Cyber threats in 2026 are evolving rapidly, targeting organizations of all sizes and industries. The stakes have never been higher for those responsible for protecting data and operations.
This comprehensive cybersecurity roadmap is designed to guide you through every step needed to build, strengthen, and future-proof your defenses for the years ahead.
Whether you are an IT professional, security leader, or business owner, this guide will equip you with practical steps, expert insights, and real-world strategies.
Inside, you will discover foundational principles, must-have technical skills, advanced tactics, compliance essentials, and growth opportunities, all mapped for today’s ever-changing landscape.
Let’s get started and turn this guide into your go-to blueprint for a resilient and secure future.
Step 1: Establishing Your Cybersecurity Foundation
Building a strong cybersecurity foundation is the first step on your cybersecurity roadmap. Let’s break it down into clear, actionable steps so you can get started with confidence.
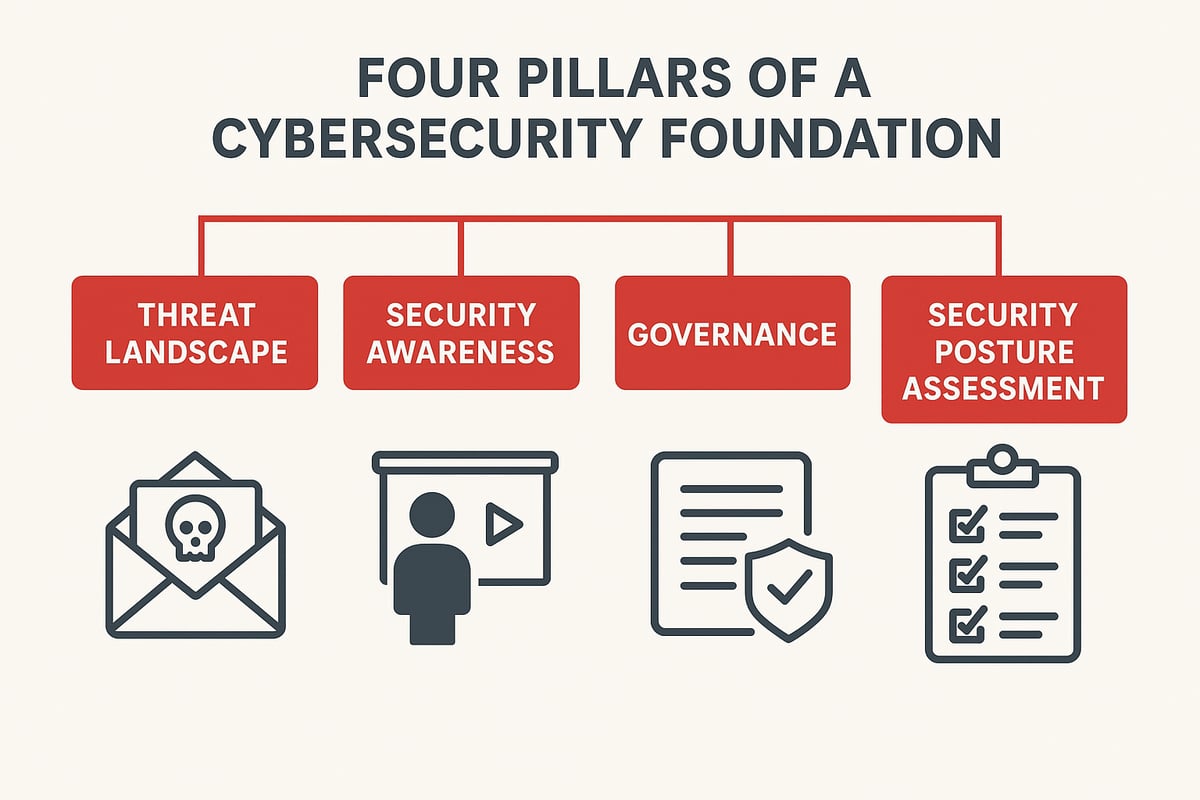
Understanding the Modern Threat Landscape
In 2026, the threat landscape is more dynamic than ever. Cybercriminals are using ransomware, supply chain attacks, and AI-driven intrusions to target businesses large and small. Global ransomware losses are expected to surpass $30 billion, making it a top concern for every cybersecurity roadmap.
Recent breaches have shown how quickly attackers adapt. For example, phishing tactics have evolved between 2023 and 2026, now using AI to craft convincing messages that bypass traditional filters. Organizations need to keep up with these changes by staying informed and leveraging threat intelligence.
High-profile incidents highlight the importance of vigilance. By understanding these trends, you can anticipate risks and protect your organization more effectively.
Building Cybersecurity Awareness and Culture
A successful cybersecurity roadmap starts with people. Employees are your first line of defense, so regular security awareness training is essential. Companies that invest in ongoing education see 70% fewer successful phishing attacks, according to 2025 data.
Start by establishing clear security policies and acceptable use guidelines. Make sure everyone knows their responsibilities and feels empowered to report suspicious activity. Fostering a culture of shared responsibility turns security into a team effort.
Leadership plays a key role here. When leaders prioritize cybersecurity, it sets the tone for everyone. Encourage open communication and celebrate positive security behaviors to build trust and resilience.
Defining Security Goals and Governance
Setting clear goals is vital for your cybersecurity roadmap. Align your objectives with your business strategy, and make sure everyone understands their roles, from the CISO to IT staff and end users.
Create a governance framework that outlines policies, procedures, and accountability. Documenting these elements helps everyone stay on the same page and ensures compliance with industry standards. Many organizations use the Cybersecurity strategy essentials as a starting point for building their roadmap.
For structure, consider adopting the NIST Cybersecurity Framework as a baseline. This approach helps you measure progress and identify gaps, making your efforts more effective and sustainable. Strong governance keeps your program adaptable and ready for future challenges.
Assessing Your Current Security Posture
Before you can move forward, you need to know where you stand. Every cybersecurity roadmap should include a thorough risk assessment. Start by identifying your critical assets and mapping out data flows.
Use maturity models and scorecards, like the Public Power Cybersecurity Scorecard, to benchmark your current state. A gap analysis will show you how your security measures compare to industry standards and where improvements are needed.
A self-assessment checklist can help you visualize your progress. Regular reviews keep your roadmap up-to-date and ensure your organization is always ready to respond to new threats.
Step 2: Developing Core Technical and Operational Capabilities
Building strong technical and operational capabilities is the heart of any effective cybersecurity roadmap. This step transforms strategy into action, ensuring defenses are robust, adaptive, and ready for emerging threats. Let’s break down the essential areas every organization should master to stay ahead in 2026.
Network and Endpoint Security Fundamentals
Securing your digital perimeter is a crucial part of any cybersecurity roadmap. In 2026, attackers exploit both network gaps and vulnerable endpoints, so layered defenses are essential.
Start by segmenting your network to limit access between sensitive areas. Deploy next-gen firewalls, intrusion detection, and prevention systems. Don’t forget endpoints—ensure every device has up-to-date antivirus, endpoint detection and response (EDR), and regular patch management.
- Use network segmentation to block lateral movement.
- Implement robust firewall policies.
- Schedule regular vulnerability scans for all endpoints.
Recent breaches have shown that organizations with segmented networks contained threats faster, minimizing damage. By embedding these best practices into your cybersecurity roadmap, you set a solid first line of defense.
Identity and Access Management (IAM)
Identity is the new security perimeter. A modern cybersecurity roadmap must include strong IAM to control who has access to what, and when.
Apply the principle of least privilege across all systems. Use multi-factor authentication (MFA) and, where possible, biometrics to strengthen logins. Regularly review user access and swiftly revoke credentials for departing staff.
- Enforce zero-trust policies for all users and devices.
- Automate access reviews and user provisioning.
- Audit privileged accounts frequently.
Adopting zero trust has significantly reduced insider threats for organizations. An IAM-focused cybersecurity roadmap not only blocks external attackers but also curbs risks from within.
Data Protection and Privacy
Data is the crown jewel in your cybersecurity roadmap. Protecting sensitive information requires a mix of technology and policy.
Classify data based on sensitivity and apply encryption both at rest and in transit. Store backups securely, and design systems with privacy in mind from the outset. Stay compliant with regulations like GDPR, CCPA, and new 2026 standards.
- Encrypt sensitive files and databases.
- Use secure protocols for data transmission.
- Regularly review privacy policies and user consent flows.
By prioritizing data protection in your cybersecurity roadmap, you reduce the risk of costly breaches and regulatory penalties.
Secure Configuration and Hardening
Misconfigurations remain a top cause of breaches. Your cybersecurity roadmap should include strict baseline configurations for servers, endpoints, and cloud resources.
Follow well-established hardening guides, such as the NIST Cybersecurity Framework 2.0, to eliminate unnecessary services and lock down settings. Automate configuration management to maintain consistency and catch drift.
- Apply CIS Benchmarks for all operating systems.
- Schedule automated vulnerability scans.
- Patch and remediate findings quickly.
A secure configuration strategy within your cybersecurity roadmap ensures attackers have fewer points of entry and reduces your overall risk profile.
Monitoring, Detection, and Incident Response
No cybersecurity roadmap is complete without real-time monitoring and a clear incident response plan. Early detection and rapid response can make the difference between a contained incident and a major breach.
Build or partner with a Security Operations Center (SOC). Implement a Security Information and Event Management (SIEM) system for log collection and analysis. Practice incident response with tabletop exercises to ensure your team is ready.
- Set up alerts for suspicious activity.
- Conduct regular incident response drills.
- Document and refine your response plan after each incident.
Organizations with strong monitoring and response reduce breach costs and recovery times. Make these capabilities a core part of your cybersecurity roadmap.
LarsBirkeland.com: Practical Cybersecurity Leadership and Strategy
For step-by-step playbooks and proven frameworks, LarsBirkeland.com is an invaluable resource. Here, you can find actionable guides to help integrate each technical and operational pillar into your cybersecurity roadmap.
Join a supportive community of IT professionals and security leaders who are committed to clarity, confidence, and strategic action. Together, we can future-proof our organizations and build a safer digital world.
Step 3: Advancing to Specialized and Emerging Domains
As we reach the next phase of your cybersecurity roadmap, it is time to tackle the specialized and fast-evolving domains that are shaping our digital landscape. These areas demand targeted strategies, modern tools, and a mindset ready for rapid change. Let us explore how to secure the cloud, build resilient applications, protect OT and IoT, leverage AI, and manage third-party risks.
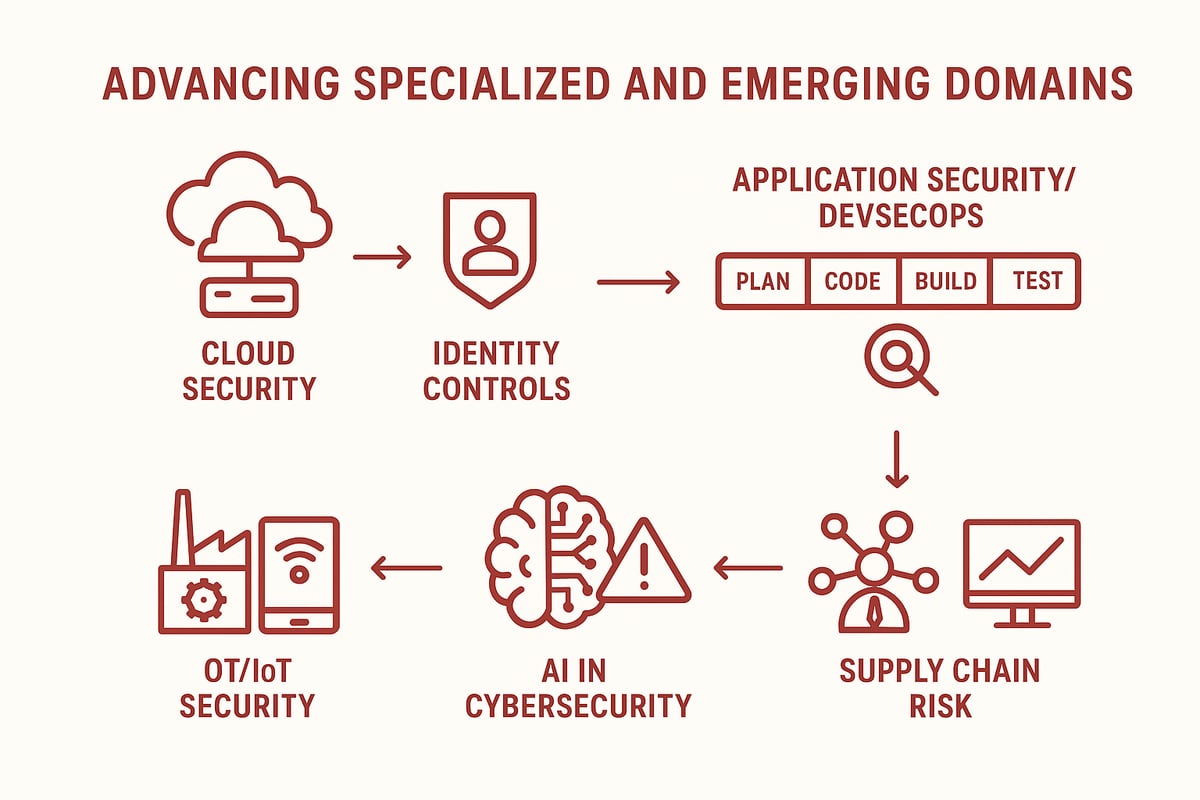
Cloud Security Strategy
Cloud adoption continues to accelerate, making robust cloud security a critical milestone on any cybersecurity roadmap. Organizations are increasingly operating in hybrid and multi-cloud environments, which introduces unique challenges around data visibility and control.
Securing your cloud footprint requires:
- Strong identity and access management, including least-privilege principles.
- Continuous monitoring for misconfigurations and unauthorized access.
- Encryption for data in transit and at rest.
- Regular audits of storage buckets and service permissions.
Cloud-specific threats, such as data exposure from unsecured storage or third-party integrations, have led to damaging breaches. For example, a 2025 incident involving unsecured storage buckets exposed millions of records, highlighting the need for proactive strategies. For further insights, explore this cloud security strategy guide to strengthen your approach.
Application Security and DevSecOps
Software is everywhere, and its security is essential to your cybersecurity roadmap. Embedding security into the software development lifecycle (SDLC) helps prevent vulnerabilities before they reach production.
Key practices include:
- Automated code scanning for vulnerabilities and dependencies.
- Secure CI/CD pipelines with built-in checks.
- Early integration of security requirements, known as “shift-left” security.
By prioritizing DevSecOps, organizations have reduced vulnerabilities by 35 percent. Real-world results show that teams adopting these practices detect and remediate flaws much earlier, reducing risk and costs.
Operational Technology (OT) and IoT Security
Industrial systems and IoT devices introduce unique risks to your cybersecurity roadmap. OT networks, found in utilities and manufacturing, control critical infrastructure and require specialized protections.
Effective steps include:
- Segmenting OT networks from IT environments.
- Maintaining an up-to-date inventory of connected devices.
- Regularly patching and securely decommissioning outdated IoT devices.
Utilities adopting OT-specific frameworks have seen measurable improvements in resilience. Building these controls into your roadmap ensures continuous protection for both digital and physical assets.
AI and Automation in Cybersecurity
Artificial intelligence is revolutionizing every part of the cybersecurity roadmap. AI-driven tools can detect threats faster and automate response actions, giving defenders an edge against sophisticated attackers.
However, AI introduces new risks, including adversarial attacks and data poisoning. It is vital to:
- Validate AI models and monitor for manipulation.
- Automate repetitive security tasks without sacrificing oversight.
- Train teams to understand both the power and limits of AI.
Organizations deploying AI-driven Security Operations Centers (SOCs) have improved detection speed and accuracy, making them more resilient to evolving threats.
Supply Chain and Third-Party Risk Management
Your cybersecurity roadmap is only as strong as its weakest link. Third-party vendors and supply chain partners can introduce vulnerabilities if not properly managed.
Best practices for this domain:
- Assess vendor security posture before onboarding.
- Include security requirements in contracts.
- Continuously monitor for changes in vendor risk.
The 2026 landscape is shaped by incidents like the SolarWinds breach, which had global repercussions. By integrating thorough third-party risk management into your roadmap, you help safeguard your organization from cascading risks and ensure business continuity.
Step 4: Compliance, Risk Management, and Business Continuity
Building resilience is more than just protecting data—it’s about setting up your entire organization for long-term security and adaptability. In this step of your cybersecurity roadmap, we focus on compliance, risk management, and making sure your business can bounce back from any challenge.
Navigating Regulatory Requirements
Regulatory demands in 2026 are more complex than ever, and staying compliant is a non-negotiable part of any cybersecurity roadmap. Organizations must keep pace with evolving laws like the NIS2 Directive, updated GDPR, and sector-specific mandates.
To succeed, map your security controls to recognized frameworks such as NIST or ISO 27001. This approach ensures your efforts are structured and audit-ready. Documentation is key—maintain clear records of your policies and procedures.
For utilities and critical infrastructure, compliance with DOE guidelines is a must. To dive deeper into building strong compliance structures, check out this Governance and compliance frameworks resource for actionable steps and templates.
Enterprise Risk Management (ERM)
Integrating cyber risk into your overall business strategy is essential for a robust cybersecurity roadmap. ERM helps organizations see the bigger picture, making it possible to identify threats, set risk appetite, and prioritize investments.
Quantifying cyber risk empowers leadership to make informed decisions. Models like FAIR translate technical risks into financial terms that executives understand. This clarity drives smarter resource allocation and strengthens your defense posture.
Regular risk assessments and open communication across teams ensure your roadmap stays aligned with business goals and adapts to new threats.
Business Continuity and Disaster Recovery
Even with the best controls in place, incidents can still happen. A solid business continuity and disaster recovery plan is a cornerstone of any cybersecurity roadmap. Start by identifying critical processes and data, then build plans that keep your business running during disruptions.
Test these plans regularly, and make sure offline backups and immutable storage are in place to resist ransomware. In 2025, organizations with robust BCPs demonstrated rapid recovery, minimizing downtime and financial loss.
Resilience isn’t just about prevention; it’s about being ready to respond and recover, no matter what.
Incident Reporting and Legal Considerations
Timely incident reporting is now a legal requirement under many regulations, making it a vital part of your cybersecurity roadmap. Understand mandatory breach notification timelines and document your processes in advance.
Work closely with legal counsel to interpret obligations under laws like NIS2, and ensure your response plans reflect these requirements.
Reporting quickly and accurately not only avoids penalties but also strengthens trust with customers and regulators. Preparation here can make a critical difference during a crisis.
Cyber Insurance and Financial Risk Transfer
Cyber insurance is now a key tool for risk transfer, rounding out your cybersecurity roadmap. Evaluate your coverage annually to ensure it matches the evolving threat landscape and your organization’s needs.
Policies in 2026 often require specific controls and may exclude certain risks, so review requirements carefully.
Trends show rising premiums and stricter claims processes after major incidents in 2025. By aligning insurance with your risk management strategy, you protect your business from unexpected financial shocks.
Step 5: Continuous Improvement, Professional Growth, and Future Trends
The journey along your cybersecurity roadmap does not end once the basics are in place. Continuous improvement is the heartbeat of resilient security. Together, let us explore how ongoing learning, collaboration, and future planning keep us one step ahead of evolving threats.
Building a Culture of Continuous Improvement
A truly effective cybersecurity roadmap relies on a mindset that embraces change and learning. Regular reviews of your security program help catch gaps before they become risks. Organizations that commit to quarterly security assessments often spot and resolve new vulnerabilities 50 percent faster than those with annual reviews.
Encourage your team to share lessons learned from incidents, near misses, and industry news. When we create space for open discussion, we foster an environment where everyone feels empowered to suggest improvements. This culture of curiosity and adaptability forms the cornerstone of any successful cybersecurity roadmap.
Security Training, Certifications, and Upskilling
Staying at the forefront of cybersecurity means making professional growth a priority. Your cybersecurity roadmap should include ongoing training for every team member. Top certifications like CISSP, CISM, and CompTIA Security+ remain highly valued in 2026, along with cloud security credentials.
Encourage hands-on learning through labs and Capture The Flag (CTF) competitions. These real-world exercises sharpen skills and boost team confidence. Did you know that SOC analysts who participate in CTFs consistently outperform their peers? Investing in upskilling keeps your cybersecurity roadmap dynamic and aligned with the latest threats.
Leveraging Cybersecurity Communities and Collaboration
No one succeeds in security alone. Collaborating with others strengthens every cybersecurity roadmap. By joining information sharing and analysis centers (ISACs) or industry groups, you gain access to fresh threat intelligence and proven defense strategies.
Seek out mentorship and peer learning opportunities. Sharing experiences with fellow professionals helps us avoid common pitfalls and discover creative solutions. The collaborative approach used by the Public Power Cybersecurity Roadmap is a great example of how a community can drive collective resilience.
Measuring Success and Reporting to Stakeholders
How do you know if your cybersecurity roadmap is making a difference? Tracking key metrics is essential. Measure your mean time to detect and respond, employee awareness rates, and compliance scores. Scorecard frameworks provide a clear, objective view of progress.
Transparent reporting builds trust and helps secure ongoing support for your cybersecurity roadmap.
Preparing for the Future: Trends and Predictions for 2026+
Looking ahead, the cybersecurity roadmap must account for emerging trends. Quantum computing, AI-powered attacks, and increasingly complex regulations are all reshaping the landscape. Staying agile and informed is crucial.
For a deeper dive into what’s next, explore the Cybersecurity Trends in 2026. By anticipating new threat vectors and regulatory shifts, your cybersecurity roadmap will remain a reliable blueprint for resilience and growth.
After diving into this roadmap and exploring what it takes to build a resilient security program, you’re probably realizing just how much there is to learn and how valuable it is to connect with others on the same journey. We all face similar challenges, from staying ahead of threats to making smart decisions when time and resources are tight.
If you’re looking for ongoing support, practical advice, and a community that truly understands the ups and downs of cybersecurity leadership, let’s keep this momentum going together. Join us in the CISO Launchpad Community.