Cyber threats have exploded in both scale and sophistication, with cyberattacks skyrocketing by over 600% during recent global disruptions. The average ransomware payment has soared past $572,000, putting every organization at risk.
From high-profile breaches at tech giants to attacks crippling small businesses, no one is immune. A single misstep can lead to devastating data loss, regulatory fines, and lasting damage to your reputation.
But there is hope. By building a proactive cybersecurity strategy, you can protect your business, earn customer trust, and ensure continuity even in a turbulent digital world.
This guide walks you through the evolving threat landscape, compliance demands, and proven steps to future-proof your security posture. Ready to transform your approach and build true resilience? Let’s get started.
Understanding the 2026 Cyber Threat Landscape
Staying ahead in cybersecurity strategy means understanding how the threat landscape is evolving. In 2026, attackers are more organized and creative, using advanced tactics to target organizations of every size. Let’s break down what’s happening, how it impacts business, and what trends you need to watch to inform a resilient cybersecurity strategy.
Evolving Attack Vectors and Tactics
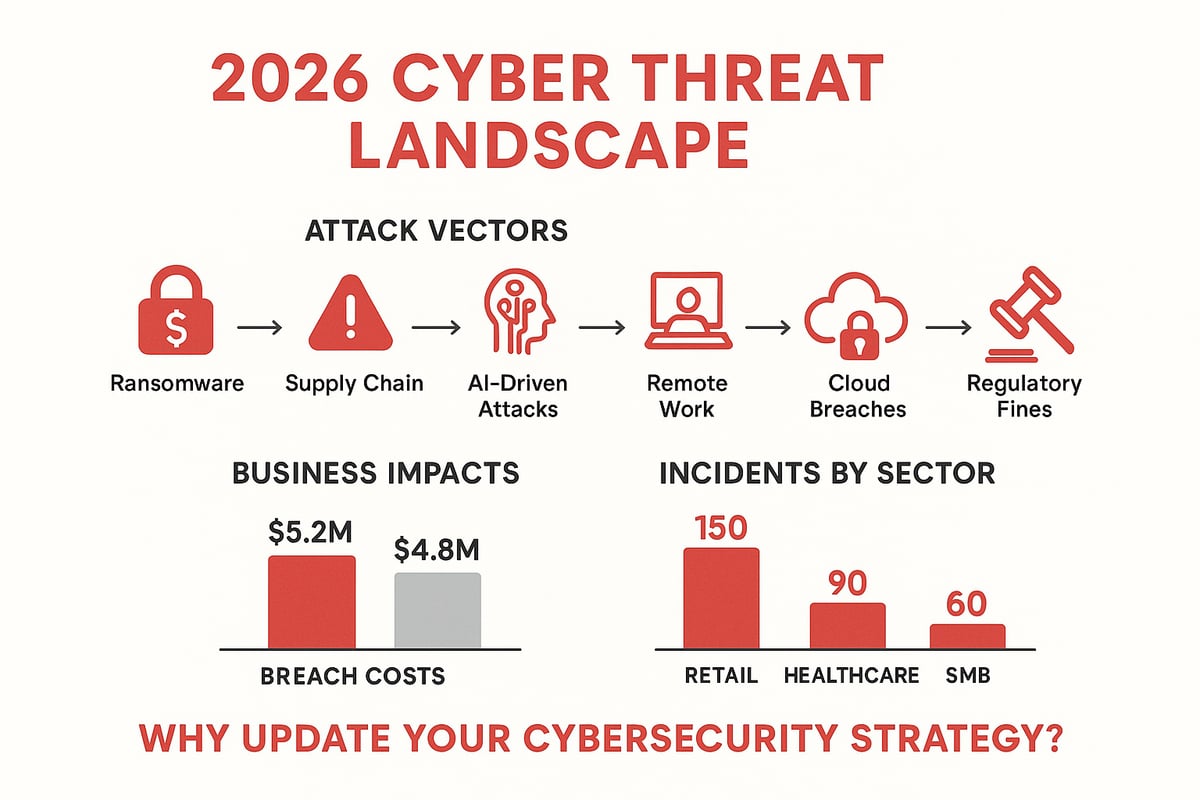
Attackers in 2026 are more persistent than ever. Ransomware remains a top threat, evolving to target backups and cloud data, with recent incidents reminding us of the scale—think SolarWinds and Colonial Pipeline. Supply chain attacks have grown, with vulnerabilities in third-party software providing backdoors into otherwise well-defended networks.
Artificial intelligence is now a double-edged sword. While it powers defense, it also fuels automated attacks that scan for misconfigured cloud services, attack IoT devices, and exploit remote work setups. Social engineering continues to rise, with 43% of attacks now hitting SMBs, not just large enterprises.
Notable breaches from 2024 to 2025, such as Microsoft Azure’s SSRF vulnerabilities and the massive Twitter data leaks, highlight the risk of zero-day exploits and cloud misconfigurations. Attackers also use deepfakes for phishing, credential stuffing to hijack accounts, and mobile malware to compromise remote workers.
The financial and reputational risks tied to regulatory penalties have never been higher, with frameworks like GDPR and HIPAA driving up compliance expectations. For a deeper dive into these evolving threats, check out Cybersecurity Trends in 2026.
Impact on Business Operations and Reputation
The fallout of a breach can be devastating. The average cost of a breach continues to climb, with downtime and recovery draining resources and threatening business continuity. Retail and healthcare are especially hard-hit—89% of healthcare organizations experienced breaches in just two years, showing that no sector is immune.
Here’s how breaches impact organizations:
| Impact Area | Consequence |
|---|---|
| Financial | Soaring costs, ransom payments, lost revenue |
| Operational | Downtime, disrupted services, recovery expenses |
| Reputational | Loss of trust, damaged brand, lost customers |
| Legal/Compliance | Fines, lawsuits, regulatory scrutiny |
Legal and compliance ramifications can be severe. For example, the Twitter data leak affected 200 million users, resulting in public outcry, regulatory investigation, and a lasting dent in user trust. These real-world events reinforce why every cybersecurity strategy must prioritize both prevention and rapid response.
Key Trends for 2026
Several trends are reshaping the cybersecurity strategy conversation. The remote and hybrid workforce has exploded, with IDC forecasting 93.5 million US mobile workers by 2024. This shift increases the attack surface, requiring new approaches to secure distributed teams and devices.
Cloud-native applications and distributed data storage are now standard, but they come with unique risks. Misconfigurations and poorly secured cloud environments are frequent breach entry points, making robust cloud security a central part of any cybersecurity strategy.
Regulatory scrutiny is intensifying, and compliance requirements are evolving. Organizations are facing more audits, higher penalties, and stricter mandates. Meanwhile, the surge in attacks has pushed up cyber insurance claims and premiums, forcing businesses to rethink risk management.
Staying aware of these trends helps organizations future-proof their cybersecurity strategy, ensuring resilience in a fast-changing digital world.
Core Principles of a Modern Cybersecurity Strategy
Building a robust cybersecurity strategy in 2026 means more than just installing firewalls or antivirus tools. It’s about layering defenses, aligning with business needs, and staying agile as new threats emerge. Let’s explore the foundational principles that help us stay one step ahead of attackers and protect what matters most.
Defense in Depth and Zero Trust
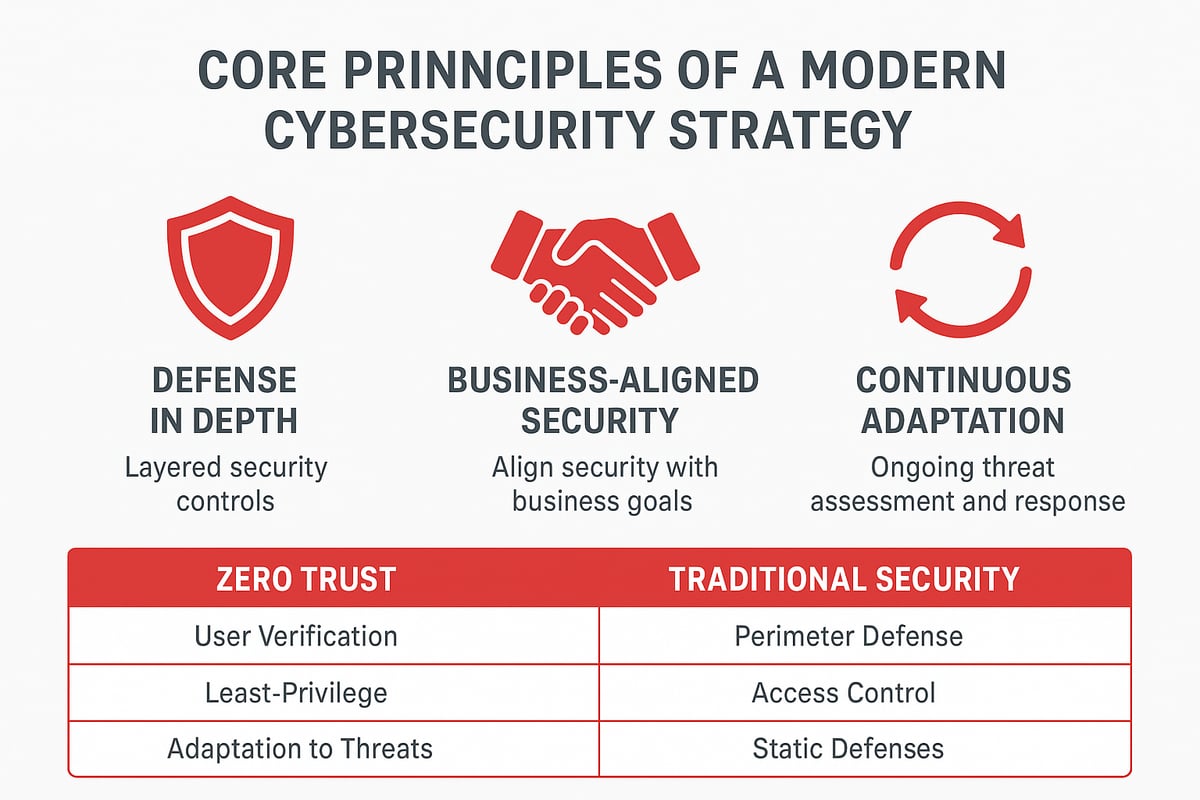
A modern cybersecurity strategy starts with defense in depth, which means setting up multiple layers of security controls to make it harder for attackers to reach your valuable data. Instead of relying on a single barrier, you create a series of hurdles—like firewalls, endpoint protection, and network segmentation. This way, even if one layer fails, the others stand guard.
Zero Trust has become a must-have model: never trust, always verify. No user or device is trusted automatically, whether inside or outside your network. Multifactor authentication, continuous monitoring, and least-privilege access are all part of this approach.
Here’s a quick comparison:
| Principle | Traditional Security | Zero Trust |
|---|---|---|
| Trust Model | Trust inside | Never trust, always verify |
| Access Controls | Perimeter-based | Identity & context-based |
| Monitoring | Periodic | Continuous |
Many organizations use frameworks like NIST or ISO 27001 to guide their layered defenses. For a deeper dive into these frameworks and how they support a resilient cybersecurity strategy, check out the Core cybersecurity frameworks overview.
Business-Aligned Security Posture
A successful cybersecurity strategy doesn’t operate in a vacuum. Instead, it works hand-in-hand with your business goals. We need to prioritize protecting the data, applications, and systems that matter most to our organization’s mission.
Adopting a risk-based approach helps us focus resources where they have the most impact. This means identifying critical assets, evaluating threats, and balancing protection with business needs. It’s important to communicate security risks in clear, relatable terms so leaders and stakeholders understand why certain investments are needed.
For example, pairing endpoint security tools with identity management can reduce both internal and external risks. This business-aligned mindset ensures security is seen as an enabler, not a barrier.
Continuous Adaptation and Learning
The threat landscape is always changing, so a resilient cybersecurity strategy must keep up. Regularly reviewing and updating security policies helps address new risks, whether from cloud adoption, remote work, or emerging technologies.
Building a security-aware culture is crucial. When everyone—from interns to executives—understands the basics, the whole organization becomes more resilient.
Leveraging threat intelligence and real-time analytics allows us to spot unusual activity early and respond quickly.
Learning from incidents, staying updated on trends, and being open to new tools and techniques keep our defenses strong. Adapting is not just a technical exercise—it’s a mindset that prepares us for whatever comes next.
Step-by-Step Guide: Building Cyber Resilience in 2026
Building a robust cybersecurity strategy in 2026 can feel overwhelming, but breaking it into actionable steps makes it manageable for any organization. By following this step-by-step guide, you’ll empower your team to proactively defend against threats, minimize risk, and strengthen business continuity.
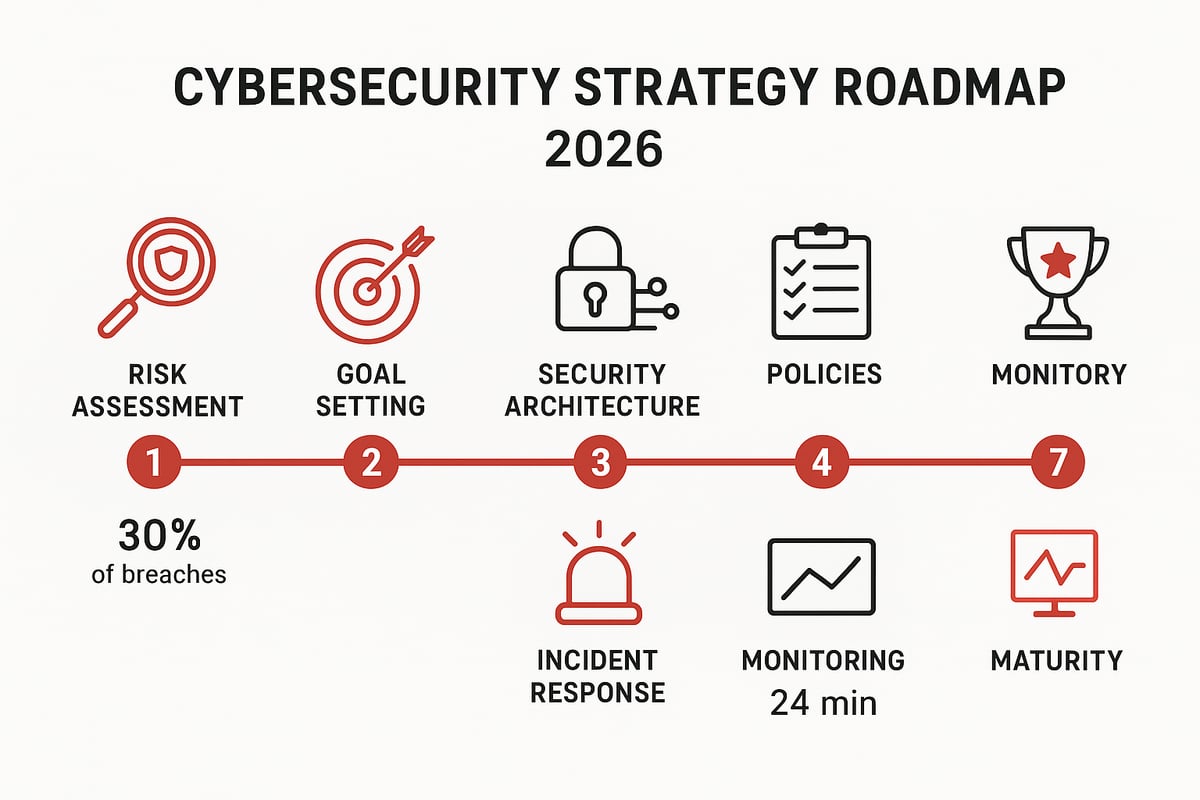
Step 1: Conduct a Comprehensive Risk Assessment
Every cybersecurity strategy must begin with a deep understanding of your organization’s unique risks. Start by mapping out all digital assets, including hardware, software, data flows, and business-critical systems. Categorize these assets by value and sensitivity.
Next, evaluate current vulnerabilities and your overall attack surface. Consider both internal and external threats, such as ransomware, phishing, and supply chain attacks. Leverage industry frameworks like NIST, ISO 27001, or CIS Controls to ensure a structured approach.
Quantify the potential impact and likelihood of various cyber risks. Include third-party and supply chain risk analysis, as attacks on vendors can quickly cascade to your environment. For example, the Kaseya ransomware attack on managed service providers exposed thousands of downstream clients.
In just six months of 2021, 1,767 publicly reported breaches led to 18.8 billion records exposed, highlighting the urgency of risk management. For a detailed roadmap on this process, check out Cybersecurity risk management fundamentals.
A thorough risk assessment is the cornerstone of any effective cybersecurity strategy, guiding every action that follows.
Step 2: Set Clear Security Goals and KPIs
With your risks identified, set measurable objectives aligned with your organization’s priorities. These goals should reflect both compliance needs and business outcomes, such as reducing incident response time or achieving regulatory certification.
Establish baseline metrics for your current security posture. Use tools like Gartner’s IT Score or a CISO effectiveness diagnostic to determine your maturity level. Involve stakeholders from IT, legal, finance, and operations to ensure buy-in and shared accountability.
For example, a healthcare provider might set goals like HIPAA compliance and zero critical vulnerabilities within six months. Define key performance indicators (KPIs) to track progress, such as:
- Number of incidents detected and contained
- Time to remediate threats
- Percentage of employees trained on security policies
Communicate these metrics in clear business language so executives and the board understand the value of your cybersecurity strategy.
Step 3: Design and Implement Security Architecture
A resilient cybersecurity strategy requires a strong, layered security architecture. Select frameworks such as NIST CSF, Zero Trust, or Defense in Depth to guide your design. Integrate layered controls, including network segmentation, endpoint protection, identity and access management, and encryption.
Securing hybrid and multi-cloud environments is critical in 2026. Address cloud misconfiguration risks by automating configuration checks and using cloud-native security tools. Implement continuous monitoring, Security Information and Event Management (SIEM), and advanced threat detection solutions.
Remote access is now standard, so protect it with VPNs, multifactor authentication, and device management. For small and midsize businesses, solutions like Microsoft Defender for Business offer affordable endpoint protection.
Legacy systems often introduce vulnerabilities. Prioritize timely patching and segment these systems from the rest of your network. By building a security architecture tailored to your needs, you make your cybersecurity strategy more effective and adaptable.
Step 4: Develop Robust Security Policies and Governance
Strong policies and effective governance are essential pillars of any cybersecurity strategy. Begin by drafting clear, comprehensive information security policies covering acceptable use, incident response, and data classification.
Make sure your policies reflect the realities of remote work, bring-your-own-device (BYOD) practices, and cloud adoption. Regularly review and update policies to keep pace with regulatory changes, such as GDPR, NIS2, or CCPA.
Train employees on security best practices and ensure everyone understands their responsibilities. Implement governance structures, such as appointing a Chief Information Security Officer (CISO), forming security committees, and establishing reporting lines.
Policy failures have led to significant breaches in both healthcare and financial sectors. Use policy templates and checklists to maintain consistency and compliance. Embedding governance into your cybersecurity strategy ensures accountability and ongoing improvement.
Step 5: Build a Risk Management and Incident Response Plan
Proactive risk management is vital for any cybersecurity strategy. Identify, assess, and prioritize risks, creating a detailed risk register to track them over time. Develop incident response playbooks for various scenarios, such as ransomware, distributed denial of service (DDoS), and insider threats.
Establish clear escalation paths and communication protocols. Regularly test your response plans with tabletop exercises and simulations to uncover gaps and improve readiness. Integrate your incident response with business continuity and disaster recovery planning.
For example, the SolarWinds supply chain attack exposed weaknesses in incident detection and supplier management. Ensure your plan aligns with industry regulations and reporting requirements for timely notification.
A well-practiced incident response plan helps your team respond quickly and effectively, minimizing the impact of any breach on your organization’s cybersecurity strategy.
Step 6: Implement, Monitor, and Optimize Security Controls
Once your security architecture and policies are in place, deploy the necessary security technologies and controls. Monitor their effectiveness using your established KPIs and adopt a cycle of continuous improvement.
Leverage real-time threat intelligence feeds and analytics to stay ahead of attackers. Regularly conduct vulnerability assessments and penetration tests to identify and remediate gaps. Automate patch management and incident detection where possible, especially in larger environments.
For instance, AI-based tools can detect anomalies and alert security teams to suspicious activity. Adjust your controls as threats evolve and as your business changes.
By actively monitoring and optimizing controls, your cybersecurity strategy remains agile and effective in the face of new risks.
Step 7: Evaluate, Report, and Mature Your Security Program
Continuous evaluation is the final piece of a successful cybersecurity strategy. Conduct periodic reviews and audits of your entire security program. Use maturity models like Gartner Score or NIST CSF tiers to benchmark your progress.
Report outcomes and risk posture to executives and the board using clear business terms. Foster a culture of ongoing learning by soliciting feedback from stakeholders and integrating lessons learned from incidents.
Organizations with mature cybersecurity programs experience fewer and less severe breaches. Plan for future investments in emerging technologies, such as AI-driven defense or quantum-safe encryption.
By embracing continuous improvement, your cybersecurity strategy will adapt and thrive—no matter what the future holds.
Special Considerations for Enterprises vs. SMBs
In the world of cybersecurity strategy, one size never fits all. Both enterprises and SMBs face mounting threats, but their needs, resources, and approaches can be very different. Let’s explore how organizations of every size can shape a cybersecurity strategy that works for them.
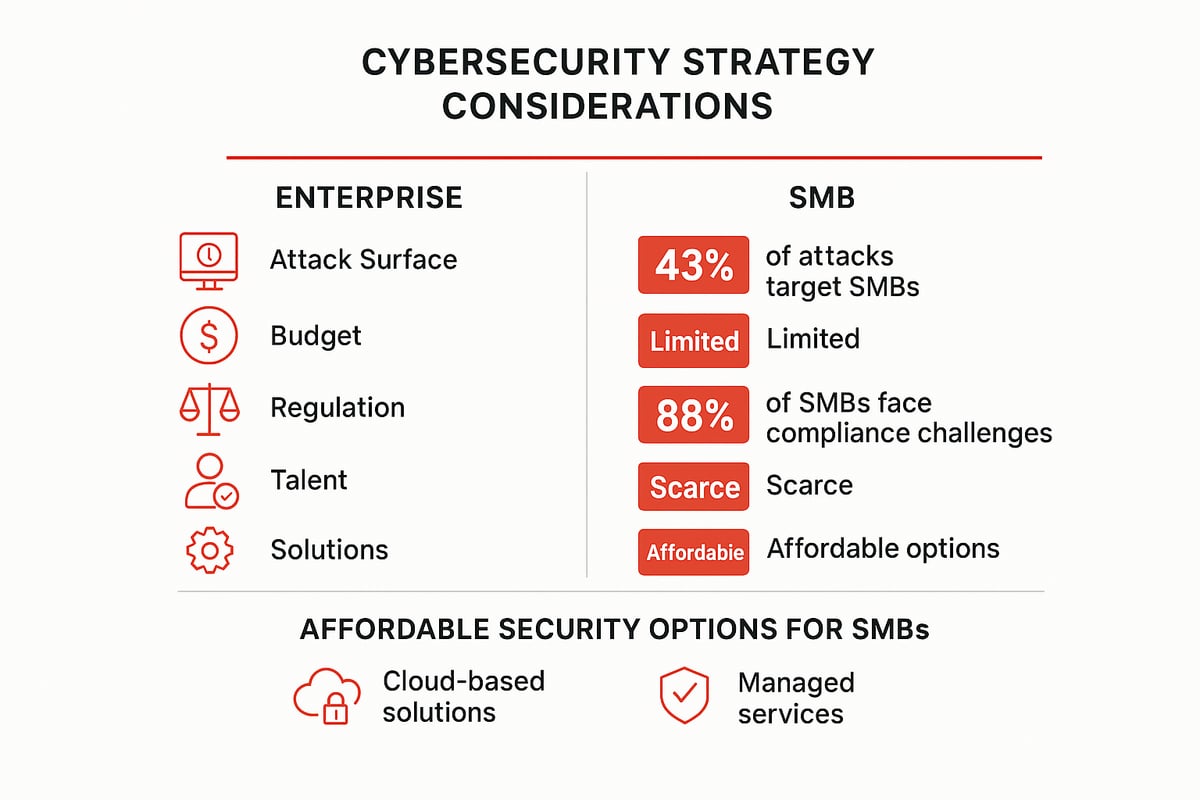
Tailoring Strategy to Organization Size and Complexity
The foundation of a strong cybersecurity strategy is understanding your organization’s unique landscape. Enterprises manage sprawling networks, multiple business units, and face strict regulatory oversight. Their attack surface is wide, requiring advanced solutions and dedicated security teams. In contrast, SMBs may have simpler infrastructures, but they are far from immune—43% of attacks now target small businesses.
Let’s visualize some key differences:
| Factor | Enterprises | SMBs |
|---|---|---|
| Attack Surface | Large, complex, distributed | Smaller, but expanding (cloud, remote) |
| Budget | Significant, for advanced tools | Limited, must prioritize |
| Regulations | Stringent, multiple frameworks | Often fewer, but still critical |
| Security Team | Dedicated, specialized roles | Small IT or outsourced |
| Solutions | Custom, layered, in-house or MSSP | Affordable, managed, cloud-based |
No matter the size, every organization needs a cybersecurity strategy that addresses third-party and supply chain risks. For example, SMBs handling HIPAA data must meet the same standards as large healthcare organizations, even when resources are tight. Retail and healthcare sectors each face unique challenges, with regulatory fines and customer trust on the line.
Affordable options exist for SMBs, such as Microsoft Defender for Business or managed security services. Many vendors now offer enterprise-grade features at a scale and price point that fit smaller organizations. Strong policy frameworks are essential for both groups; you can explore information security policies best practices to guide policy development and governance, a key part of any cybersecurity strategy.
Overcoming Resource and Talent Constraints
Resource and talent shortages can make or break a cybersecurity strategy. SMBs often lack full-time security staff, so outsourcing to managed providers or leveraging vendor-managed solutions is a smart way to cover critical controls. Prioritizing essentials—like endpoint protection, regular patching, and user training—can make a big difference.
Enterprises, with larger teams and budgets, still struggle to attract and retain skilled cybersecurity professionals. Ongoing training, leadership development, and a positive security culture are vital for keeping teams motivated and effective. Investing in security awareness across the workforce is a universal need, regardless of size.
Both enterprises and SMBs benefit from building a culture where everyone feels responsible for security. Engaging leadership, providing clear communication, and celebrating security wins helps organizations stay resilient. As more security vendors tailor solutions for smaller teams, even SMBs can access the tools needed to support a robust cybersecurity strategy.
Future-Proofing Your Cybersecurity Strategy
Staying ahead in cybersecurity strategy means more than just reacting to new threats. It’s about building resilience, preparing for what’s next, and empowering every team member. As we look to the future, let’s explore how to adapt, comply, and keep improving together.
Adapting to Emerging Technologies and Threats
The cybersecurity strategy of tomorrow must be agile and ready for anything. We’re seeing a surge in AI-driven attacks, along with smarter AI-powered defenses. Quantum computing is on the horizon, making today’s encryption vulnerable, so organizations are beginning to adopt quantum-safe cryptography.
Cloud environments and distributed data are now the norm. This means our cybersecurity strategy must extend beyond the traditional perimeter, securing IoT devices, operational technology, and remote workforces. Integrating Zero Trust and SASE architectures helps us verify every user and device, no matter where they are.
Want a deeper dive into cloud protections? Check out these Cloud security strategy essentials for practical frameworks and actionable tips. By embracing new technology and staying flexible, we turn innovation into a security advantage.
Navigating Regulatory and Compliance Changes
Regulations shift fast, and a proactive cybersecurity strategy helps us stay compliant without slowing down. New rules like the NIS2 Directive, ongoing GDPR updates, and industry-specific mandates are raising the bar for everyone.
To future-proof your approach, build flexibility into your policies. This way, when new regulations arrive, you can adapt quickly and avoid costly disruptions. Fines and penalties for non-compliance are climbing, but organizations that treat compliance as a core part of their cybersecurity strategy gain a competitive edge.
Use compliance as an opportunity to strengthen your brand. Customers and partners value organizations that take privacy and security seriously. Make compliance part of your story and set yourself apart.
Fostering a Culture of Continuous Improvement
A resilient cybersecurity strategy is not just about technology—it’s about people. Continuous improvement starts with regular training, awareness campaigns, and sharing lessons learned from incidents and near-misses.
Encourage cross-functional collaboration between IT, leadership, and staff. Invest in leadership development and community engagement to build a strong, supportive security culture. When everyone understands the role they play in cybersecurity strategy, your organization becomes more adaptable and recovers faster from setbacks.
Keep your team curious, open to feedback, and ready to grow. This mindset transforms challenges into opportunities for lasting resilience.
We’ve covered a lot together—from understanding the latest threats in 2026 to building a security program that truly fits your business. But you don’t have to navigate this journey alone. If you’re ready to turn insight into real action, let’s keep the momentum going.
Join a community where you can swap stories, get advice, and tap into practical resources designed for busy security leaders and business owners like us. We’re all about clarity, not jargon, and helping each other build resilience that lasts.
Ready to take your next step? Join CISO Launchpad