Imagine a world where billions of smart devices, vehicles, and factories are all connected through lightning-fast 5G networks. This future is arriving quickly, bringing incredible opportunities for innovation, but also introducing new risks that cannot be ignored.
By 2026, 5g network security will be the foundation for safe, reliable global connectivity. For IT leaders, security professionals, and business decision-makers, building strong defenses is no longer a luxury but a necessity.
In this guide, we will uncover the top threats facing 5G, explain the latest compliance rules, and share architecture best practices. You will also find step-by-step strategies to help you confidently protect your 5G environment.
Let’s explore how to stay ahead of evolving risks, secure your organization, and build a future where 5G drives progress without compromise.
Understanding the 5G Security Landscape in 2026
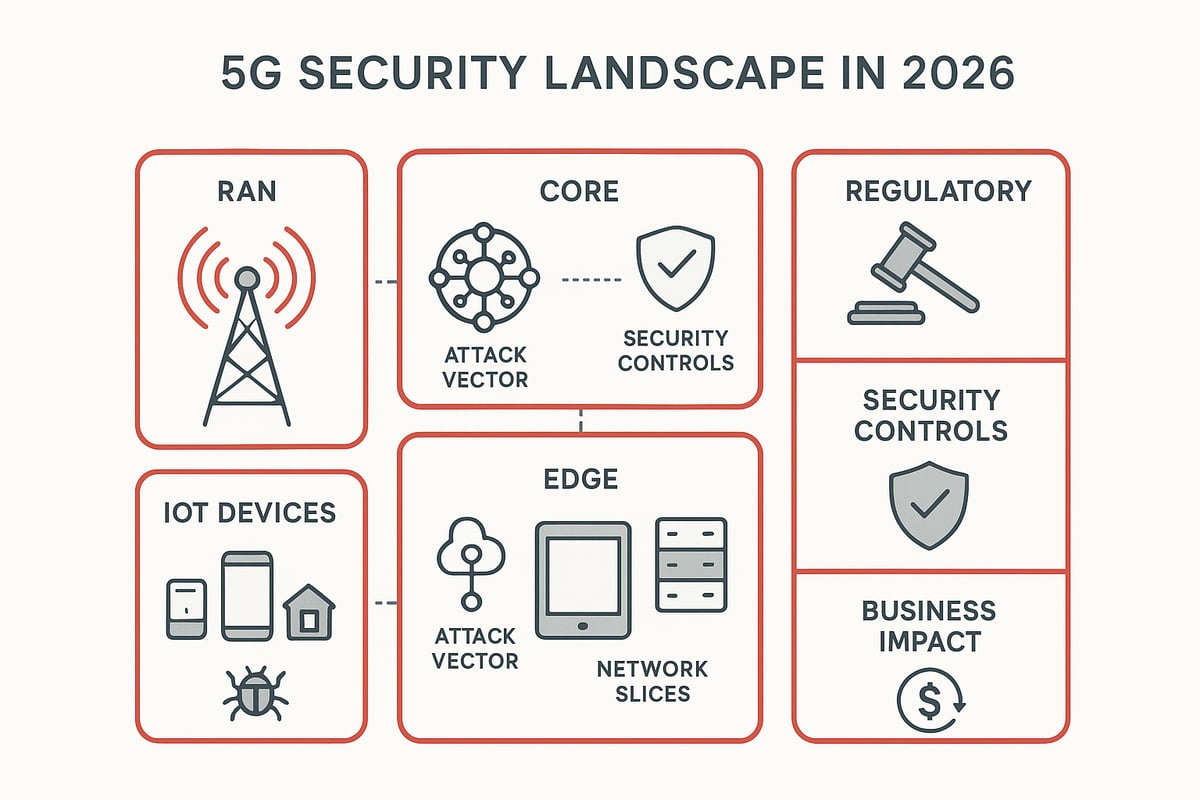
The world is experiencing a seismic shift as 5g network security becomes a top priority for organizations everywhere. With billions of devices and critical services relying on 5G, understanding the evolving security landscape is essential for IT leaders and business decision-makers. Let’s explore what makes 5G security so different and so urgent.
The Evolution of 5G and Its Impact on Security
5g network security is evolving rapidly as 5G adoption accelerates worldwide. By 2026, industry reports predict billions of connected devices, from autonomous cars to industrial sensors, all relying on ultra-fast, low-latency communication.
Unlike 4G, 5G networks use virtualization, network slicing, and edge computing, making the architecture more flexible but also more complex. This flexibility introduces new attack surfaces and challenges. For example, according to Ericsson, enterprise 5G adoption is growing, but so are the threats targeting these advanced networks. Critical infrastructure, IoT, and autonomous systems now depend on robust 5g network security controls.
Major 5G Security Threats and Attack Vectors
5g network security faces a wide array of threats. Attackers target the radio access network (RAN), the core, edge nodes, APIs, and especially IoT endpoints. The rise of sophisticated DDoS attacks, man-in-the-middle exploits, and supply chain intrusions has made the threat landscape more complex.
Nation-state actors and cybercriminal groups are increasingly focusing on 5G networks. Palo Alto Networks reports a surge in 5G-specific attacks, with real-world breaches causing significant disruption. For a deeper dive into risk mitigation, see GSMA’s Insights on Managing 5G Security Risks, which highlights strategies for defending against these evolving threats.
Regulatory and Compliance Requirements for 5G
Regulations are shaping 5g network security in unprecedented ways. Global and regional bodies like NIST, ENISA, and GSMA have introduced new frameworks to address the complexity of 5G. Telecoms and enterprises must comply with mandates that govern data privacy, integrity, and network resilience.
For example, GDPR introduces strict requirements for data flows in 5G environments, making compliance a top priority. As standards evolve, organizations must stay agile, ensuring their 5g network security strategies align with both current and upcoming regulations.
Security Challenges Unique to 5G
With 5g network security, unique technical challenges emerge. Network slicing, which allows multiple virtual networks on shared infrastructure, brings risks of slice isolation failure and cross-slice attacks. Securing cloud-native, software-defined networks adds another layer of complexity.
Zero Trust models and dynamic identity management are vital in 5G, where devices and users constantly join and leave the network. Ericsson highlights the risks in network slice management, emphasizing the importance of advanced controls for 5g network security.
The Business Case for 5G Security Investment
Investing in 5g network security is not just a technical decision, it is a business imperative. The cost of breaches includes data loss, downtime, and damaged reputation. Industry case studies show that proactive security investments deliver strong ROI and help organizations avoid costly incidents.
Deploying secure-by-design 5G architectures builds customer trust and strengthens regulatory standing. Organizations that prioritize 5g network security gain a strategic edge in the market, ensuring resilience and long-term success.
Building a Secure 5G Architecture: Foundational Principles
Building a secure 5g network security foundation is more important than ever as we enter 2026. With new technologies and greater complexity, organizations must rethink how they approach protection at every layer. Let’s explore the essential building blocks for a resilient 5g network security architecture.
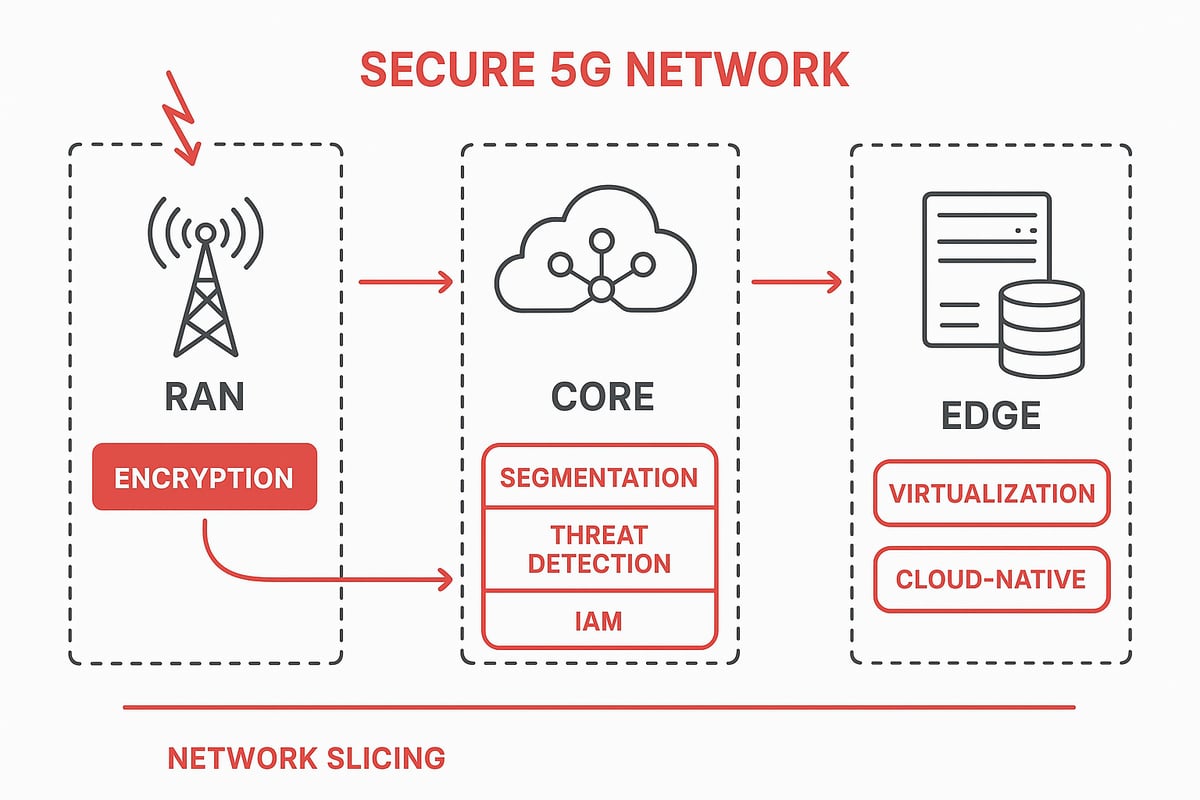
Core Components of 5G Security Architecture
The backbone of 5g network security lies in its architecture. Security must be embedded in the Radio Access Network (RAN), Core, and Edge. Each segment demands specialized controls, including encryption, segmentation, and continuous monitoring. Virtualization and containerization, essential to 5G, create both new opportunities and risks.
For example, adopting a security-by-design approach, as recommended by NIST 5G Network Security Design Principles, ensures that protection is not an afterthought. Integrating AI and machine learning can further enhance threat detection and rapid response.
Zero Trust in 5G Networks
A Zero Trust model is critical for modern 5g network security. The guiding principle is simple: never trust, always verify. Every user, device, and service must prove its identity before gaining access to any resource.
Key practices include robust identity and access management, micro-segmentation, and continuous authentication. Telecom operators have shown that implementing Zero Trust policies reduces attack surfaces and limits lateral movement within the network. Embracing this mindset fosters a proactive, not reactive, security posture for 5g network security.
Secure Network Slicing and Isolation
Network slicing is a game-changer for 5g network security but brings unique risks. Multi-tenancy and shared resources can create vulnerabilities if not properly isolated. Each slice must be authenticated, authorized, and monitored to prevent cross-slice attacks.
Best practices involve automated policy enforcement and real-time visibility into slice activity. Real-world incidents have shown that failure in isolation can lead to severe breaches. By prioritizing slice security, organizations can confidently deploy innovative services without compromising the integrity of their 5g network security environment.
Cloud-Native and Edge Security Considerations
5g network security extends to the cloud and the edge, where new threats emerge. Securing containers, orchestration platforms, and APIs is essential. Edge devices, often in remote or exposed locations, are vulnerable to physical tampering and data interception.
Data privacy and sovereignty are growing concerns, especially with distributed architectures. Industry experts recommend adopting cloud-native security tools and practices, such as regular vulnerability scanning and automated patching. Taking these steps ensures that your 5g network security is robust from the core to the farthest edge.
End-to-End Encryption and Data Protection Strategies
Protecting data as it moves through the 5g network security ecosystem is non-negotiable. Strong encryption protocols must secure both signaling and user data, whether in transit or at rest. Distributed environments demand careful key management and compliance with global data protection regulations.
By implementing comprehensive encryption and data protection policies, organizations can reduce the risk of data breaches and regulatory penalties. Staying ahead of evolving threats means making security a core part of every data flow within your 5g network security strategy.
Step-by-Step Strategies for 5G Network Security in 2026
Securing 5g network security in 2026 requires a proactive, layered approach. Let’s walk through a seven-step strategy designed for today’s threats and tomorrow’s challenges. Each step builds your resilience, boosts regulatory compliance, and protects your organization’s most valuable assets.
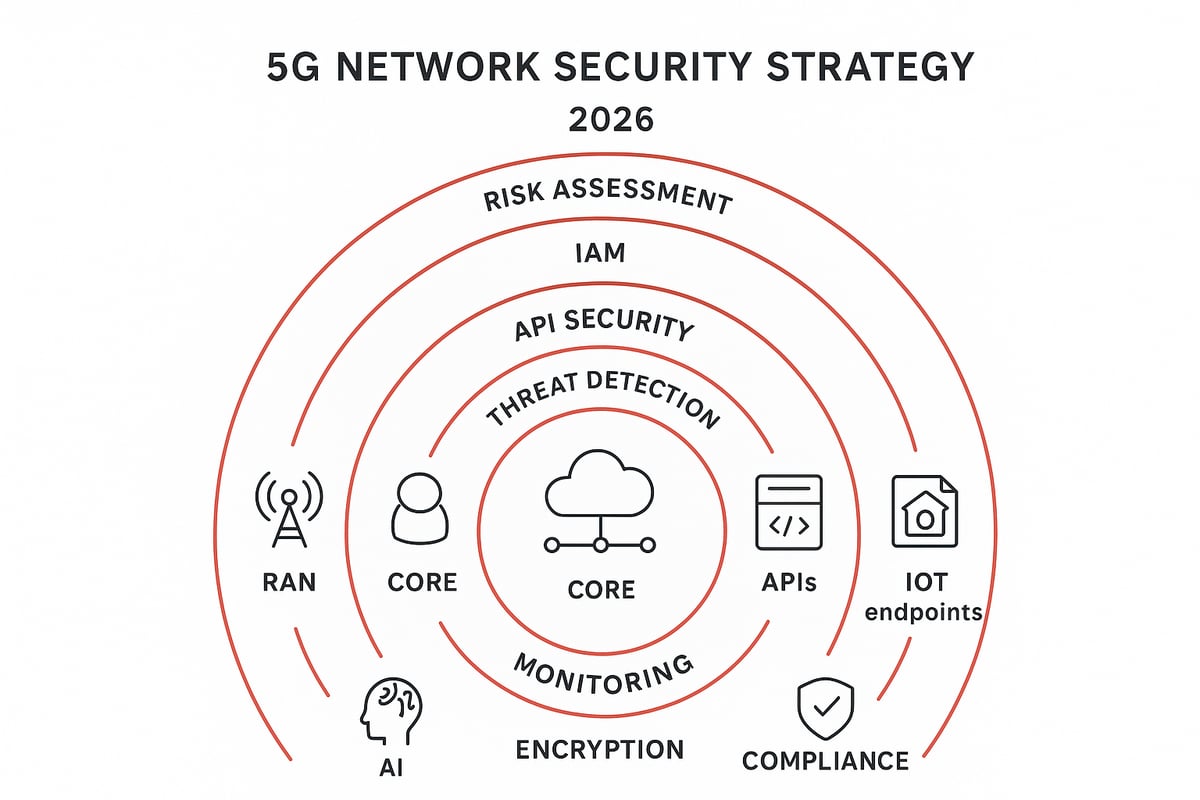
Step 1: Conduct a Comprehensive 5G Risk Assessment
Every strong 5g network security program begins with understanding your unique risk landscape. Start by mapping all assets, data flows, and dependencies across your 5G environment. Identify which systems are critical to business operations.
Threat modeling helps uncover vulnerable points, especially as networks become more complex. Use proven frameworks and templates, like those covered in Risk Assessment in Cybersecurity, to make this process efficient and thorough.
Prioritize risks based on potential business impact, not just likelihood. This ensures security resources focus where they matter most for 5g network security.
Step 2: Implement Robust Identity and Access Management (IAM)
Effective identity and access management is a cornerstone of 5g network security. With the explosion of users, devices, and applications, controlling who gets access to what is more important than ever.
Deploy multi-factor authentication to verify identities. Apply role-based and attribute-based controls to limit privileges. Continuous verification helps prevent lateral movement if credentials are compromised.
Remember, overlooked IAM gaps have led to real 5g network security breaches. Make sure your IAM policies are up to date, and regularly review user and device access.
Step 3: Secure APIs and Application Interfaces
APIs are the lifeblood of 5g network security, yet they can also be a weak link. Attackers target APIs for data leakage, injection, and abuse.
Protect APIs by enforcing strict authentication and input validation. Use rate limiting to prevent automated attacks. Automated API discovery and monitoring tools help you stay ahead of evolving threats.
Review lessons from real-world API incidents to strengthen your defenses. With strong API security, you close a major gap in 5g network security.
Step 4: Deploy Advanced Threat Detection and Response
Modern 5g network security relies on rapid detection and response. AI and machine learning can spot anomalies in huge volumes of 5G traffic, flagging suspicious behavior in real time.
Integrate your detection tools with SIEM and SOAR platforms for a unified view. Automated playbooks enable swift containment actions, reducing incident impact.
Leverage threat intelligence feeds to stay updated on the latest 5G-specific attack trends. This proactive approach keeps your 5g network security posture strong and adaptive.
Step 5: Ensure Supply Chain and Vendor Security
The supply chain is a growing attack vector for 5g network security. Third-party hardware, software, and firmware can introduce hidden risks.
Vet all vendors with rigorous due diligence. Monitor suppliers continuously for changes in risk profile. Enforce secure development and update practices, especially for critical 5G components.
Stay compliant with regulations that demand supply chain transparency. Strong supply chain security underpins a resilient 5g network security framework.
Step 6: Ongoing Security Monitoring and Incident Response
Continuous monitoring is non-negotiable for 5g network security. Deploy 24/7 monitoring across all network segments and endpoints to catch threats early.
Automated alerting and forensic analysis help you respond fast to incidents. Build and regularly test incident response playbooks so your team is ready for anything.
Learning from real-world telecom operator incidents can inspire improvements. Consistent monitoring and practiced response are key to 5g network security.
Step 7: Regular Security Testing and Continuous Improvement
Never assume your 5g network security is perfect. Regularly schedule penetration testing, red teaming, and vulnerability assessments.
Continuous compliance checks keep you audit-ready. Track security maturity with clear metrics, and use lessons from assessments to guide improvements.
Iterate and refine your security strategy to stay ahead of emerging threats. This commitment to ongoing testing and learning is essential for 5g network security success.
Human Factors and Governance in 5G Security
Securing a 5g network security environment is not just about technology, it is about people, processes, and leadership working together. Without a strong focus on human factors and governance, even the best technical controls can fall short. Let us explore how a security-first mindset, robust governance, ecosystem vigilance, and empowered leadership come together to build resilient 5g network security.
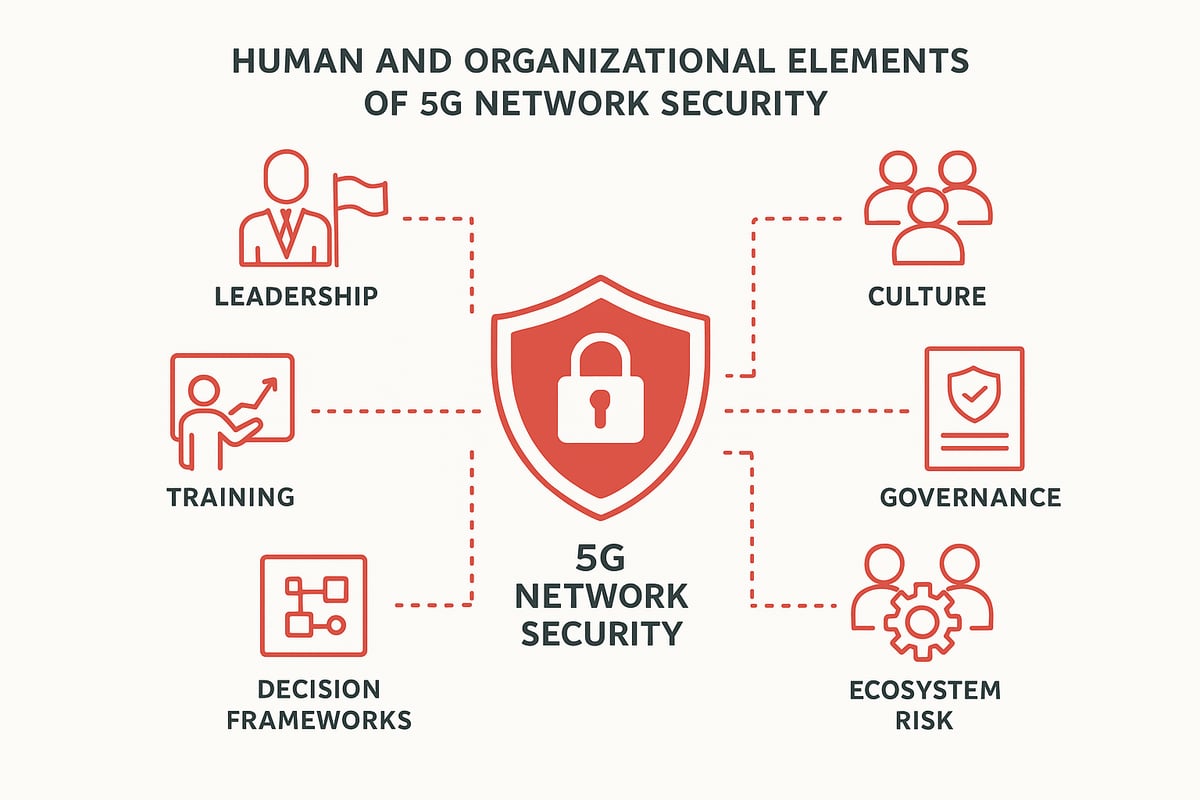
Building a Security-First Culture for 5G
Creating a security-first culture is foundational for effective 5g network security. Leadership must set the tone by making security a core value, not just a checklist. This means leaders promote open communication about risks and encourage everyone to take responsibility for security.
Security awareness training tailored to 5g network security threats helps staff recognize and respond to emerging risks. Cross-functional collaboration between IT, operations, and business units ensures that security is woven into daily decisions. Appointing security champions in different teams fosters grassroots advocacy and drives positive change. Organizations that prioritize change management during 5g rollouts see fewer missteps and faster adoption of secure practices.
Governance, Risk, and Compliance (GRC) for 5G
A robust governance framework guides every aspect of 5g network security, from policy development to compliance checks. Integrating 5g security into enterprise GRC practices means setting clear rules for network use, access control, and data handling. Regular policy reviews keep these guidelines current as threats evolve.
Aligning with regulatory and industry standards, such as GSMA NESAS, is vital for both compliance and customer trust. For deeper insights on establishing effective frameworks, see Cybersecurity Governance. Frequent governance reviews ensure that security policies remain relevant and enforceable, providing a solid foundation for ongoing 5g network security.
Third-Party and Ecosystem Risk Management
In a 5g network security context, your ecosystem is only as strong as its weakest link. Managing risks from partners, vendors, and service providers is essential. Clear contractual security requirements, like service-level agreements (SLAs), help set expectations and standards for all parties involved.
Continuous monitoring of third-party risks and regular risk scoring can uncover vulnerabilities before they become incidents. When organizations have experienced supply chain breaches impacting 5g network security, the cause is often a lack of ecosystem visibility. Proactive management helps ensure that partners uphold the same high standards as your own team.
Security Leadership and Decision-Making in 5G Era
Strong leadership is the backbone of any successful 5g network security strategy. CISOs and security leaders must bridge the gap between technical needs and business priorities, ensuring resources are allocated wisely. Decision frameworks help leaders evaluate risks, set priorities, and make informed trade-offs.
Engaging stakeholders from across the organization fosters a unified approach to 5g network security. Industry leaders emphasize the value of clear communication, regular updates, and empowering teams to act quickly. By placing security at the heart of every decision, organizations build resilience and agility for the future.
Future Trends and Emerging Technologies in 5G Security
The world of 5g network security is evolving at an astonishing pace. As we look toward 2026, emerging technologies are shaping both new risks and powerful defenses. Let’s explore the most significant trends on the horizon and how they will impact us all.
AI and Automation in 5G Security Operations
Artificial intelligence is revolutionizing 5g network security. AI-powered systems can analyze enormous volumes of network data, spotting suspicious patterns that humans might miss. These tools help us respond to threats in real time, reducing the window of vulnerability.
Automated policy enforcement lets us adapt defenses instantly as new risks appear. Yet, as we rely more on AI, we also face new challenges such as adversarial attacks and the risk of false positives. Upskilling teams is essential to keep pace with these changes.
For a deeper dive into the practical strategies needed to secure AI-driven 5g network security, check out CISA’s 5G Security and Resilience Overview. This resource covers risk management approaches tailored to modern networks.
Quantum Computing and Its Impact on 5G Security
Quantum computing is rapidly approaching, and its impact on 5g network security cannot be ignored. Quantum machines have the potential to break many of today’s encryption protocols, putting sensitive data at risk.
To prepare, organizations are beginning to explore post-quantum cryptography—algorithms designed to resist quantum attacks. Industry groups are setting roadmaps for migration, but timelines remain uncertain. For now, the best defense is to stay informed and start planning for quantum-safe upgrades.
The transition to quantum-resistant methods is a journey, not a sprint. By acting early, we can ensure our 5g network security stays strong in the face of future breakthroughs.
Securing the 5G-Enabled Internet of Things (IoT)
IoT devices are proliferating across industries, all connected through 5g network security frameworks. With billions of endpoints, the risk surface is massive. Each device, from sensors to smart cameras, represents a potential entry point for attackers.
Securing these devices means focusing on robust authentication, secure onboarding, and continuous monitoring. Cloud infrastructure, which supports much of this IoT traffic, introduces additional risks. For more on these, see Cybersecurity Threats in the Cloud, which explores vulnerabilities relevant to IoT environments.
By prioritizing IoT security, we can protect data, ensure reliability, and keep the promise of smart, connected environments.
Preparing for 6G and the Next Wave of Network Security
The shift to 6G is already underway, and the lessons we learn from 5g network security will guide us. As networks become even faster and more complex, new attack surfaces and threats will emerge.
Forward-thinking organizations are using today’s challenges to build adaptable, resilient security strategies. This means investing in flexible architectures and continuous learning. As we look ahead, keeping a close eye on evolving standards and cross-industry collaboration will be key.
By applying what we know now, we can shape a future where 5g network security and beyond keeps our data, businesses, and communities safe.
Case Studies: 5G Security in Action
Real-world stories bring 5g network security to life, showing us what works and what pitfalls to avoid. Let’s explore how organizations in telecom, manufacturing, and the public sector have tackled their toughest 5G security challenges.
Telecom Operator: Preventing a Multi-Vector 5G Attack
A leading telecom operator faced a coordinated assault on its 5G network. Attackers combined a massive DDoS flood with targeted API abuse, putting critical mobile services at risk. The operator’s team immediately segmented its network, isolating affected regions to contain the threat. They also deployed advanced DDoS mitigation and robust API gateways.
By monitoring for API security vulnerabilities, the team detected and blocked malicious traffic before it could escalate. This layered approach to 5g network security allowed fast detection and response, resulting in minimal downtime and full compliance with regulations.
Lessons learned included the importance of continuous API monitoring and automated threat response. Other operators can benefit by prioritizing segmentation and tackling API risks head-on.
Manufacturing: Securing 5G-Connected IoT Devices
A smart factory harnessed the power of 5G to connect thousands of sensors, robots, and cameras. However, this connectivity introduced new attack vectors. The factory’s security team identified risks such as device hijacking, data exfiltration, and lateral movement between machines.
To address these, they implemented device attestation, ensuring only trusted hardware could join the network. Segmentation isolated critical systems, preventing a single breach from spreading. Continuous monitoring flagged suspicious behavior, allowing rapid intervention.
Their investment in 5g network security paid off. The company saw fewer incidents, improved uptime, and stronger customer trust. The takeaway: securing every device and enforcing strict network boundaries are essential in modern manufacturing.
Public Sector: 5G Network Slicing for Emergency Services
Emergency services rely on dedicated 5G network slices for secure, reliable communication. In one city, public safety officials faced threats from unauthorized access and misconfigured slices, putting sensitive data and response times at risk.
The team adopted strong authentication and real-time monitoring to protect these slices. They also reviewed research on rogue gNodeB’s impact on 5G network slicing, learning how attackers could manipulate slice allocations. By applying best practices from industry standards, they maintained data confidentiality and ensured that first responders always had priority access.
This proactive stance in 5g network security led to better outcomes for citizens and reinforced public trust in emergency services.
Lessons Learned and Best Practices
Across industries, 5g network security success comes from a blend of technology, vigilance, and collaboration. Common threads include network segmentation, robust authentication, and a readiness to learn from new threats. Organizations adopting 5G should prioritize end-to-end security, invest in continuous monitoring, and foster a culture where security is everyone’s responsibility.
We’ve just explored the core threats, practical strategies, and real-world lessons that matter most for securing your 5G environment in 2026. If you’re ready to keep this momentum going and connect with others who share your drive for clarity and actionable cybersecurity leadership, I’d love for you to join us.
The Join Cyber Launchpad Community is a welcoming space where IT leaders, security pros, and decision-makers share stories, frameworks, and support, no buzzwords, just real guidance.
Let’s keep learning, growing, and helping each other build truly resilient organizations. You belong in this community.