An Essential Guide to Cyber Risk to Decision Engineering in 2026
In 2026, cyber risk is no longer a technical problem waiting to be fixed. It is a leadership problem waiting to be decided.
Organizations are not failing because they lack data, tools, or frameworks. They are failing because risk information rarely turns into clear, confident decisions. Reports are written, findings are documented, and dashboards are updated—yet priorities stall, funding is delayed, and accountability remains unclear.
This guide introduces Cyber Risk to Decision Engineering: a practical discipline that transforms cyber risk from technical findings into decision-ready input for executives. We will explore why traditional approaches fall short, how decision-centric thinking changes outcomes, and what it takes to engineer risk conversations that leaders can actually act on.
Join the book waitlist
I’m preparing to release Cyber Risk-to-Decision Engineering as a book. If you’d like to be notified when it’s available, you can join the waitlist here.
No launch emails.
Just a note when the book is ready.
Let’s begin where most security programs quietly break down.
Understanding Cyber Risk to Decision Engineering
Cyber Risk to Decision Engineering is the practice of deliberately designing how cyber risk information becomes an executive decision.
Understanding the implications of Cyber Risk to Decision Engineering is crucial for modern leadership.
It recognizes a hard truth of modern organizations: risk does not speak for itself. Evidence alone does not drive action. Decisions happen only when leaders clearly understand what matters now, what choices exist, and who owns the outcome.
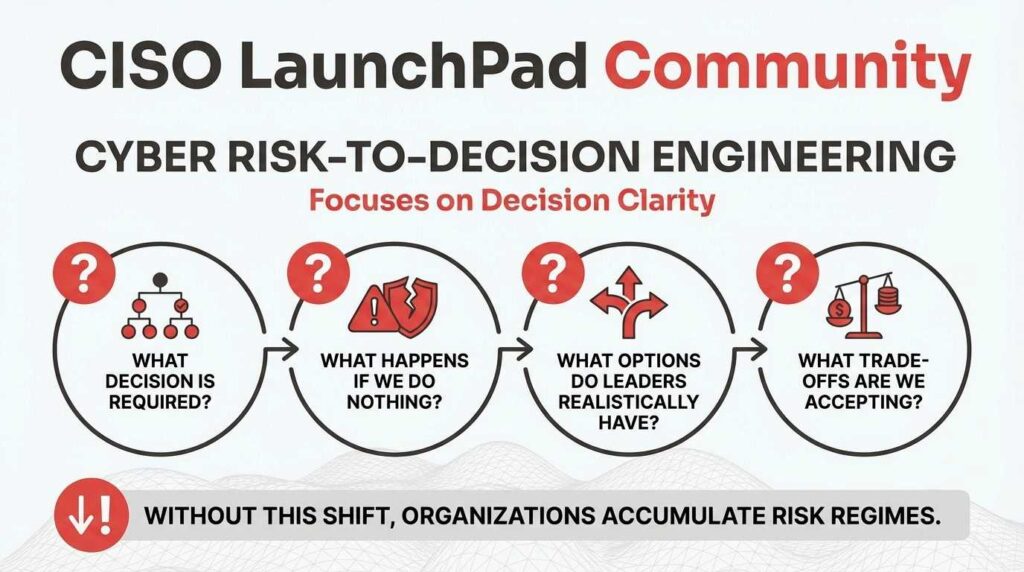
Where traditional cyber risk management focuses on identifying, scoring, and documenting risks, Cyber Risk-to-Decision Engineering focuses on decision clarity. It asks different questions:
- What decision is required?
- What happens if we do nothing?
- What options do leaders realistically have?
- What trade-offs are we accepting?
Without this shift, organizations accumulate risk registers that grow more detailed—and less useful—every year.
Why Cyber Risk Fails to Become Action
Most cyber risk programs break down at the same point: the handoff from analysis to leadership.
Technical teams deliver findings. Executives receive information. But no one engineers the decision itself.
This gap shows up in familiar symptoms:
- “Let’s revisit this next quarter.”
- “We need more data before deciding.”
- “Is this really a business risk?”
- “Who owns this?”
These are not signs of disinterest. They are signs that the risk was never framed for decision-making.
Cyber Risk to Decision Engineering exists to close this gap—by design, not by chance.
Risk Engineering vs. Risk Reporting
Traditional risk reporting emphasizes completeness. Decision engineering emphasizes relevance.
Risk reports often aim to be exhaustive, covering controls, vulnerabilities, likelihood scores, and maturity ratings. While accurate, they overwhelm decision-makers who must weigh cyber risk alongside revenue, operations, legal exposure, and strategy.
Decision-engineered risk, by contrast, is intentionally constrained. It focuses on:
- Consequences, not configurations
- Timing, not theoretical likelihood
- Options, not recommendations
- Ownership, not escalation
The goal is not to simplify risk, but to make it usable.
The Core Principles of Cyber Risk to Decision Engineering
Effective decision engineering rests on a few foundational principles.

Decisions Come First
Every risk conversation must start with a clear decision requirement. If no decision is needed, no executive attention will follow.
Options Beat Opinions
Executives do not want a single “right answer.” They want credible options, trade-offs, and implications.
Time Changes Risk
Risk is dynamic. Decision-ready risk always answers: “What happens if we wait?”
Ownership Is Engineered, Not Assumed
A risk without a clear decision owner is not a risk—it is noise.
Confidence Is Built Through Clarity
Executives act when they feel oriented, not pressured.
These principles shift cyber conversations from explanation to enablement.
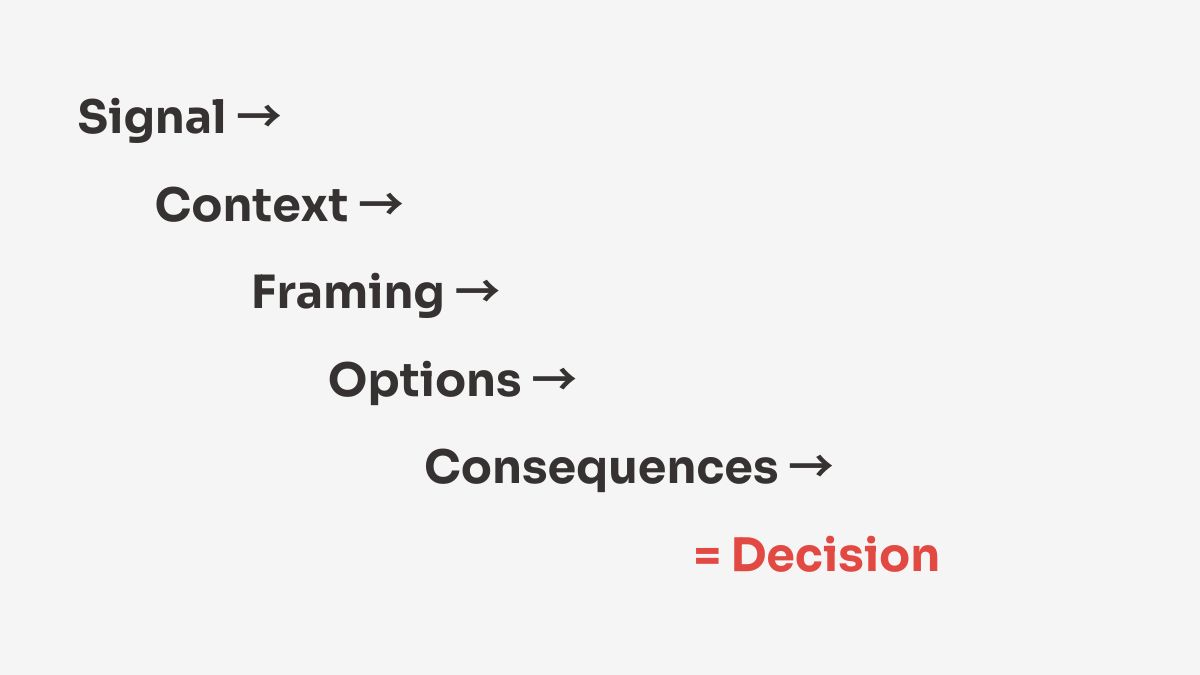
The Cyber Risk-to-Decision Pipeline
Cyber Risk to Decision Engineering works best as a repeatable pipeline rather than a one-off presentation.
A typical pipeline includes:
- Signal Identification
Identify the risk signal that actually threatens objectives—not every technical issue. - Context Framing
Translate the signal into business impact, timing, and relevance. - Decision Scoping
Define the exact decision required and who owns it. - Option Design
Present realistic options with consequences—not generic recommendations. - Decision Handoff
Deliver the risk in a format that enables immediate judgment. - Outcome Tracking
Record the decision, rationale, and accepted risk for future reference.
This pipeline transforms cyber risk from an abstract concern into an organizational action.
Executive-Grade Risk Communication
Decision-engineered risk communication is concise by necessity.
Most executive-grade risk briefings can—and should—fit into 30 seconds. Not because the risk is small, but because clarity is a sign of mastery.
Effective executive risk narratives answer three questions:
- Why does this matter now?
- What are our options?
- What happens next if we choose each path?
When these questions are answered clearly, trust follows.
Leadership in a Decision-Centric Security Model
Cyber Risk-to-Decision Engineering changes the role of security leaders.
The modern security leader is not primarily a risk identifier or control owner. They are a decision engineer, someone who shapes how uncertainty is understood and acted upon at the leadership level.
This requires restraint, confidence, and judgment. It means removing detail instead of adding it. It means resisting the urge to over-educate. It means trusting executives to decide once they are properly oriented.
Organizations that adopt this model often see faster decisions, clearer accountability, and fewer “surprise” incidents—not because risk disappeared, but because it was finally owned.
From Risk Awareness to Decision Maturity
Cyber Risk-to-Decision Engineering is not about better tools or more frameworks. It is about maturity.
Decision-mature organizations:
- Treat risk as an input to leadership, not a technical artifact
- Accept that some risk will remain, and document why
- Make fewer decisions by default and more decisions by design
- Build institutional memory around why choices were made
In a world of constant uncertainty, this maturity becomes a strategic advantage.
Moving Forward
Cyber risk will only continue to grow in complexity. But complexity does not require confusion.
By engineering how risk becomes decisions, organizations move from reactive security postures to intentional leadership outcomes. They stop asking, “Do we understand the risk?” and start asking, “Have we decided?”
That is the shift Cyber Risk to Decision Engineering exists to enable.
If you are ready to move beyond reporting and into real decision influence, this discipline is not optional—it is foundational for security leadership in 2026 and beyond.
If you’re excited to keep learning, share your journey, and connect with others working toward the same goals, I’d love for you to join us at the Join Cyber Launchpad Community.
Together, we can help each other stay ahead, grow as leaders, and make cybersecurity a little less overwhelming for everyone.