In 2026, cyber threats are advancing at lightning speed, putting every organization at risk. The stakes have never been higher, making cybersecurity governance essential for survival and growth. Recent studies show that cyber incidents are rising sharply, and a single misstep can lead to massive losses and damaged trust.
This guide is your roadmap to mastering cybersecurity governance in today’s complex landscape. We’ll walk you through up-to-date frameworks, expert strategies, and actionable tools tailored for IT leaders, CISOs, and business owners. Together, we’ll unlock practical steps that build true resilience, empower confident leadership, and prepare you for what’s next. The risks of waiting are real—let’s get started and secure your organization’s future.
Understanding Cybersecurity Governance in 2026
In 2026, cybersecurity governance is the foundation for organizations seeking trust and resilience in a world where threats are constantly evolving. It is more than a technical checklist; it is a strategic, organization-wide approach to managing risk and safeguarding value. When governance breaks down, so does trust, as seen in recent high-profile breaches. Today, the stakes are higher than ever, making cybersecurity governance a mission-critical priority for every enterprise.
Defining Cybersecurity Governance
Cybersecurity governance is the strategic framework that guides how an organization manages and responds to cyber risks across every level. Unlike day-to-day management, governance sets the vision, policies, and accountability structures that drive secure behaviors and decision-making.
It is the engine behind business resilience and customer trust. When governance is weak, cyber incidents can spiral, as seen in real-world breaches where unclear roles or outdated policies left organizations exposed.
In 2026, cybersecurity governance is more critical than ever. The increasing complexity of digital ecosystems and the speed of new threats demand a proactive, strategic approach that goes beyond traditional IT management.
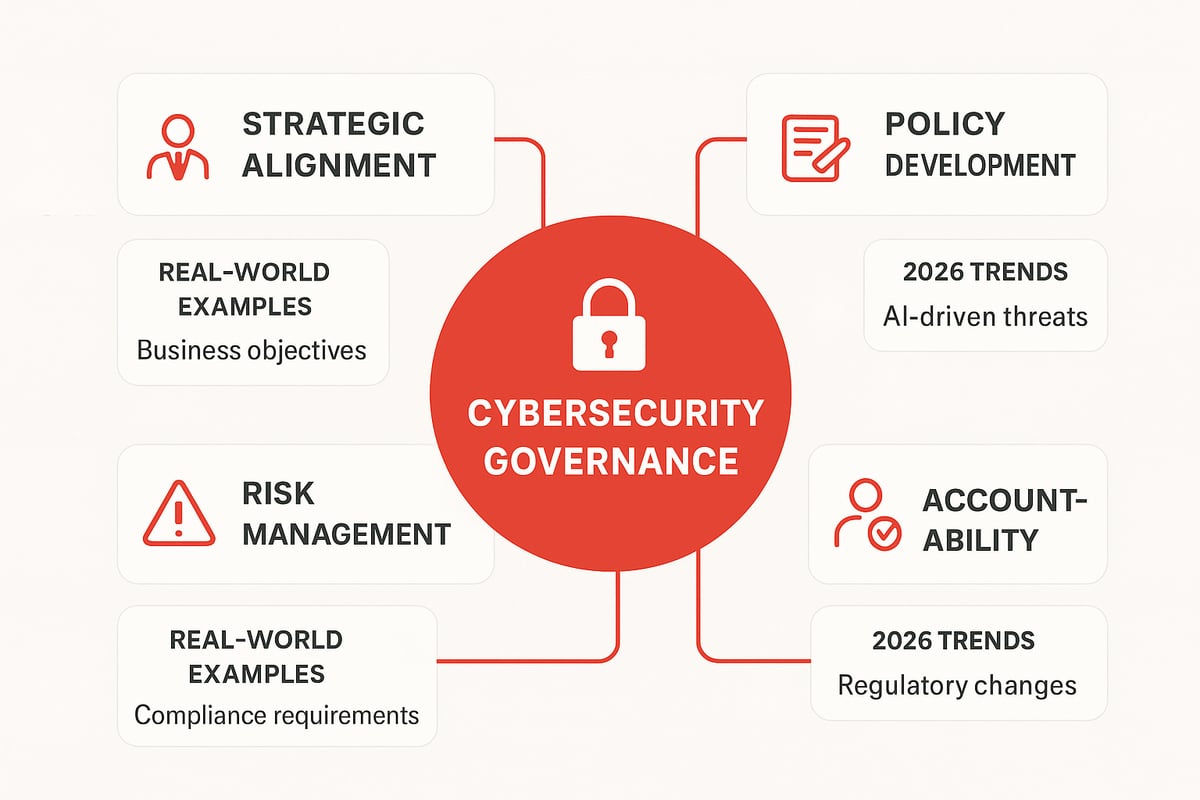
Key Components of Cybersecurity Governance
Effective cybersecurity governance depends on several key components working together:
- Strategic alignment with business goals ensures security supports growth.
- Policy development and enforcement set clear expectations for all staff.
- Ongoing risk management identifies and mitigates threats in real-time.
- Accountability structures clarify who is responsible for each decision.
- Oversight and compliance mechanisms keep everything on track.
For example, integrating governance across departments brings legal, HR, and IT together, creating a unified defense. For a deeper dive into these foundational aspects, check out Governance and compliance essentials.
Governance vs. Management: Why the Difference Matters
Cybersecurity governance defines the direction, while management handles execution. When organizations confuse these roles, they risk creating a fragmented security culture and missing blind spots.
A recent case showed what happens when governance and management are blurred: a large enterprise suffered a costly breach because security managers acted without clear board guidance, leading to inconsistent policies and slow response.
Data from industry surveys shows that only 44 percent of organizations have a clearly defined cybersecurity governance framework in place. Understanding this distinction helps build a culture of accountability and drives better outcomes.
The Evolving Threat Landscape in 2026
Cybersecurity governance must adapt to a threat landscape that is more dynamic than ever before. AI-driven attacks, supply chain vulnerabilities, and new digital transformation initiatives are expanding the attack surface.
Regulators have ramped up scrutiny, and stakeholders now expect robust, transparent governance. According to PwC's 2026 Cybersecurity Outlook, cyber incidents have grown by 22 percent year over year, highlighting the need for vigilant, future-focused governance frameworks.
In 2026, organizations that prioritize cybersecurity governance are better equipped to anticipate risks, respond quickly, and maintain trust in a rapidly changing world.
The Critical Role of Leadership and Culture
A strong cybersecurity governance program starts at the top. Leadership commitment and a culture that values security are the backbone of resilience in 2026. Without engaged executives and a shared sense of accountability, even the best technology falls short. Let’s explore how leadership and culture shape the future of cybersecurity governance.
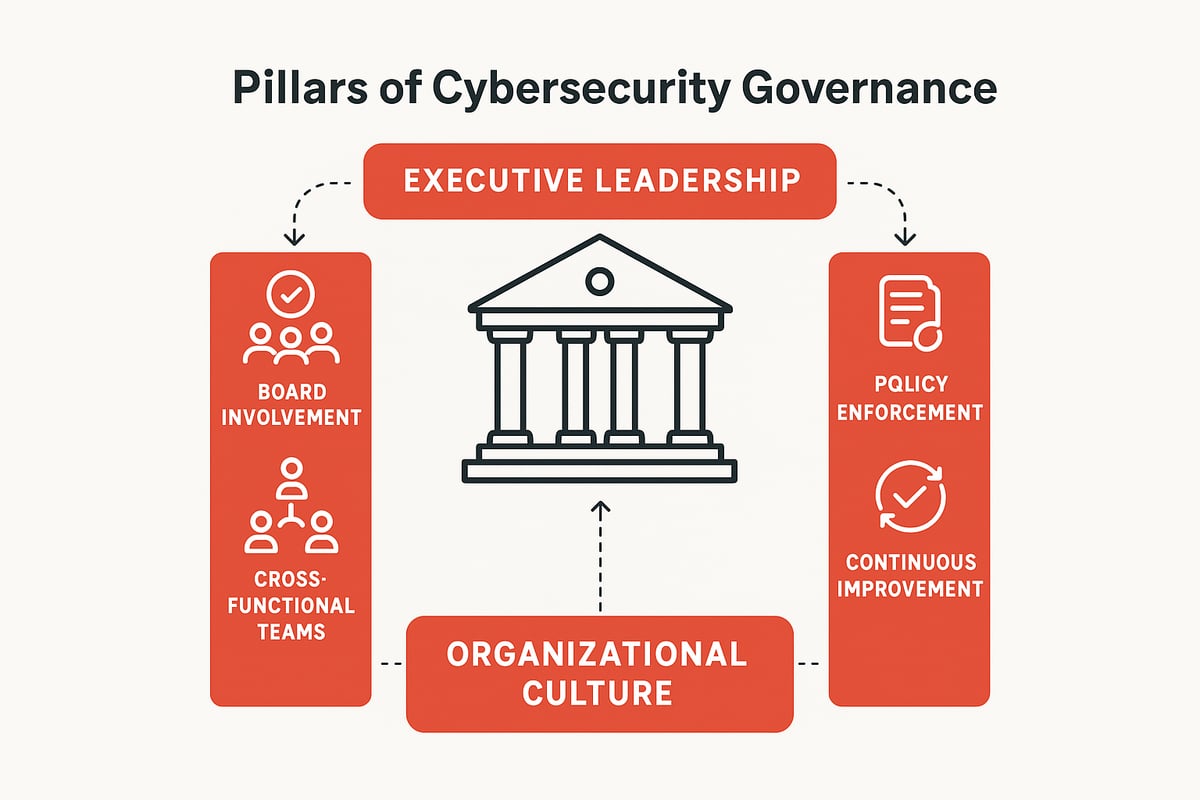
Executive Responsibility and Board Involvement
Executive teams and boards set the tone for cybersecurity governance. Their active participation signals to employees that security is a strategic priority. In 2026, boards are increasingly accountable for cyber risk, with 68% now having dedicated cyber committees, according to industry benchmarks.
When leaders disengage, organizations face greater risk. High-profile breaches often reveal a lack of oversight or unclear responsibilities. Successful boards oversee cyber risk, ask the right questions, and ensure regular reporting. For more on building effective leadership in cybersecurity governance, see Security leadership strategies.
Best practices include setting clear cyber objectives, providing resources, and integrating security discussions into board agendas. This empowers teams to act decisively and build trust across the organization.
Building a Security-First Organizational Culture
Culture is the invisible force driving cybersecurity governance forward. When security becomes part of company values, employees are more likely to make secure choices every day. Incentivizing safe behaviors, such as reporting phishing attempts or following password policies, helps build habits that protect the business.
Resistance to change is common, but with transparent communication and ongoing support, teams adapt. Many organizations have seen dramatic improvements in their cybersecurity governance after launching awareness campaigns and celebrating security champions.
Consider these steps:
- Embed security into onboarding and training.
- Recognize employees who uphold security values.
- Encourage open discussions about cyber risk.
A culture that supports cybersecurity governance turns every employee into a guardian of company assets.
Accountability and Compliance Structures
Clear accountability is essential for effective cybersecurity governance. Assigning roles—such as CISO, IT leads, and business unit champions—ensures everyone knows their part in keeping data safe. Cross-functional teams, including legal and HR, bring diverse perspectives and strengthen oversight.
Ongoing compliance with evolving standards like NIST or ISO 27001 keeps organizations audit-ready. When roles are well-defined, incident response is faster and more coordinated, as shown by companies that cut their response times by 30% after improving accountability structures.
- Define responsibilities in job descriptions.
- Set up regular compliance reviews.
- Foster communication between departments.
Accountability makes cybersecurity governance practical and responsive to new challenges.
LarsBirkeland.com: Practical Leadership Frameworks for Governance
For IT leaders and CISOs seeking hands-on support, LarsBirkeland.com delivers real-world stories and frameworks to strengthen cybersecurity governance. The site’s CISO LaunchPad community connects professionals to share best practices, while templates and checklists help transform technical know-how into strategic action.
You’ll find playbooks focused on communicating cyber risk to business leaders and lessons learned from seasoned executives. By leveraging these resources, organizations build a resilient security culture that adapts to the ever-changing threat landscape.
Access to practical tools and leadership insights empowers teams to elevate cybersecurity governance, turning strategy into daily action.
Developing a Cybersecurity Governance Framework: Step-by-Step
Building a strong cybersecurity governance framework in 2026 is essential for resilience and trust. With threats growing more complex, every organization needs a clear, actionable pathway to success. This step-by-step guide empowers you to craft a governance framework that is modern, adaptive, and robust.
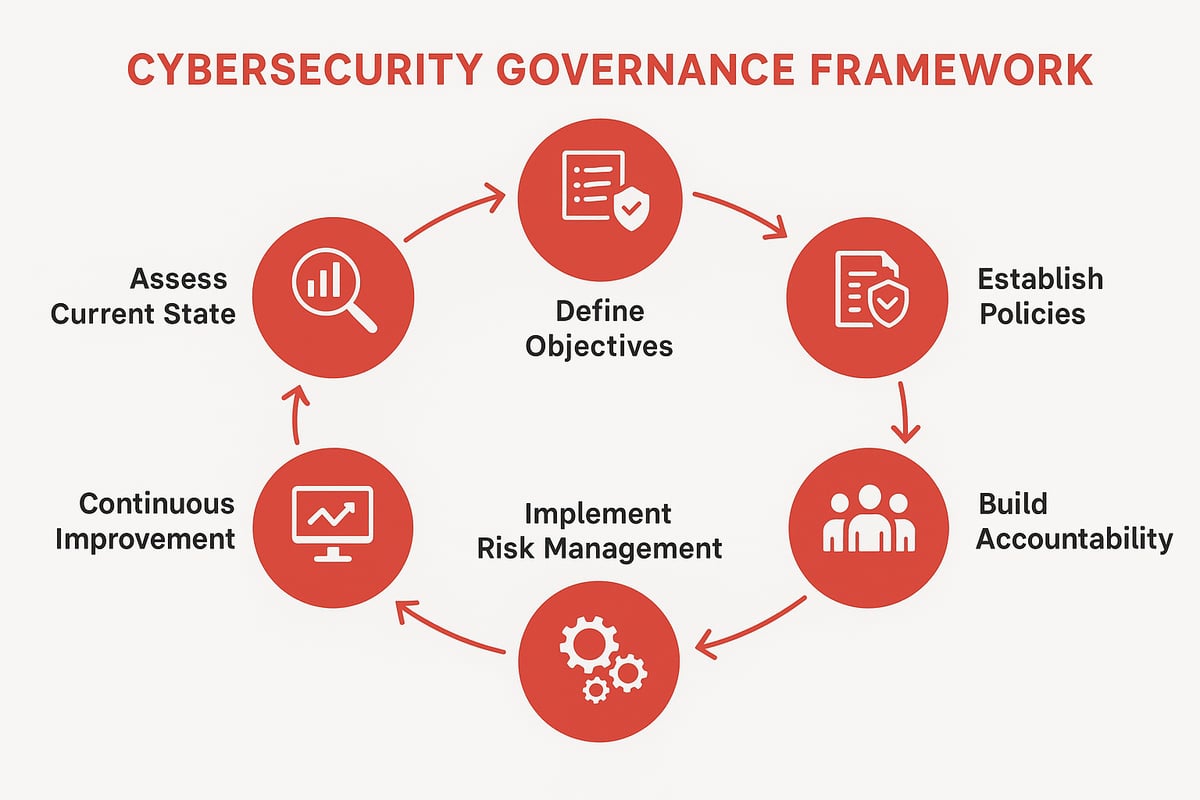
Step 1: Assess Current State and Identify Gaps
Start by taking stock of your current cybersecurity governance environment. Conduct a thorough inventory of existing policies, controls, and governance structures. Use risk assessments and maturity evaluations to uncover gaps and weaknesses. Benchmark your organization against recognized standards, such as NIST or ISO 27001, to gauge your position.
For many mid-sized enterprises, common gaps include outdated policies and unclear accountability. Reviewing a Best cybersecurity frameworks overview can help you select the right reference point for your assessment. Remember, knowing where you stand is the foundation of strong cybersecurity governance.
Step 2: Define Governance Objectives and Scope
Once you understand your baseline, define clear cybersecurity governance objectives that align with your business strategy. Set your organization’s risk appetite and tolerance, making sure leadership and stakeholders are on board.
Decide if your framework will be enterprise-wide, department-specific, or a hybrid approach. For example, fintech companies often require stricter controls than healthcare, reflecting unique regulatory needs. Defining the scope ensures your cybersecurity governance efforts are focused, measurable, and relevant.
Step 3: Establish Policies, Standards, and Procedures
Next, develop enforceable cybersecurity policies that reflect your objectives. Standardize procedures for incident response, data protection, and access control. Integrate regulatory and compliance requirements into every step.
Consider using policy templates for rapid deployment and consistency. Clear documentation helps teams understand expectations, reducing ambiguity. Well-crafted policies are the backbone of effective cybersecurity governance and support smooth day-to-day operations.
Step 4: Build Accountability and Oversight Mechanisms
Assign clear roles and responsibilities for cybersecurity governance. Define reporting lines, decision-making processes, and escalation paths. Form governance committees or cross-functional working groups to oversee implementation and address issues promptly.
When teams from IT, HR, and business units collaborate, oversight improves significantly. For instance, a cross-functional committee can spot risks sooner and respond faster, leading to stronger cybersecurity governance and a culture of shared responsibility.
Step 5: Implement Risk Management Processes
Effective cybersecurity governance relies on continuous risk management. Identify, assess, and mitigate risks using both manual and automated tools for real-time monitoring. Integrate risk management with your broader enterprise risk management (ERM) program.
Automation can lighten the manual workload, freeing up resources for strategic tasks. For example, organizations that automate risk assessments often see a noticeable reduction in time spent on repetitive tasks, allowing cybersecurity governance teams to focus on higher priorities.
Step 6: Monitor, Measure, and Report
Define key performance indicators (KPIs) and metrics to track the effectiveness of your cybersecurity governance framework. Regularly report findings to leadership and stakeholders, using dashboards and automated reporting tools for clarity.
Metrics such as policy adherence rates and incident response times drive accountability and highlight areas for improvement. Transparent reporting fosters trust and demonstrates your commitment to cybersecurity governance at every level.
Step 7: Continuous Improvement and Adaptation
Cybersecurity governance is never static. Schedule regular reviews and updates of your framework based on incidents, audits, and new threat intelligence. Encourage a feedback loop where lessons learned inform future strategy.
Organizations that adapt quickly after regulatory changes or cyber incidents stay ahead of risks. In 2025, many companies successfully pivoted their cybersecurity governance approaches in response to evolving regulations, proving the value of agility and continuous learning.
Regulatory Trends and Compliance in 2026
Staying ahead of regulatory changes is essential for effective cybersecurity governance. In 2026, organizations face heightened scrutiny and new standards that demand a proactive, strategic approach. Let’s explore the evolving compliance landscape and how we can adapt together.
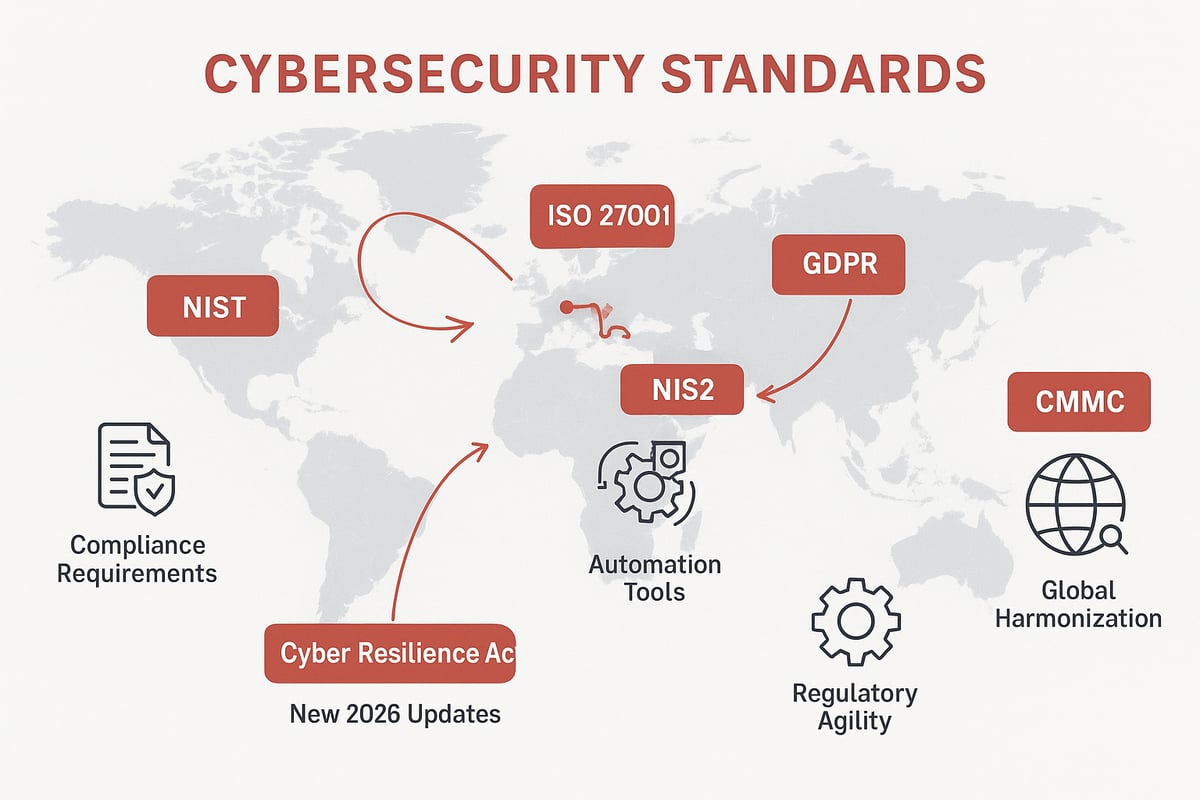
Major Regulatory Frameworks and Standards
In 2026, the landscape of cybersecurity governance is shaped by a blend of established and emerging frameworks. Standards like NIST, ISO 27001, GDPR, and HIPAA remain foundational, but new regulations such as NIS2 and the Cyber Resilience Act Overview are setting higher bars for compliance and accountability.
For example, NIS2 is expanding its reach across Europe, affecting more sectors and requiring stricter incident reporting. Adoption rates of these frameworks are climbing, as organizations recognize that robust cybersecurity governance is key to building trust, meeting legal obligations, and protecting digital assets.
Navigating Global Compliance Challenges
Managing compliance across borders is growing more complex. Organizations must juggle multi-jurisdictional requirements and navigate varying data privacy laws. This complexity often calls for harmonized policies that align with global standards while respecting local regulations.
Multinational enterprises, for instance, face challenges when synchronizing their cybersecurity governance efforts in regions with conflicting rules. Adopting a unified yet flexible approach, supported by cross-functional teams, helps bridge these gaps and fosters smoother compliance worldwide.
Integrating Compliance into Governance
Integrating compliance seamlessly into daily operations is a cornerstone of modern cybersecurity governance. Automation is transforming the way organizations monitor and report compliance, reducing manual workloads and improving accuracy.
Automated compliance tools are gaining popularity, with a growing percentage of organizations leveraging these solutions to streamline audit preparation and ongoing monitoring. Embedding compliance into governance frameworks ensures that oversight is continuous, and that organizations can quickly adapt to new regulatory requirements.
Preparing for Future Regulatory Changes
The regulatory landscape will continue to evolve, especially with the rise of AI regulations and data sovereignty laws. Forward-thinking organizations are building agile cybersecurity governance frameworks that can swiftly respond to new legislation.
Some businesses have already demonstrated agility by proactively adjusting to updates like GDPR, staying ahead of the curve. Industry surveys show that organizations prioritizing adaptability and scenario planning are better prepared for future regulatory shifts, making resilience a competitive advantage.
Implementing and Operationalizing Cybersecurity Governance
Turning a cybersecurity governance framework into daily practice is where the real work—and rewards—begin. Successful implementation means weaving governance into every layer of the organization, from the server room to the boardroom. Let’s explore how to put strategy into action and create lasting resilience.
Building Cross-Functional Teams and Collaboration
Cybersecurity governance thrives on teamwork. It is not just IT’s responsibility—legal, HR, risk management, and business units all play vital roles. Bringing these groups together breaks down silos, ensuring that everyone understands their part in protecting the organization.
Cross-functional teams help spot gaps and blind spots that a single department might miss. For example, when HR and IT collaborate, onboarding and offboarding processes become more secure. This holistic approach makes cybersecurity governance a shared mission, not an isolated task.
Leveraging Technology and Automation
Modern cybersecurity governance depends on technology to manage complexity and scale. Tools like Governance, Risk, and Compliance (GRC) platforms, automated monitoring, and evidence collection make oversight more efficient. Automated solutions speed up audits and help ensure policies are followed consistently.
For risk management, organizations increasingly rely on specialized cyber risk assessment tools to identify, prioritize, and mitigate threats in real time. These platforms integrate with existing systems, providing a single source of truth for governance activities. Embracing automation frees up teams to focus on strategy, not paperwork.
Training, Awareness, and Change Management
No cybersecurity governance program is complete without people. Ongoing training ensures employees know how to spot threats and respond effectively. Tailored awareness campaigns address the unique risks faced by different roles, making the message relevant and memorable.
Change can be tough, but with strong leadership and clear communication, even the most skeptical team members can become security champions. Regular simulations, such as phishing tests, reinforce good habits and show measurable progress. Building a culture of vigilance is essential to lasting success.
Incident Response and Crisis Management Integration
A strong incident response plan is the backbone of cybersecurity governance. Integrating these plans with governance frameworks ensures a swift, coordinated reaction when things go wrong. Cross-functional teams participate in regular tabletop exercises, testing their readiness against real-world scenarios.
Lessons from recent breaches show that well-prepared organizations recover faster and minimize damage. Incident response is not just about stopping attacks—it is about learning and adapting. Embedding these practices into cybersecurity governance helps organizations bounce back stronger every time.
Measuring Success: Metrics and KPIs
You cannot improve what you do not measure. Effective cybersecurity governance uses clear metrics to track progress, such as policy adherence, incident response times, and risk reduction. Dashboards and automated reporting tools make it easy to share results with leadership and stakeholders.
Staying informed about audit trends and risk areas is also crucial. According to Gartner’s 2026 Audit Plan Hot Spots, internal auditors are focusing more on cybersecurity vulnerabilities and governance effectiveness. Benchmarking against peers helps organizations set ambitious, achievable goals.
Overcoming Common Implementation Challenges
Bringing cybersecurity governance to life is not always smooth sailing. Common obstacles include limited resources, competing priorities, and resistance to change. Overcoming these challenges takes creativity and persistence.
Start by securing executive support and communicating the value of governance. Use quick wins to build momentum, like automating repetitive tasks or improving response times. Celebrate progress and share success stories to keep everyone engaged. With the right mindset and tools, any organization can make cybersecurity governance a lasting reality.
Future-Proofing Cybersecurity Governance: Trends and Innovations
The pace of change in cybersecurity governance is accelerating. As we look toward the future, organizations must stay ahead of new threats and evolving business demands. Let’s break down the most important trends shaping how we build and sustain effective cybersecurity governance for the years ahead.
Adapting to Emerging Technologies and Threats
Artificial intelligence, machine learning, and quantum computing are reshaping the threat landscape. Attackers now use AI to automate reconnaissance, bypass defenses, and scale phishing campaigns. At the same time, defenders leverage these technologies to predict, detect, and respond to incidents faster.
Cybersecurity governance must adapt by incorporating these innovations into risk assessment and policy development. For example, quantum-safe encryption and AI-driven monitoring are quickly becoming industry standards. According to PwC’s 2026 Cybersecurity Outlook, organizations that proactively integrate emerging technologies into their cybersecurity governance frameworks are better positioned to manage new risks.
The Rise of Integrated Risk Management (IRM)
Traditional risk management often operates in silos, but integrated risk management (IRM) brings together security, compliance, and business risk under a single umbrella. This shift improves visibility, speeds up decision-making, and aligns cyber strategy with business goals.
With IRM, cybersecurity governance becomes more agile and responsive. Teams can prioritize risks based on real business impact, rather than isolated technical issues. Many enterprises now use IRM platforms to centralize oversight, automate reporting, and break down barriers between departments.
By adopting IRM, organizations enhance their ability to adapt governance to changing threats and regulatory expectations. This holistic approach is quickly becoming the gold standard for cybersecurity governance.
The Evolving Role of the CISO and Security Leadership
The Chief Information Security Officer (CISO) is no longer just a technical expert. Today’s CISO is a strategic leader, engaging with the board and driving organizational change. The evolution of cybersecurity governance means CISOs must translate complex risks into business language, ensuring executives and employees understand their roles.
More companies are forming dedicated cyber committees at the board level. This elevates cybersecurity governance from IT concern to business priority. As a result, CISOs gain greater influence in shaping strategy, culture, and investment.
Organizations that empower CISOs and foster leadership collaboration see measurable improvements in governance maturity and overall security.
Building Resilience and Agility for the Future
Resilient organizations are ready for anything. Cybersecurity governance frameworks must enable rapid adaptation to new threats, regulations, and business models. Scenario planning, regular exercises, and continuous feedback are key elements.
Global standards and integrated defense strategies, like those outlined in CISA’s 2025-2026 International Strategic Plan, set the foundation for agile governance. By adopting flexible policies and encouraging proactive risk management, companies build a culture that thrives amid uncertainty.
Ultimately, future-proofing cybersecurity governance means staying informed, embracing innovation, and prioritizing resilience at every level.
If you’ve made it this far, you’re clearly committed to building a stronger, more resilient security program—one that goes beyond buzzwords and actually moves the needle. We all know the challenges: limited time, evolving threats, and the pressure to communicate cyber risk in a way business leaders get. You don’t have to go it alone. Let’s keep the conversation going and support each other as we turn practical strategies into real change. Want to connect with peers, share stories, and find fresh frameworks that work in the real world Join us at Join CISO Launchpad—your community for cybersecurity leaders who care about doing things differently.