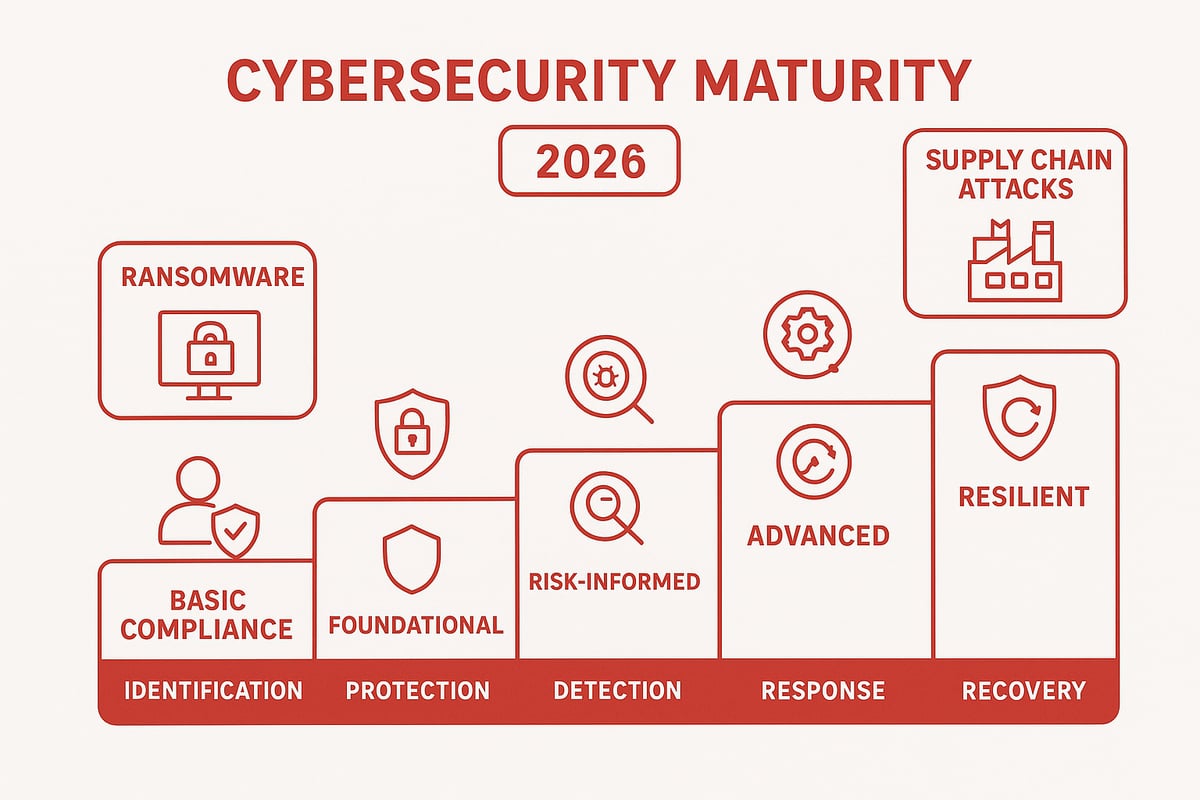
Cybersecurity maturity is built on five core pillars:
- Identification: Knowing your assets, systems, and sensitive data.
- Protection: Implementing robust security controls and defenses.
- Detection: Continuously monitoring for threats and anomalies.
- Response: Having clear incident management and playbooks.
- Recovery: Ensuring business continuity and disaster recovery plans are in place.
These map directly to the NIST CSF’s core functions, forming the foundation for a proactive and resilient cybersecurity program.
Maturity vs. Risk Assessment
Risk assessment and cybersecurity maturity assessment are related but serve different purposes. Risk assessments identify specific vulnerabilities and threats, helping you patch systems or fix gaps. A cybersecurity maturity assessment, however, evaluates your overall strategic readiness, processes, and culture.
For instance, a business might have up-to-date patches (risk control) but lack a mature incident response plan, revealing a maturity gap.
Competitors stress that while risk assessments are tactical, maturity assessments take a proactive, holistic view. This approach helps organizations strengthen their security posture and prepare for evolving threats.
Choosing the Right Cybersecurity Maturity Model
Selecting the right cybersecurity maturity model is a foundational step in building a resilient security program. With so many frameworks available, it can feel overwhelming to know where to start.
Let’s break down the leading options, explore their unique strengths, and guide you toward a model that fits your organization’s needs.
Overview of Leading Models
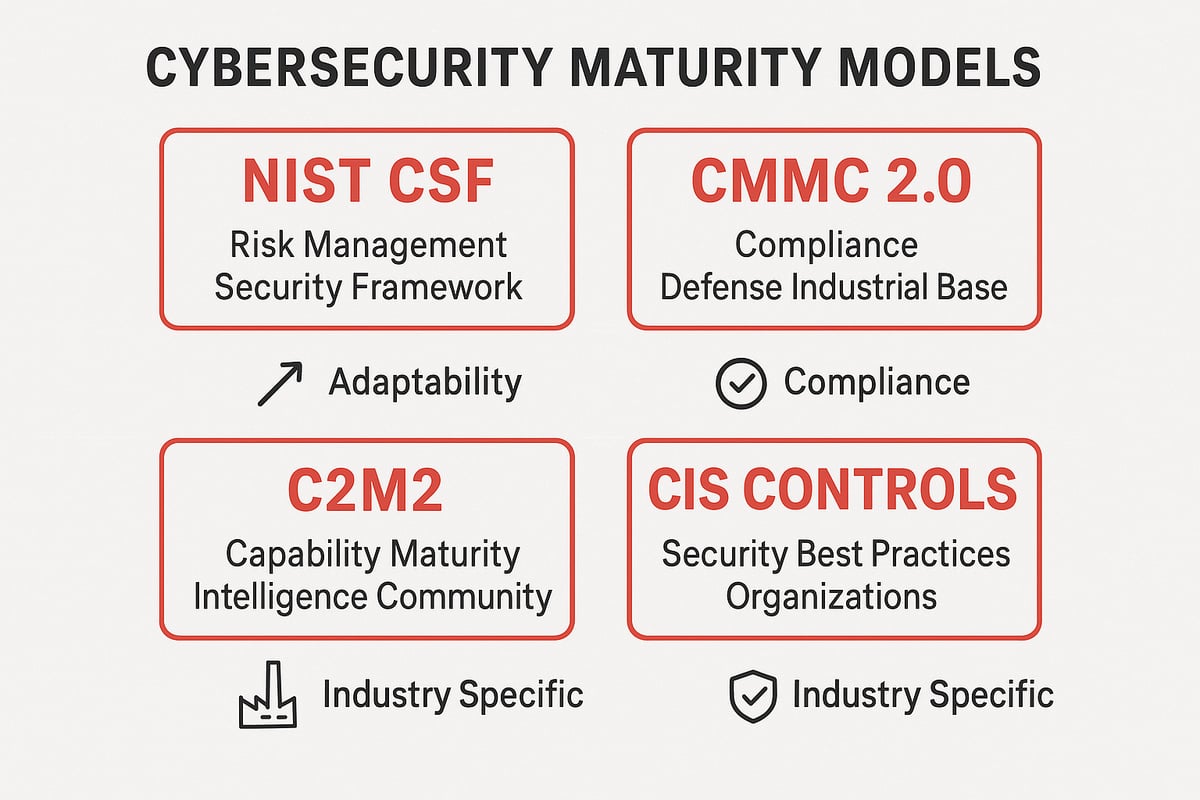
When it comes to cybersecurity maturity, several frameworks stand out as industry leaders. The NIST Cybersecurity Framework (CSF) is widely praised for its flexibility, making it suitable for organizations of all sizes and sectors. CMMC 2.0 is tailored for defense contractors, while C2M2 was developed for energy and critical infrastructure. The CIS Controls offer actionable security practices that are easy to understand and implement.
Each model has its own structure and focus. For example, NIST CSF centers on five core functions, while CMMC 2.0 uses a tiered approach to compliance. C2M2 is domain-based and highly detailed, and CIS Controls emphasize practical steps. If you want a deeper comparison, review this Best cybersecurity frameworks overview for a helpful side-by-side look.
NIST Cybersecurity Framework (CSF)
The NIST CSF is built around five essential functions: Identify, Protect, Detect, Respond, and Recover. This outcome-driven structure helps organizations map their existing practices and spot gaps in their cybersecurity maturity journey.
One of the greatest strengths of the NIST CSF is its adaptability. Whether you’re a small business or a multinational enterprise, you can scale the framework to fit your needs. Implementation tiers within the CSF allow you to benchmark your progress, moving from partial to adaptive cybersecurity maturity as your program evolves. Many organizations begin with NIST CSF because it is risk-based and non-prescriptive, making it practical for real-world environments.
CMMC 2.0 and Sector-Specific Models
CMMC 2.0 introduces three levels of cybersecurity maturity, each with increasing requirements for process and practice. This model is especially important for organizations working with the U.S. Department of Defense, ensuring that sensitive data is protected throughout the supply chain.
C2M2, on the other hand, was designed for the energy sector and other critical infrastructure. It offers a domain-based, detailed approach, allowing organizations to assess and enhance their maturity in targeted areas.
Some industries prefer sector-specific models to align with regulatory or customer expectations. For example, healthcare organizations may use the CIS Controls to address privacy and operational needs, while energy companies lean on C2M2 for its industry focus.
Selecting the Best-Fit Model for Your Organization
Choosing the right cybersecurity maturity model depends on several factors. Consider your regulatory environment, business size, industry, risk profile, and available resources. Each model has pros and cons: NIST CSF is flexible, CMMC 2.0 ensures compliance, and C2M2 is well-suited for critical infrastructure.
It’s essential to take a tailored, strategic approach rather than defaulting to a one-size-fits-all model. For instance, a retail company might leverage NIST CSF for its adaptability, while a federal contractor may need CMMC 2.0 to meet government requirements. By aligning your maturity model selection with your business goals, you set the stage for sustainable security growth and measurable progress.
Step-by-Step Cybersecurity Maturity Assessment Process
Embarking on a cybersecurity maturity assessment can feel daunting, but breaking it into clear, manageable steps makes the journey approachable for any organization. By following a structured process, you’ll gain clarity on where you stand, where you need to go, and how to get there with confidence.
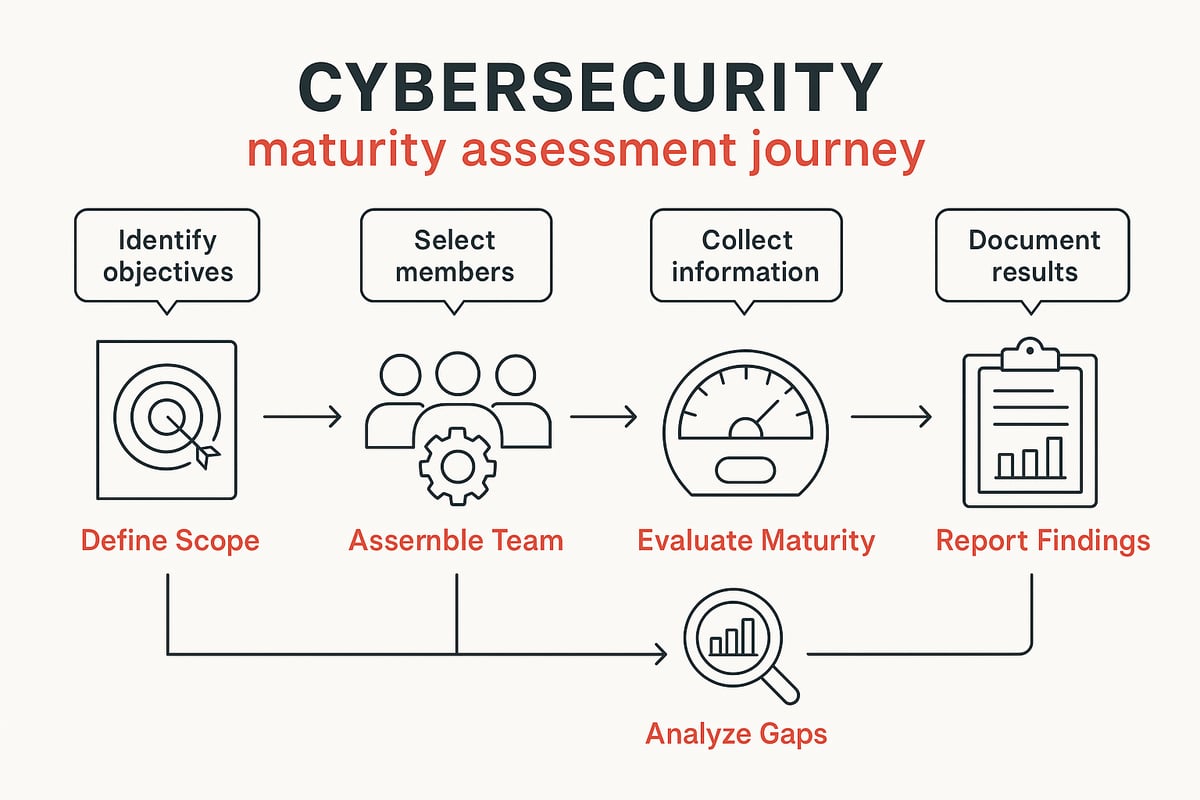
Step 1: Define Scope and Objectives
Start by clarifying why you’re assessing cybersecurity maturity. Is your main driver compliance, customer trust, or risk reduction? Understanding your motivation shapes the entire process.
Identify which business units, assets, and systems fall within your scope. Maybe you focus on cloud services, or perhaps you need to cover everything from endpoints to supply chain partners.
Set measurable objectives that align with your organization’s broader strategy. For example, you might aim to improve incident response or achieve a specific compliance milestone.
Engage key stakeholders early, such as CISOs, IT leads, compliance officers, and business executives. Remember, a successful cybersecurity maturity assessment should be seen as a continuous improvement journey, not a one-time event.
Step 2: Assemble the Assessment Team
A diverse team is crucial for an effective cybersecurity maturity assessment. Define clear roles for each participant:
- CISO or cybersecurity lead to oversee the process
- Security analysts and IT staff for technical expertise
- Compliance professionals to ensure regulatory alignment
- External assessors for unbiased perspectives
Encourage cross-functional collaboration so you get holistic insights, not just a technical snapshot. Assign ownership for data collection, interviews, and documentation to streamline the process.
Executive sponsorship helps ensure the team has the authority and resources needed to drive the cybersecurity maturity initiative forward.
Step 3: Gather Data and Evidence
With your team in place, it’s time to collect the facts. Inventory all assets, systems, and data flows relevant to your cybersecurity maturity goals.
Review existing policies, security controls, and records of past incidents. Use a mix of tools and techniques:
- Questionnaires for staff
- Technical scans for vulnerabilities
- Interviews to understand real-world practices
A systematic, data-driven approach helps surface gaps that might otherwise be missed. For instance, you might discover missing hardware inventories or insufficient data-at-rest protections. Comprehensive evidence gathering is the foundation of an accurate cybersecurity maturity assessment.
Step 4: Evaluate Against the Chosen Maturity Model
Now, map your collected evidence to the criteria of your selected maturity model. This could be a framework like NIST CSF, CMMC 2.0, or C2M2.
Assign maturity levels to each domain or outcome, often using a 1-5 scale. Scoring tools or digital platforms can help ensure consistency across business units.
Document strengths, weaknesses, and improvement areas. This step uncovers both technical and process gaps, providing a complete picture of current cybersecurity maturity.
For a deeper dive into actionable steps and model alignment, check out this Cybersecurity roadmap for organizations for practical guidance.
Step 5: Analyze Results and Prioritize Gaps
Summarize your findings in a format that makes sense for your audience. Use visualizations like heatmaps or dashboards to highlight risk concentrations and maturity gaps.
Prioritize remediation efforts based on risk, business impact, and any pressing regulatory deadlines. For example, if detection and response are lagging, focus there before tackling less critical areas.
Link mitigation planning to business key performance indicators. By aligning cybersecurity maturity improvements to what matters most for your organization, you maximize both impact and support.
Step 6: Report Findings to Stakeholders
Reporting is where your cybersecurity maturity assessment drives real change. Tailor your message for each audience: use clear, non-technical language for executives, and detailed recommendations for technical teams.
Highlight quick wins, significant risks, and strategic recommendations. Effective reporting not only secures buy-in but also helps allocate resources where they’re needed most.
When CISOs present maturity progress to the board, it shows commitment to resilience and provides a roadmap for ongoing improvement. Remember, transparency and clarity empower everyone to support the organization’s cybersecurity maturity journey.
Implementing a Cybersecurity Maturity Improvement Roadmap
Building a cybersecurity maturity improvement roadmap is about more than checking boxes. It’s a journey of ongoing progress, strategic planning, and uniting your team around shared security goals. Let’s break down how to turn assessment findings into action and foster a culture of resilience together.
Setting Strategic Goals and KPIs
After your assessment, translate insights into practical cybersecurity maturity goals. Start by aligning security objectives with your organization’s strategy and risk tolerance.
Define key performance indicators (KPIs) such as mean time to detect incidents, response speed, compliance rates, and user awareness scores. For example, you might aim to reduce incident response time by 30 percent within a year.
Choose goals that are specific, measurable, and tied to business outcomes. This clarity helps everyone see how cybersecurity maturity supports your broader mission.
Developing Action Plans and Milestones
Break down each goal into actionable projects, with clear tasks, deadlines, and ownership. Assign responsibility for every milestone to ensure accountability.
Prioritize actions that address high-risk or high-impact areas first. For instance, rolling out multi-factor authentication organization-wide can be a game-changer.
Remember, action plans should be flexible and adaptable. Review and update them as your cybersecurity maturity evolves or as new threats emerge.
Integrating Security into Business Processes
Embedding cybersecurity maturity into daily business operations transforms security from an IT concern into a company-wide value.
Integrate security checks into procurement, development, HR, and other core workflows. Encourage security champions within each business unit to promote awareness and best practices.
Fostering a culture where everyone plays a role in cybersecurity maturity leads to more sustainable, long-term results.
Leveraging Technology and Automation
The right tools can supercharge your cybersecurity maturity. Deploy solutions for monitoring, detection, and automated response to threats.
Automate routine tasks like patch management and access reviews. Evaluate platforms that support your maturity goals and offer visibility across your environment.
Technology should amplify your team’s efforts, not replace strategic thinking. For structured guidance, explore Cyber risk framework essentials to align your roadmap with proven frameworks.
Training, Communication, and Change Management
People are central to cybersecurity maturity. Provide targeted training for both technical staff and end users.
Communicate the reasons behind changes to build trust and secure buy-in. Use engaging methods like phishing simulations and tabletop exercises to reinforce learning.
Change management is ongoing. Celebrate quick wins and encourage feedback to keep the momentum going.
Measuring Progress and Iterating
Regularly review your KPIs and track progress on milestones. Adjust your roadmap as your business grows or new threats appear.
Make cybersecurity maturity assessments a recurring event, not a one-off project. After incidents or major changes, revisit your goals and update strategies.
Continuous improvement is the key to staying resilient. Every cycle brings your organization closer to true cybersecurity maturity.
LarsBirkeland.com: Practical Guidance for Cybersecurity Leaders
Looking for a trusted place to grow your cybersecurity maturity journey? LarsBirkeland.com is here to help CISOs, IT professionals, and business leaders turn challenges into opportunities. The site blends practical frameworks, step-by-step guides, and genuine community support so you never feel alone navigating complex risks.
You will find real-world strategies that help you move past theory and into action. The focus is always on transforming technical know-how into programs that drive progress, keep your organization resilient, and communicate risk with clarity.
Explore resources like the CISO LaunchPad, leadership templates, and hands-on playbooks built for the unique challenges of 2026. Each tool is crafted to make sure your cybersecurity maturity program is not just compliant but also a true business enabler.
Ready to take the next step? Join a community dedicated to sharing insights, supporting each other, and building future-ready organizations that thrive no matter what the threat landscape brings.
Continuous Cybersecurity Maturity: Monitoring, Reassessment, and Evolution
Staying secure in 2026 means treating cybersecurity maturity as a living process, not a one-time project. We need to adapt, learn, and grow stronger with every new challenge. Let’s explore how ongoing monitoring, regular reassessment, and a culture of improvement keep us ahead of threats and resilient in the face of change.
Establishing Ongoing Monitoring and Metrics
Ongoing monitoring forms the heartbeat of cybersecurity maturity. Dashboards and automated alerts help us track key security indicators across our organization. By watching compliance levels, incident trends, and risk exposure in real time, we gain insight into where we stand and where we need to improve.
For example, platforms that track maturity across business units can highlight strengths and reveal hidden gaps. Many teams use frameworks like the Cybersecurity Capability Maturity Model (C2M2) to guide their monitoring and reporting strategies. Continuous threat exposure management is now considered a best practice, ensuring we’re always alert to new risks and ready to respond.
Scheduling Regular Maturity Assessments
To keep cybersecurity maturity on track, regular reassessments are a must. Setting a clear cadence—whether annual, bi-annual, or triggered by major events—helps us stay aligned with business changes and emerging threats. Updating the assessment scope ensures nothing slips through the cracks as our organization evolves.
After mergers, regulatory updates, or significant incidents, it’s vital to revisit our maturity posture. Competitors agree that maturity is never static, and ongoing reviews are essential for resilience. By making reassessment part of our routine, we build confidence and foster a proactive security mindset.
Adapting to New Threats and Technologies
Cybersecurity maturity thrives on adaptability. We need to stay informed about new cyber threats, regulatory shifts, and industry trends. Integrating emerging technologies—such as AI-driven security tools, zero-trust architectures, and enhanced cloud protections —helps us stay one step ahead.
Responding to modern risks, such as supply chain attacks, means enhancing vendor risk management and updating our defenses. Flexibility and a willingness to evolve are hallmarks of true maturity. By embracing change, we transform challenges into opportunities for growth.
Fostering a Culture of Continuous Improvement
A strong cybersecurity maturity program is built on a culture of learning and collaboration. Encouraging feedback and sharing lessons from incidents or near-misses creates space for innovation. Rewarding proactive security behaviors helps everyone feel invested in our shared mission.
Programs like security champions and cross-functional workshops empower teams to solve problems together. When we celebrate progress and support each other, we build lasting resilience. Organizational learning and agility become our greatest assets in navigating the ever-shifting security landscape.
We’ve covered a lot of ground together, turning complex cybersecurity maturity steps into something practical, approachable, and genuinely achievable.
If you’re looking for more than just theory and want a supportive group that “gets it” when it comes to real-world challenges and strategies, you’re not alone. Let’s keep growing and learning together.
I invite you to join us in the Join CISO Launchpad Community where you’ll find peers, resources, and expert insights designed to help you put these steps into action and build a future-ready security program. We’re in this together!