Imagine a world where a single slip in it security management can cost millions, disrupt critical operations, and shatter trust overnight. In 2026, the stakes have never been higher, and the threats are evolving at breakneck speed.
This essential guide is here to help you master it security management. We’ll walk through the latest cyber threats, foundational security principles, innovative technologies, compliance hurdles, and proven frameworks. You’ll gain up-to-date, practical strategies to stay ahead.
Ready to build resilience and lead with confidence? Let’s dive into the future of it security management together.
The Evolving IT Security Threat Landscape in 2026
The world of it security management in 2026 is more unpredictable than ever. Cyber threats have grown in complexity and scale, with attackers using advanced tactics to outmaneuver traditional defenses. As we look ahead, the stakes for businesses, governments, and individuals continue to climb.
A Surge in Sophisticated Cyberattacks
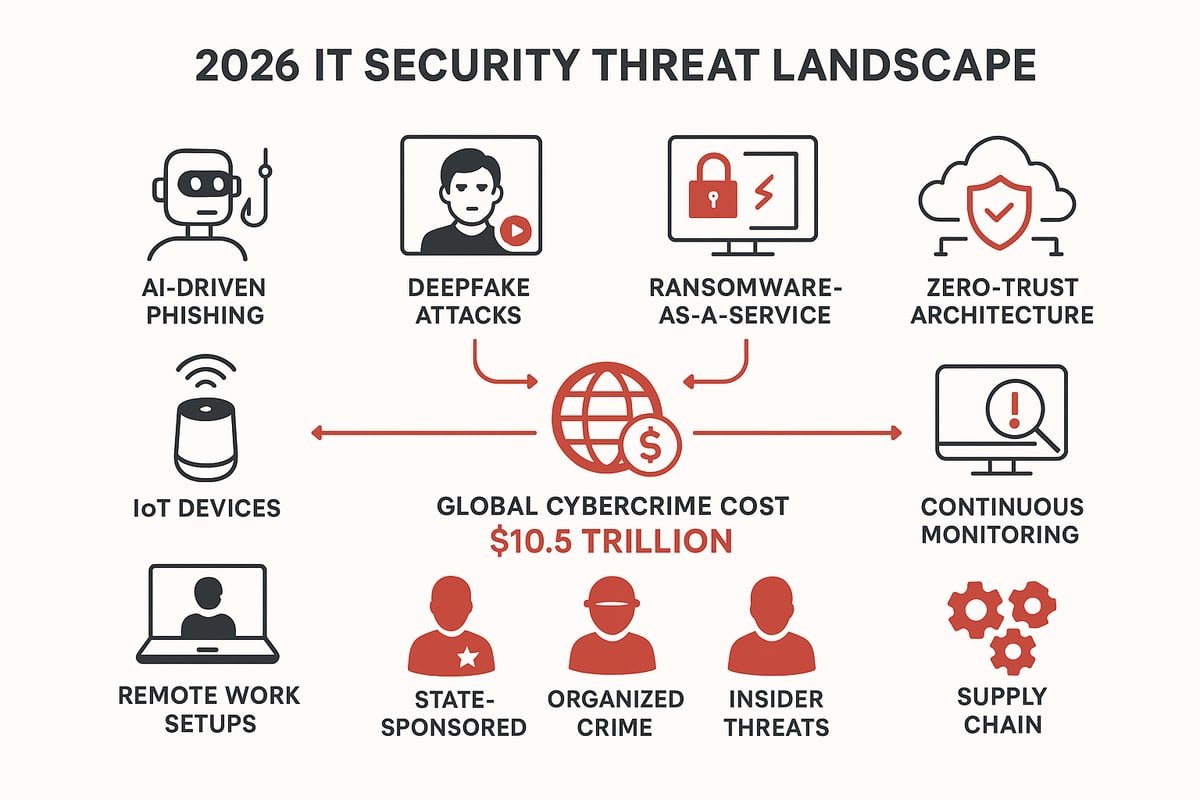
Attackers in 2026 aren’t just using old tricks. They’re deploying AI-driven phishing campaigns that craft messages indistinguishable from real colleagues. Deepfake technology enables cybercriminals to impersonate executives in video calls, tricking employees into transferring funds or sharing sensitive data. Meanwhile, ransomware-as-a-service platforms have lowered the barrier to entry, letting even less-skilled actors launch devastating attacks.
The evolution of these threats means it security management must adapt quickly. Modern defenses now rely on predictive analytics and automation to spot and contain threats before they spread. According to industry forecasts, global cybercrime costs are projected to hit $10.5 trillion annually by 2026, underscoring the urgent need for robust protection.
Expanding Attack Surfaces: IoT, Remote Work, and Supply Chains
The rapid adoption of IoT devices, increased remote work, and the migration to cloud services have expanded the digital attack surface. Each new device and connection represents a potential entry point for attackers. Supply chain vulnerabilities have also risen, as organizations depend on third-party vendors for critical operations.
It security management now demands a holistic approach, accounting for these interconnected risks. Regular assessments and continuous monitoring are crucial to identify weak spots before they can be exploited.
High-Profile Breaches and the Ripple Effect
Recent years have seen headline-grabbing breaches in banking and healthcare, where a single vulnerability led to massive data leaks, service disruptions, and loss of customer trust. The impact isn’t limited to large enterprises. Small and medium businesses are increasingly targeted, often because attackers know they may lack the resources for mature it security management.
The consequences extend beyond financial loss. Reputational harm and regulatory penalties can threaten an organization’s survival. Leaders must remember that no company is too small to be targeted.
Emerging Threat Actors: Who’s Behind the Attacks?
Threat actors have grown more organized and resourceful. State-sponsored groups, often backed by significant funding and expertise, target critical infrastructure and intellectual property. Organized cybercrime rings run large-scale operations for profit, while insider threats remain a persistent risk.
Staying ahead requires it security management teams to gather threat intelligence, understand attacker motives, and prepare for tactics that change almost daily. Proactive defense strategies, rather than reactive ones, are now essential for resilience.
Zero-Trust, Continuous Monitoring, and the Shift to Proactive Defense
Traditional perimeter defenses are no longer enough. Modern it security management emphasizes zero-trust principles, treating every user and device as untrusted until proven otherwise. Continuous monitoring across networks and endpoints helps detect suspicious activity in real time.
To explore the latest trends in AI-driven threat detection and zero-trust architectures, see Cybersecurity trends in 2026: AI defense to digital trust.
Ultimately, the organizations that thrive in this new landscape are those that shift from a reactive stance to a proactive, resilient approach. By embracing continuous improvement and learning from past incidents, we can build a stronger, more secure future together.
Core Principles and Pillars of IT Security Management
In today’s digital landscape, IT security management is the backbone of every resilient organization. The core principles form a safety net, ensuring that sensitive data remains protected, operations run smoothly, and trust is never compromised.
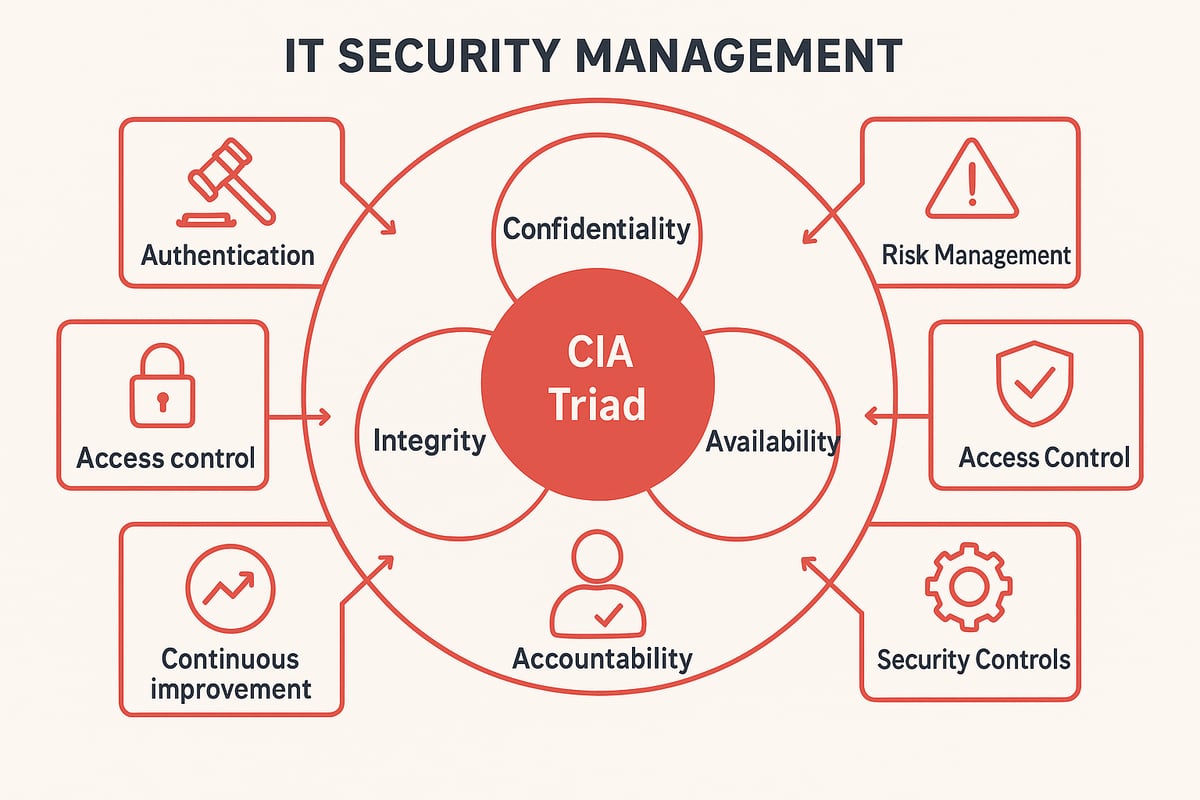
The CIA Triad: Foundation of IT Security Management
At the heart of it security management lies the CIA Triad: Confidentiality, Integrity, and Availability. Confidentiality keeps unauthorized eyes away from sensitive data. Integrity ensures information remains accurate and unaltered. Availability guarantees that systems and data are accessible when needed.
These three principles serve as the compass for every security decision. Whether you’re protecting patient records or financial transactions, the CIA Triad guides how we safeguard information and keep business moving forward.
Beyond the Basics: Expanding Security Principles
Modern it security management goes beyond the CIA Triad. Authentication verifies the identity of users and systems, building trust into every interaction. Accountability ensures that every action is traceable to an individual or system, which helps in audits and investigations. Non-repudiation means no one can deny their actions, providing assurance in legal or compliance scenarios.
By weaving these principles into daily practices, organizations build layers of protection that adapt to evolving threats. Each principle acts like a puzzle piece, fitting together to create a stronger, more resilient defense.
The Six Pillars of IT Security Management
Effective it security management stands on six essential pillars:
- Governance sets the tone, defining policies, roles, and expectations. For a deep dive, check out Cybersecurity Governance Essentials.
- Risk Management helps identify, assess, and prioritize threats before they cause harm.
- Compliance ensures organizations meet industry standards and legal obligations.
- Access Control restricts who can view or change critical data, minimizing insider risk.
- Security Controls include technical, procedural, and physical safeguards that detect, prevent, and respond to threats.
- Continuous Improvement means regularly reviewing and strengthening defenses as new risks emerge.
In healthcare, for example, these pillars work together. Layered security models protect patient data at every stage, from encryption in databases to strict access controls for staff. This holistic approach reduces vulnerabilities and supports uninterrupted care.
Aligning Security with Business Goals
It security management isn’t just about technology; it’s about enabling the business. When security aligns with company objectives and risk appetite, it becomes a driver of innovation and growth. Leaders like CISOs and IT managers play a vital role in creating a security-first culture, where every team member understands their part in protecting the organization.
A strong security culture empowers people to make smart decisions, report suspicious activity, and embrace new technologies with confidence. This unity transforms security from a hurdle into a powerful business enabler.
The Regulatory Landscape: Why Compliance Matters
Today, regulatory requirements for data protection are more demanding than ever. Frameworks like GDPR, CCPA, HIPAA, and PCI DSS set high standards for privacy and accountability. As these requirements evolve, organizations must adapt their it security management strategies to stay compliant and avoid costly penalties.
Meeting these standards is not just about ticking boxes. It’s about building trust with customers, partners, and regulators. By prioritizing compliance, businesses show they value security and are committed to protecting everyone’s interests.
Strategic Frameworks and Standards for IT Security Management
In today’s fast-changing world, it security management is only as strong as the frameworks that guide it. With threats growing more advanced, organizations need clear standards to protect their operations, data, and reputation.
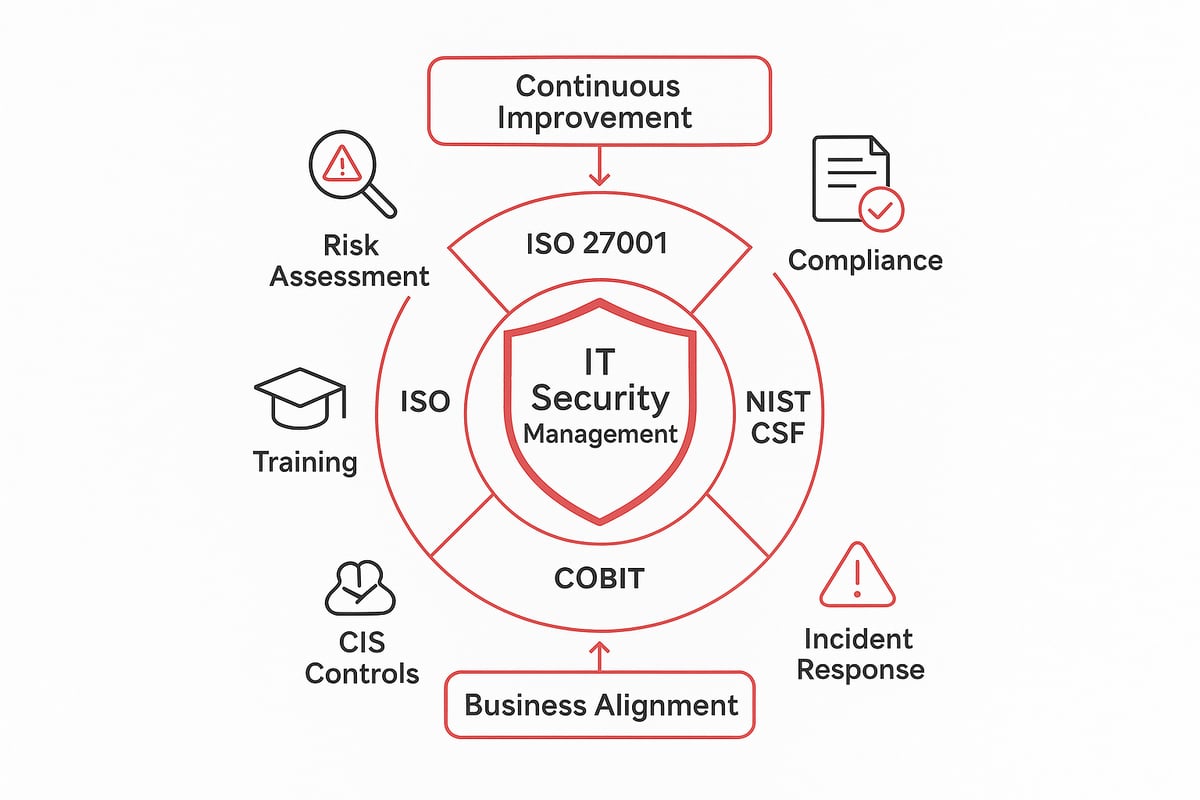
Leading Frameworks Shaping Security Management
Several leading frameworks form the backbone of modern it security management. Each offers a unique approach to safeguarding information and systems:
- ISO 27001: A global standard for establishing, implementing, and continually improving an information security management system.
- NIST Cybersecurity Framework (CSF): Widely used in the US, it provides a flexible structure for identifying, protecting, detecting, responding, and recovering from cyber threats.
- COBIT: Focuses on governance and management of enterprise IT, aligning security with business goals.
- CIS Controls: A set of prioritized actions to defend against the most common attacks.
Curious about which framework fits your needs? Explore a comprehensive comparison of these options in the Best Cybersecurity Frameworks guide.
Choosing and Customizing the Right Framework
Selecting the best framework for your organization depends on size, industry, and risk tolerance. Larger companies may lean toward ISO 27001 or COBIT for their comprehensive scope. Smaller businesses often start with CIS Controls for practical, actionable steps.
Tailoring a framework is key to making it security management a business enabler. Map framework requirements to your company’s processes, regulatory needs, and technology stack. Regularly revisit these choices as your environment evolves.
Implementing and Sustaining Security Standards
Putting a framework into action starts with a gap analysis. Identify where your current practices fall short of the chosen standard. From there, develop an action plan that covers risk assessments, policy updates, and technical controls.
Integration with business continuity and disaster recovery plans ensures resilience when incidents occur. Regular training and certification keep your it security management team sharp and informed about the latest threats and best practices.
A recent industry survey shows 65% of organizations plan to adopt new frameworks by 2026. This shift highlights the growing recognition that structured, well-maintained it security management programs are essential for long-term success.
The Impact of Emerging Technologies on IT Security Management
Emerging technologies are transforming the landscape of it security management. As new tools and innovations reshape how we protect data, IT teams must adapt quickly to stay ahead. The pace of change can feel overwhelming, but with the right mindset and tools, we can turn these challenges into opportunities.
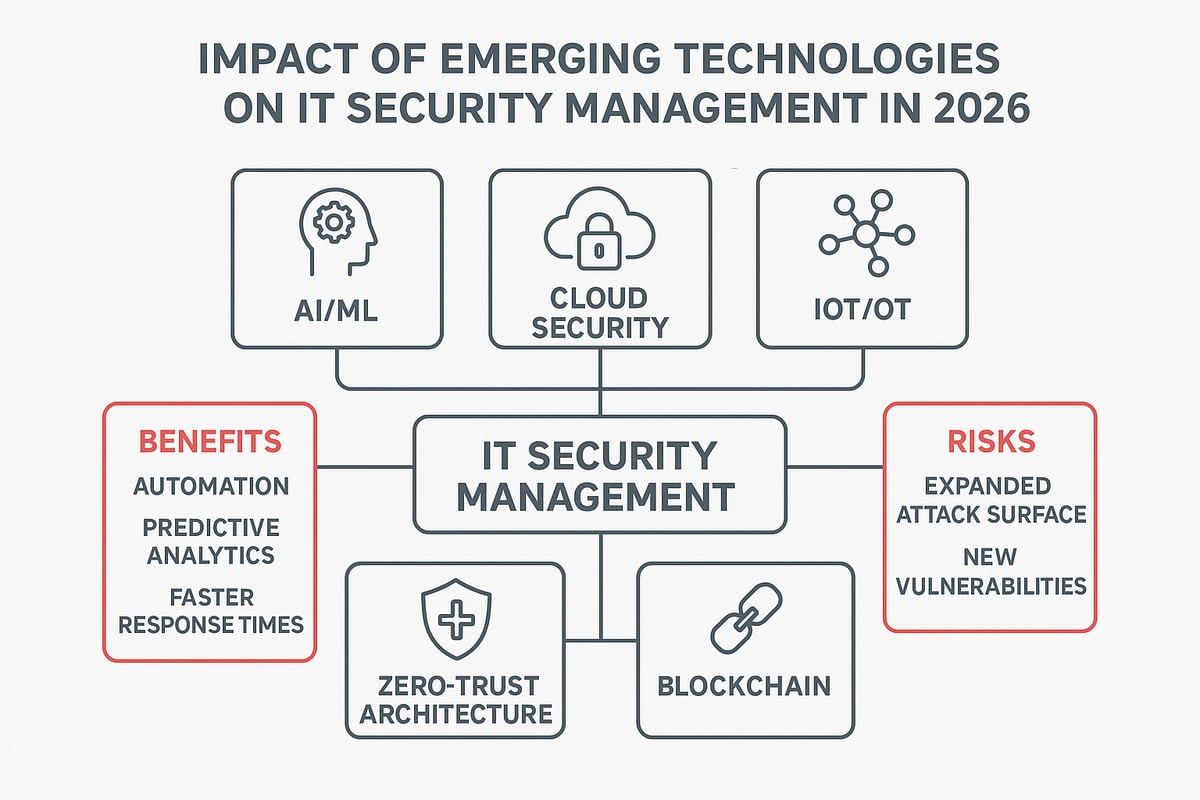
Artificial intelligence and machine learning are at the forefront of it security management. These technologies help organizations spot threats faster and automate repetitive security tasks. Predictive analytics powered by AI can identify unusual patterns, flagging possible breaches before they cause harm. Security Operations Centers now use AI-driven platforms to cut response times, letting teams focus on complex incidents that require human judgment.
Cloud computing, IoT, and operational technology are expanding the attack surface for it security management. With more devices and data in the cloud, managing access and ensuring encryption is essential. The shared responsibility model means organizations must understand their role in protecting assets. As IoT and OT devices multiply, risks grow, especially in sectors like manufacturing and energy. For more on these challenges, see OT cybersecurity 2026: six data-driven trends.
Zero-trust architecture is quickly becoming a cornerstone of it security management. This approach assumes no user or device is trusted by default, requiring continuous verification. Implementing zero-trust can be complex, with challenges around legacy systems and user experience. Meanwhile, blockchain and decentralized identity solutions are emerging to help secure transactions and protect digital identities, offering new avenues for resilience.
Technology is a double-edged sword for it security management. While AI and automation empower faster, smarter defenses, they also introduce new risks. Attackers are leveraging these same tools to craft more sophisticated threats. By 2026, 80% of enterprises are expected to use AI-powered security tools, making it vital for organizations to weigh the benefits and potential vulnerabilities of every innovation.
Step-by-Step Implementation: Building an Effective IT Security Management Program in 2026
Building a resilient IT security management program in 2026 requires a clear, methodical approach. With threats multiplying and regulations evolving, organizations need a roadmap that ensures nothing falls through the cracks. Let’s walk through the essential steps, each designed to strengthen your security posture and build confidence across your team.
Step 1: Conduct a Comprehensive Risk and Vulnerability Assessment
Every effective IT security management journey begins with a deep understanding of your current risk landscape. Use up-to-date tools and recognized frameworks to identify potential threats, vulnerabilities, and digital assets at risk. For a practical guide on assessment processes, see Risk Assessment in Cybersecurity. By mapping risks early, you ensure your program is built on solid ground.
Step 2: Develop a Comprehensive IT Security Policy
Next, craft a security policy that aligns with your business objectives and regulatory requirements. This policy should outline:
- Access controls for users and devices
- Encryption standards for sensitive data
- Backup and disaster recovery procedures
- Incident response plans
A clear, well-communicated policy sets expectations and provides a foundation for consistent decision-making.
Step 3: Establish Governance Structures and Define Roles
Strong IT security management depends on clear leadership and accountability. Assign responsibilities to key roles such as the CISO, IT managers, and security analysts. Define who makes decisions, who manages incidents, and who ensures compliance. This clarity avoids confusion during critical moments and promotes a culture of shared responsibility.
Step 4: Deploy Layered Security Controls
Implement a multi-layered approach to defenses, including:
- Physical controls (badge access, surveillance)
- Technical controls (multi-factor authentication, endpoint protection, network segmentation)
- Procedural controls (security policies, change management)
- Compliance controls (meeting regulatory standards)
Layered security makes it much harder for threats to succeed, reducing the risk of single points of failure.
Step 5: Implement Continuous Monitoring, Testing, and Improvement
Security is never static. Use tools for real-time threat detection, regular audits, and penetration testing. Continuous monitoring helps you spot and respond to incidents quickly. For example, organizations that maintain 24/7 Security Operations Center (SOC) monitoring have significantly reduced breach dwell times and improved their overall IT security management outcomes.
Step 6: Foster a Culture of Security Awareness and Accountability
People are at the heart of every IT security management program. Provide ongoing training, run simulated phishing attacks, and encourage open communication about security concerns. When everyone feels responsible, you reduce the risk of human error and build a stronger defense.
Step 7: Prepare for Incident Response and Disaster Recovery
No system is infallible. Develop playbooks for different incident scenarios, run tabletop exercises, and create comprehensive business continuity plans. Being prepared minimizes downtime and reputational damage when incidents occur.
Step 8: Stay Ahead of Regulatory Changes and Update Policies
Regulations shift quickly. Assign responsibility for tracking new laws and standards, and update your security policies as needed. Proactive adaptation reduces the risk of fines and keeps your organization trusted by clients and partners.
Organizations with formalized IT security management programs recover from incidents 50% faster, according to recent industry case studies. This step-by-step approach is not a one-time project, but a continuous, iterative process. By building each layer thoughtfully, you can adapt to new challenges and keep your business resilient—no matter what 2026 brings.
The Human Element: Leadership and Communication in IT Security Management
Effective leadership is the backbone of it security management in 2026. No matter how advanced your technology or how robust your controls, the human element will always be the greatest variable. Leaders set the tone for security culture, influence priorities, and drive lasting change across organizations.
Strong leadership in it security management means more than enforcing policies. It’s about inspiring a sense of shared responsibility. When leaders actively champion security, employees are more likely to embrace best practices and remain vigilant. This ripple effect can make the difference between a near-miss and a costly breach.
Communication is a critical skill for any security leader. Translating technical risks into business language ensures that executives understand the stakes, approve necessary investments, and support security initiatives. When teams speak a common language, decision-making becomes faster and more effective.
The gap between technical experts and business leaders often leads to misunderstandings and missed opportunities. Successful it security management bridges this gap by building cross-functional teams. Including representatives from IT, operations, HR, and legal ensures that everyone’s perspective is considered, and responses to incidents are coordinated and swift.
Unfortunately, human error remains a stubborn challenge. Industry reports show that 70% of breaches involve mistakes or social engineering. The solution is not blame but education. Regular training, realistic simulations, and open feedback channels help employees recognize threats and respond with confidence. Organizations that tie security KPIs to executive performance see stronger engagement from the top down.
Learning from past failures is just as important as celebrating successes. When security is siloed or undervalued, organizations become vulnerable. Encouraging mentorship, peer learning, and community involvement helps develop the next generation of leaders who can adapt to new challenges.
As we look ahead, future-ready leaders in it security management will need technical acumen, communication skills, and a collaborative mindset. Investing in leadership development is not optional—it’s essential for building resilient, adaptive teams. For practical guidance on building these skills, explore Security Leadership Strategies, which offers actionable insights on leading security initiatives and fostering a culture of trust.
By placing people at the core of it security management, organizations can turn their workforce into their greatest defense, not their weakest link.
As we wrap up this essential guide to IT security management in 2026, remember—you’re not alone on this journey. Navigating evolving threats, balancing strategy with real-world challenges, and leading with confidence can feel overwhelming, but together, we can make sense of it all.
If you’re looking for a supportive space to share ideas, get practical guidance, and learn from fellow security professionals, I’d love to invite you to join Cyber Launchpad Community.
Let’s keep building resilient organizations and supporting each other as the security landscape grows more complex. We’re stronger together!