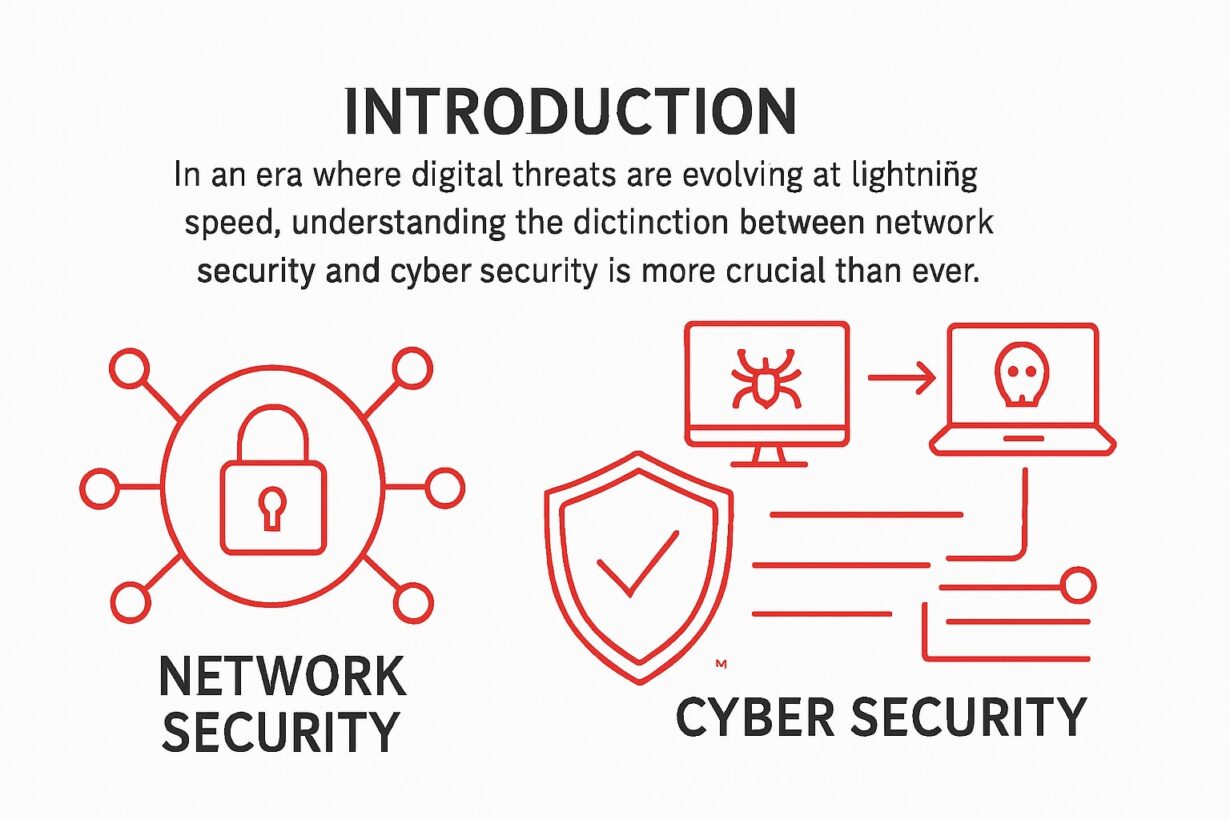
Did you know that global cyber attacks surged by over 30% in the past year alone? As digital threats multiply, the confusion between network security and cyber security leaves many organizations exposed.
Understanding the difference between network security and cyber security is essential for anyone aiming to build resilience against modern threats. For IT professionals, business leaders, and security fans, knowing where these disciplines overlap and diverge can make all the difference.
In this article, we will define both terms, compare their core functions, explore real-world applications, analyze career paths, and share strategies for creating a strong digital defense in 2026. Let’s get started on this journey to confident security decision-making.
Defining Network Security and Cyber Security
Understanding the difference between network security and cyber security is more important than ever as we look toward 2026. Both are vital for protecting digital assets, but each has its unique focus and approach. Let’s break down what sets them apart and how they work together to keep us safe.
What is Network Security?
Network security and cyber security are often mentioned together, but network security is a specialized field focused on protecting computer networks and the data moving through them. It involves a mix of physical and digital measures designed to block unauthorized access, misuse, and attacks targeting network infrastructure.
Core components of network security include:
- Firewalls that filter traffic and block threats
- Intrusion detection and prevention systems (IDS/IPS)
- Network segmentation, which isolates sensitive areas
For example, network security might prevent malware from spreading across a company’s local area network (LAN), stopping a threat before it can reach critical systems.
Network security and cyber security are closely linked, but network security is often seen as a foundational layer. It works behind the scenes to ensure data safely moves within and between systems. As noted by the SANS Institute, network security relies on both physical protections and software tools to keep infrastructure safe. For a deeper dive into these principles, see What Is Network Security?.
What is Cyber Security?
While network security and cyber security share some goals, cyber security casts a wider net. Cyber security is the practice of protecting all digital assets, including systems, networks, devices, applications, and users, from a broad range of digital attacks.
Key components of cyber security include:
- Endpoint security for devices like laptops and phones
- Application security to protect software from vulnerabilities
- Cloud security for remote data and services
- Identity and access management to control user permissions
A typical example is defending organizations from phishing scams, ransomware, or data breaches that target employees or sensitive information. Cyber security reaches beyond just the network, addressing threats to data at rest and in use, as well as in transit.
Network security and cyber security often overlap, but cyber security is considered the broader discipline. It treats network security as one of its pillars, ensuring protection across the entire digital environment. Cisco defines cyber security as the defense of systems, networks, and programs from digital attacks—a vast landscape requiring constant vigilance.
Shared Goals and Overlap
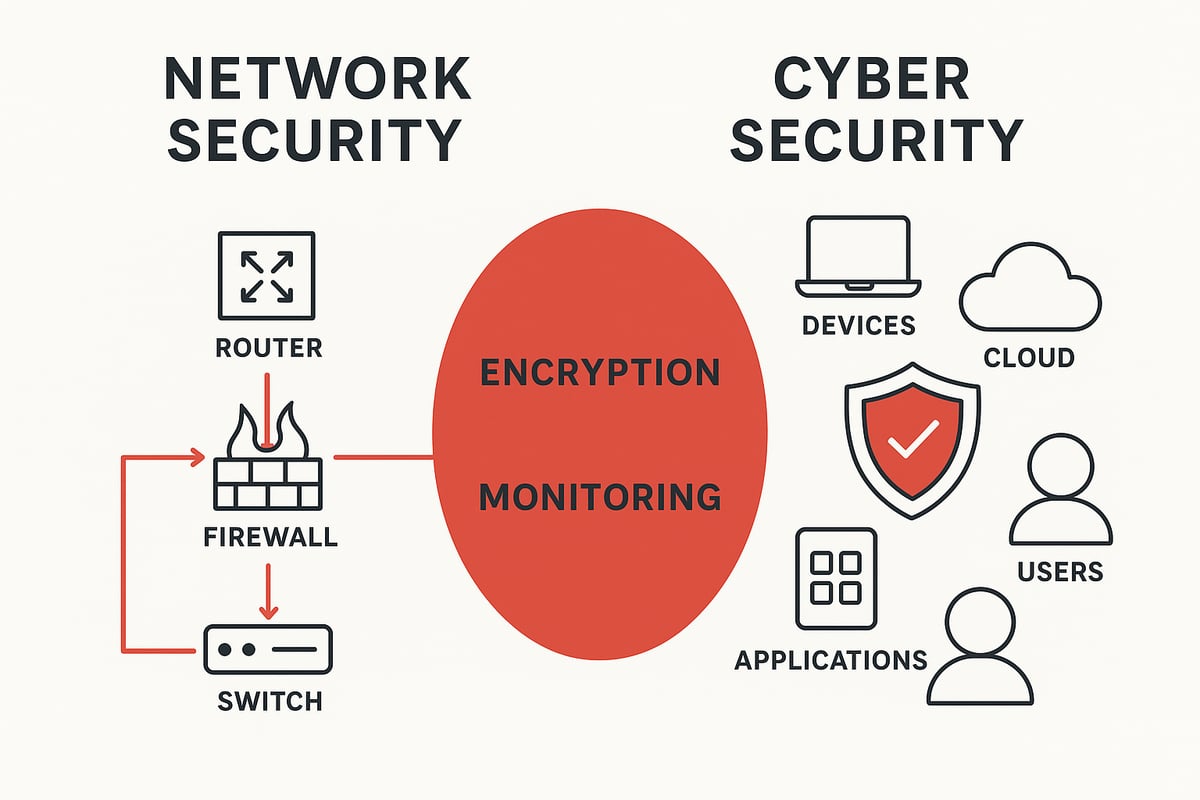
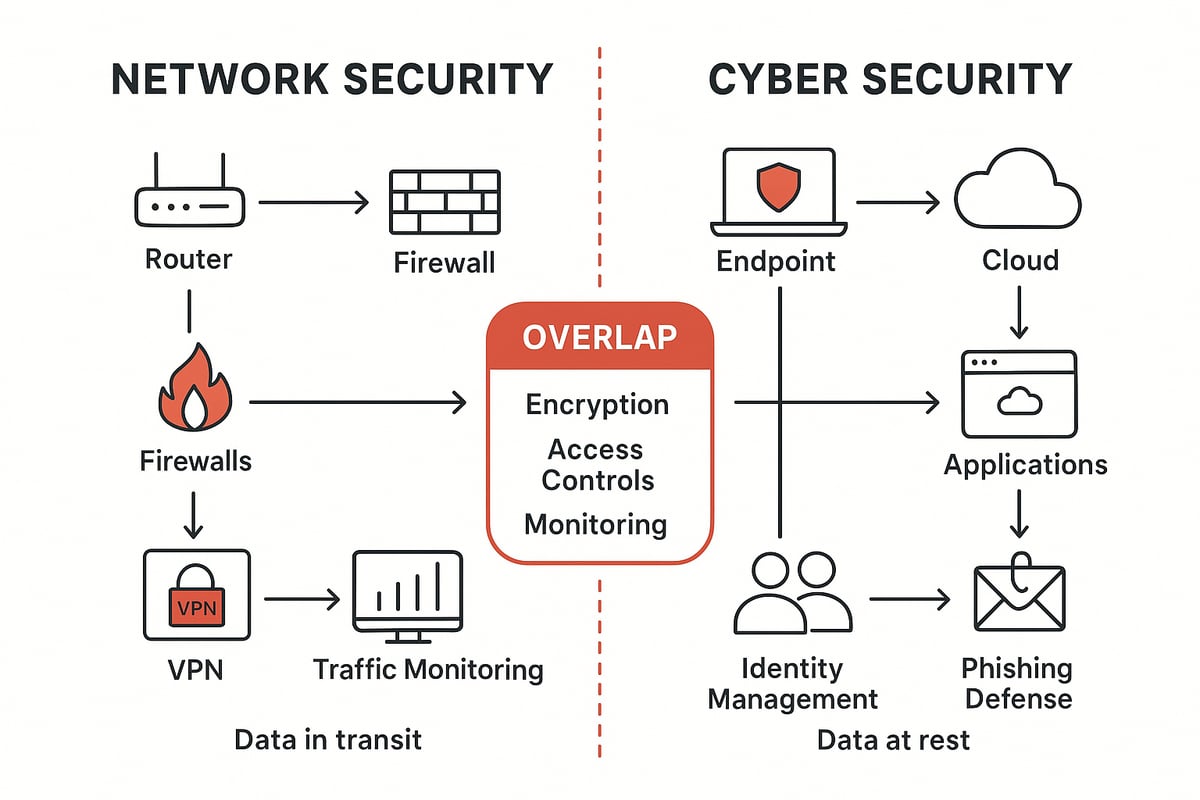
At their core, network security and cyber security aim to protect digital assets while ensuring confidentiality, integrity, and availability. Both use similar measures, such as:
- Encryption to scramble sensitive data
- Access controls to restrict entry
- Monitoring tools to detect unusual activity
For example, multi-factor authentication is used in both network security and cyber security to verify user identities and prevent unauthorized access. Even though their responsibilities sometimes overlap, each has unique areas of focus that are crucial for a strong, unified defense.
Core Functions and Objectives: Network Security vs. Cyber Security
Understanding the core functions and objectives of network security and cyber security is essential for anyone looking to build a strong digital defense in 2026. While both fields aim to keep our data and systems safe, their unique focuses and strategies play distinct roles in the broader security landscape.
Primary Objectives of Network Security
Network security and cyber security both share the goal of protecting digital assets, but network security zeroes in on safeguarding the pathways our data travels. Its primary mission is to secure networks from unauthorized access, misuse, and various attacks that could disrupt operations.
Key objectives of network security include:
- Protecting data as it moves across internal and external networks
- Preventing unauthorized users from accessing sensitive network resources
- Ensuring the reliability and uptime of the network infrastructure
- Mitigating threats such as DDoS attacks, worms, and trojans
For example, a financial institution facing a potential DDoS attack relies on network security measures like firewalls and intrusion prevention systems to keep services online. Network segmentation can also isolate threats, stopping malware from spreading laterally.
A foundational approach to network security and cyber security involves layering multiple defenses. This includes physical safeguards as well as software-based solutions. If you want a deeper dive into practical defenses, check out this Network Security Solutions Overview for insights into current strategies.
Ultimately, network security and cyber security overlap here, but network security is the backbone, focusing on the safe transit of information and the integrity of connections we rely on every day.
Primary Objectives of Cyber Security
When we talk about network security and cyber security, cyber security takes a broader view. Its core focus is to defend all digital assets, from endpoint devices and servers to cloud applications and user identities, against an ever-evolving set of threats.
The main objectives of cyber security are:
- Defending against a wide array of cyber threats, including malware, phishing, and ransomware
- Protecting endpoint devices, data stored on disk, and applications from compromise
- Enforcing security policies and best practices across the organization
- Ensuring compliance with data privacy regulations and industry standards
A good example is an organization launching a security awareness program to help employees recognize phishing emails. While network security might block suspicious traffic, cyber security empowers users and systems to detect and respond to threats before they escalate.
Cyber security also integrates with network security and cyber security tools, such as endpoint detection and response (EDR) platforms, identity management, and cloud security controls. These layers work together to protect not only the network but also the devices and data within it.
As threats grow more sophisticated, the objectives of network security and cyber security must expand. This means staying vigilant about both technical vulnerabilities and human factors.
How Their Approaches Differ
Although network security and cyber security are intertwined, their approaches to safeguarding digital environments are quite distinct. Network security traditionally focuses on the perimeter and the infrastructure, using hardware and software appliances to control traffic and access.
In contrast, cyber security is concerned with a wider range of assets, including endpoints, applications, data in the cloud, and user identities. While network security might deploy firewalls and VPNs, cyber security adopts solutions like zero trust models that verify every user and device, regardless of location.
For example, network segmentation is a classic network security technique, dividing the network into isolated sections to limit the spread of threats. Meanwhile, cyber security’s zero trust approach assumes that threats can originate anywhere, so every access request is continuously validated.
The rise of remote work and cloud adoption has blurred traditional boundaries between network security and cyber security. Today, organizations must blend both approaches, ensuring that security extends from the core network to every endpoint and cloud service.
By understanding these differences, we can see how network security and cyber security complement each other. This knowledge empowers us to build a layered, resilient defense ready for whatever 2026 brings.
Key Differences Between Network Security and Cyber Security
Understanding the key differences between network security and cyber security is essential for anyone aiming to protect digital assets in 2026. These two fields are closely related, but their unique characteristics shape how organizations defend against threats. Let’s break down the most important distinctions.
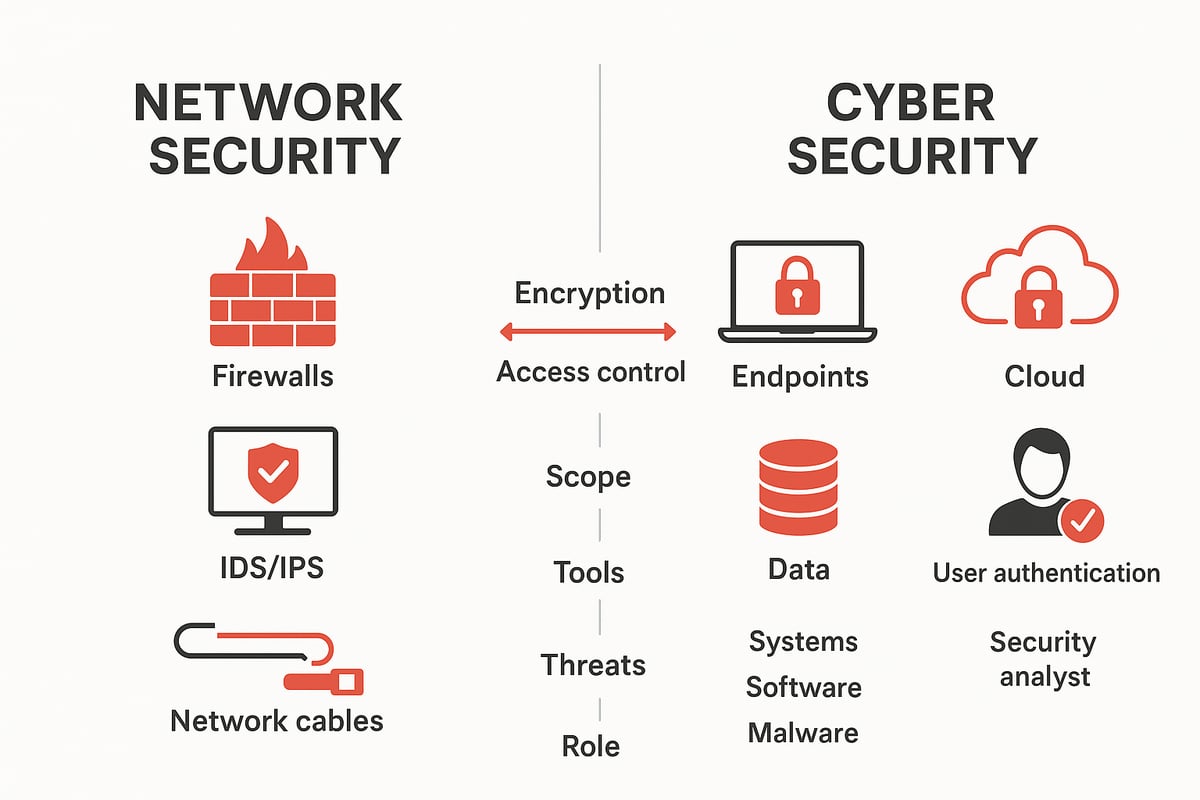
Scope and Coverage
At the core, network security and cyber security differ in their overall scope. Network security focuses on protecting the infrastructure that allows data to flow between devices. This means safeguarding routers, switches, and the pathways that connect computers and servers. It’s about ensuring only authorized users and devices can access the network.
Cyber security, on the other hand, covers the entire digital environment. This includes networks, but also devices, applications, cloud services, and the data itself—whether it’s at rest, in transit, or in use. For a deeper dive into how these distinctions compare to other security domains, check out this Key Differences: Information Security vs Cybersecurity resource.
By understanding where network security and cyber security overlap and where they diverge, organizations can better allocate resources and expertise.
Types of Threats Addressed
Both network security and cyber security are designed to shield against a variety of threats, but the types they focus on can differ. Network security commonly deals with dangers like DDoS attacks, man-in-the-middle exploits, sniffing, and unauthorized access attempts. These threats specifically target the communication channels and network infrastructure.
Cyber security casts a wider net, fighting off phishing emails, ransomware, advanced persistent threats, and insider attacks. These threats can bypass traditional network defenses and often exploit human error or software vulnerabilities.
A strong understanding of network security and cyber security helps teams spot and stop evolving threats before they cause damage.
Tools and Technologies Used
The tools and technologies used in network security and cyber security reflect their unique priorities. Network security relies on firewalls, intrusion detection and prevention systems (IDS/IPS), and network access controls to create boundaries and monitor traffic.
In contrast, cyber security uses antivirus solutions, endpoint detection and response (EDR), security information and event management (SIEM), and cloud security tools. These solutions focus on protecting data, devices, and applications wherever they reside.
Selecting the right mix of network security and cyber security tools is crucial for building a resilient defense.
Data Protection Focus
When it comes to data, network security and cyber security have different areas of emphasis. Network security is primarily concerned with data in motion—protecting information as it travels across the network. Techniques like VPNs and encrypted tunnels are vital here.
Cyber security covers data in motion, at rest (stored data), and in use (actively processed data). This means encrypting files on disk, securing databases, and safeguarding information as it’s accessed by users or applications.
A balanced approach to network security and cyber security ensures that sensitive information is always protected, regardless of where it lives.
Organizational Hierarchy and Roles
Within organizations, network security and cyber security often have distinct roles and structures. Network security is sometimes viewed as a specialized subset within the larger cyber security team, focusing on infrastructure and connectivity. Job titles might include Network Security Engineer or Network Architect.
Cyber security roles, such as Cyber Security Analyst or Architect, handle broader responsibilities like policy development, incident response, and compliance. These teams look at the big picture, weaving network security measures into a larger strategy.
Understanding how network security and cyber security fit into the organizational chart helps leaders assign responsibilities and streamline communication.
Real-World Case Study: Impact of Overlapping and Distinct Security Measures
Imagine a ransomware attack that exploits a network vulnerability, quickly spreading across a company’s systems. If network security controls are weak, the malware can move laterally with ease. At the same time, lacking endpoint protection means the attack is not detected or stopped at individual devices.
This scenario shows why a layered approach—combining network security and cyber security—is vital. By integrating both, organizations can block threats at multiple points and reduce the risk of a single failure leading to catastrophe.
Real-World Applications and Use Cases
In today’s digital-first world, real-life scenarios reveal just how vital network security and cyber security have become. Let’s dive into how these strategies play out in organizations, protecting our data, people, and operations every day.
Network Security in Action
Network security and cyber security are both essential, but network security specifically focuses on keeping the digital highways within an organization safe and efficient. Imagine a company with hundreds of employees, each accessing confidential files, applications, and cloud services daily. To keep this environment secure, IT teams deploy firewalls, intrusion prevention systems, and virtual private networks (VPNs) to shield internal data as it travels between devices.
Firewalls are like the security gates of a building, making sure only authorized communication gets in or out. VPNs encrypt data, protecting sensitive information when employees work remotely or connect from branch offices. These measures help prevent malware from spreading if a single device is compromised and stop cyber criminals from launching distributed denial-of-service (DDoS) attacks that could slow or shut down operations.
A real-world example is a financial institution defending against a sudden surge in malicious traffic designed to overwhelm its systems. With strong network security and cyber security controls, the IT team can quickly detect abnormal patterns, block harmful traffic, and keep customer services running smoothly.
Network security and cyber security also contribute to overall network performance. By stopping unauthorized access and limiting the spread of malware, organizations experience fewer outages and bottlenecks, making the digital experience smoother and more reliable for everyone.
Cyber Security in Action
While network security and cyber security overlap, cyber security casts a wider net, focusing on protecting all digital assets, from endpoints to cloud applications. Let’s say an employee receives a convincing phishing email. If they click a malicious link, cyber security tools like endpoint detection and response (EDR) software jump into action, isolating the threat before it spreads.
Cyber security teams regularly train staff to recognize social engineering tactics, reducing the risk of human error. They enforce multi-factor authentication to make it harder for attackers to gain access, even if passwords are stolen. In the cloud, cyber security measures safeguard sensitive data stored in SaaS platforms and ensure compliance with privacy regulations.
Consider a healthcare provider targeted by ransomware. Thanks to a layered approach involving both network security and cyber security, the organization can detect the attack, quarantine affected systems, and restore operations from secure backups, minimizing downtime and financial loss.
These real-world examples show that network security and cyber security work together to protect not just the network, but also the people, devices, and information that rely on it every day.
Integration and Collaboration
The most resilient organizations treat network security and cyber security as two sides of the same coin. Instead of keeping teams and tools separate, they encourage collaboration and shared intelligence. For instance, when a suspicious event occurs, both network and cyber security experts join forces to investigate, contain, and remediate the threat.
Coordinated incident response is key. If a breach is detected at the network level, cyber security analysts dig deeper into affected endpoints and user accounts. Regular communication and joint drills ensure everyone knows their role when seconds count.
Industry leaders agree that siloed approaches leave gaps. Bringing network security and cyber security together makes it easier to adapt to new threats and technologies. As highlighted in 2026 Security Trends: From Complexity to Control, aligning these strategies is essential for building a comprehensive defense in the evolving digital landscape.
By working as a unified team, organizations can face the future with confidence, knowing their digital world is protected from every angle.
Career Paths, Skills, and Industry Trends
Choosing a career in network security and cyber security means stepping into a field that is both dynamic and rewarding. These paths offer opportunities to protect organizations, shape digital futures, and make a real impact. Whether you are just starting or looking to advance, understanding the skills, roles, and trends shaping network security and cyber security can help you carve out your place in this rapidly evolving landscape.
Roles and Responsibilities in Network Security
Careers in network security and cyber security often begin with specialized roles focused on safeguarding IT infrastructure. In network security, professionals like Network Security Engineers and Network Architects are responsible for designing, implementing, and maintaining secure network environments.
Common responsibilities include:
- Configuring and managing firewalls to block unauthorized access
- Setting up intrusion detection and prevention systems (IDS/IPS)
- Monitoring network traffic for unusual activity
- Managing Virtual Private Networks (VPNs) for secure remote access
A typical day might involve analyzing network logs, responding to alerts, and fine-tuning access controls. Strong knowledge of network protocols, switching, and routing is essential. For example, a Network Security Engineer might catch an attempted breach by identifying suspicious lateral movement within the corporate LAN.
According to industry reports, network security and cyber security professionals focusing on infrastructure play a vital role in reducing downtime and ensuring business continuity. As organizations expand their digital footprint, the demand for these skills continues to rise.
Roles and Responsibilities in Cyber Security
The world of cyber security is broad, encompassing everything from protecting endpoints to securing cloud applications. Cyber Security Analysts, Cyber Security Architects, and Incident Responders all play crucial roles in defending against a wide range of threats.
Key skills for these roles include:
- Threat analysis and vulnerability assessment
- Incident response and digital forensics
- Developing and enforcing security policies
- Conducting security audits and compliance checks
For instance, a Cyber Security Analyst might conduct a vulnerability scan, identify a critical weakness, and coordinate with IT to patch the system before attackers exploit it. These professionals also educate users, helping prevent social engineering attacks.
Want to dive deeper into these roles? Check out Cybersecurity Explained for Beginners for a comprehensive introduction to the essential concepts and responsibilities in cyber security. As organizations embrace cloud and mobile technologies, network security and cyber security roles are evolving, often requiring cross-disciplinary expertise.
Industry Trends and Future Outlook for 2026
Looking ahead to 2026, several trends are shaping the future of network security and cyber security. The boundaries between these disciplines are blurring as organizations adopt cloud, mobile, and Internet of Things (IoT) technologies. Many companies are merging network and cyber security teams to improve collaboration and efficiency.
Artificial intelligence and automation are becoming standard in threat detection, enabling faster responses to complex attacks. The adoption of zero trust architectures is also accelerating, requiring professionals to rethink traditional perimeter-based defenses.
To stay ahead, keep an eye on Cybersecurity Trends in 2026: AI Defense and Digital Trust, which highlights how AI, digital trust, and integrated strategies are transforming the way network security and cyber security operate. Organizations will increasingly seek talent with both technical and strategic skills.
Educational Pathways and Certifications
Building a successful career in network security and cyber security starts with the right education and certifications. Many professionals begin with a degree in computer science, information technology, or a related field, but hands-on experience is just as valuable.
Popular certifications include:
- CompTIA Security+
- Cisco Certified Network Associate (CCNA) Security
- Certified Information Systems Security Professional (CISSP)
- Certified Ethical Hacker (CEH)
Training programs and bootcamps can help you gain practical skills and prepare for industry exams. Some universities now offer master’s programs focused on integrated network security and cyber security, reflecting the growing need for versatile experts.
Whether you are interested in protecting networks, responding to cyber incidents, or leading security strategy, there is a place for you in network security and cyber security. The journey is challenging but deeply rewarding.
Building a Comprehensive Security Posture for 2026
Creating a resilient digital defense in 2026 means weaving network security and cyber security into every layer of your organization. The landscape is shifting fast, so we need strategies that adapt, connect, and empower everyone from technical teams to business leaders.
Aligning Network and Cyber Security Strategies
To build a strong foundation, organizations must align network security and cyber security strategies. This means moving beyond isolated solutions and uniting policies, processes, and technologies.
A unified approach lets us protect data in motion and at rest, secure endpoints, and defend against evolving threats. For example, combining network segmentation with zero trust access controls ensures no single point of failure. With the shift toward cloud and remote work, it’s essential that network security and cyber security teams collaborate on shared goals.
The 2026 Cybersecurity Outlook: PwC emphasizes the rise of identity-centric operations, showing how integrated strategies empower organizations to adapt quickly. By aligning your efforts, you can close security gaps and build resilience for the future.
Implementing Best Practices and Frameworks
Adopting proven frameworks is key to a comprehensive security posture. Standards like NIST and ISO 27001 encourage organizations to weave network security and cyber security controls into daily operations.
Start with regular risk assessments and security audits. These help identify vulnerabilities across networks, endpoints, and cloud environments. Pair technical controls like network segmentation with user-focused measures such as security awareness training. This dual focus ensures both the technical and human elements are protected.
When network security and cyber security teams work from the same playbook, organizations gain a holistic defense. This creates a culture of accountability and continuous improvement, making it easier to adapt as new threats emerge.
Addressing Emerging Threats and Technologies
The threat landscape is evolving rapidly. Cloud adoption, IoT expansion, and 5G connectivity all bring new risks that demand a coordinated response from network security and cyber security professionals.
AI-driven attacks are becoming more sophisticated, targeting both infrastructure and users. Organizations must stay ahead by using advanced analytics, automation, and integrated threat intelligence. According to Cybersecurity Trends: IBM’s Predictions for 2026, the future will require strong identity systems and adaptive defenses that bridge traditional security silos.
By proactively addressing these challenges, we ensure our defenses remain robust and future-ready.
The Role of Leadership and Communication
Leadership is the glue that binds network security and cyber security efforts together. Security leaders must bridge the gap between technical teams and business decision-makers.
Clear communication of cyber risk in business terms helps secure buy-in for investments and policy changes. When leaders champion security, it becomes part of the organization’s DNA, influencing decisions at every level.
Empowering teams through open dialogue and shared goals strengthens both morale and resilience.
LarsBirkeland.com: Practical Guidance for Security Leaders
For IT professionals and security leaders looking for actionable strategies and real-world insights, LarsBirkeland.com is a trusted resource. The site offers practical playbooks, leadership advice, and a supportive community to help you navigate the evolving challenges of network security and cyber security in 2026.
We’ve covered a lot about the evolving roles of network security and cyber security, and how understanding their differences sets you up for resilience in 2026. If you’re ready to take your next step and connect with others navigating these same challenges, you don’t have to do it alone. We’re all in this together, learning how to make smarter decisions and build stronger, more secure organizations.
If you want real-world guidance, shared experiences, and a supportive network of peers and leaders, come join us at the Join Cyber Launchpad Community. Let’s shape the future of security, side by side.