Cyber threats are escalating at an unprecedented rate, making digital forensics and cyber security more vital than ever in 2026. As attacks grow more sophisticated, the ability to investigate and defend digital environments is now a must-have skill for every organization and individual.
This essential guide is designed for professionals, students, and organizations eager to stay ahead. We will explore key definitions, core principles, current threats, investigative processes, must-have skills, career outlook, and future trends. Ready to boost your knowledge and resilience? Let’s dive in together.
Understanding Digital Forensics and Cyber Security
As we step further into 2026, understanding digital forensics and cyber security is more essential than ever. With our lives and businesses relying on technology, these fields form the backbone of digital trust and protection. Let’s break down what makes them so crucial, how they work together, and why they matter for all of us.
Defining Digital Forensics
Digital forensics is the process of recovering, preserving, and analyzing electronic evidence to uncover what happened in a digital environment. This field dives deep into computers, mobile devices, and network logs, searching for clues that can reveal everything from cybercrime to policy violations.
It’s both investigative and preventive, as organizations use findings to improve their defenses. For example, when a breach occurs, digital forensics experts might examine a hard drive or smartphone, piecing together the timeline of events. To learn more about the fundamentals, check out Digital Forensics Fundamentals.
Core Concepts of Cyber Security
Cyber security focuses on shielding digital assets from threats before they can cause harm. It’s all about prevention, using tools and strategies to block attackers and manage vulnerabilities.
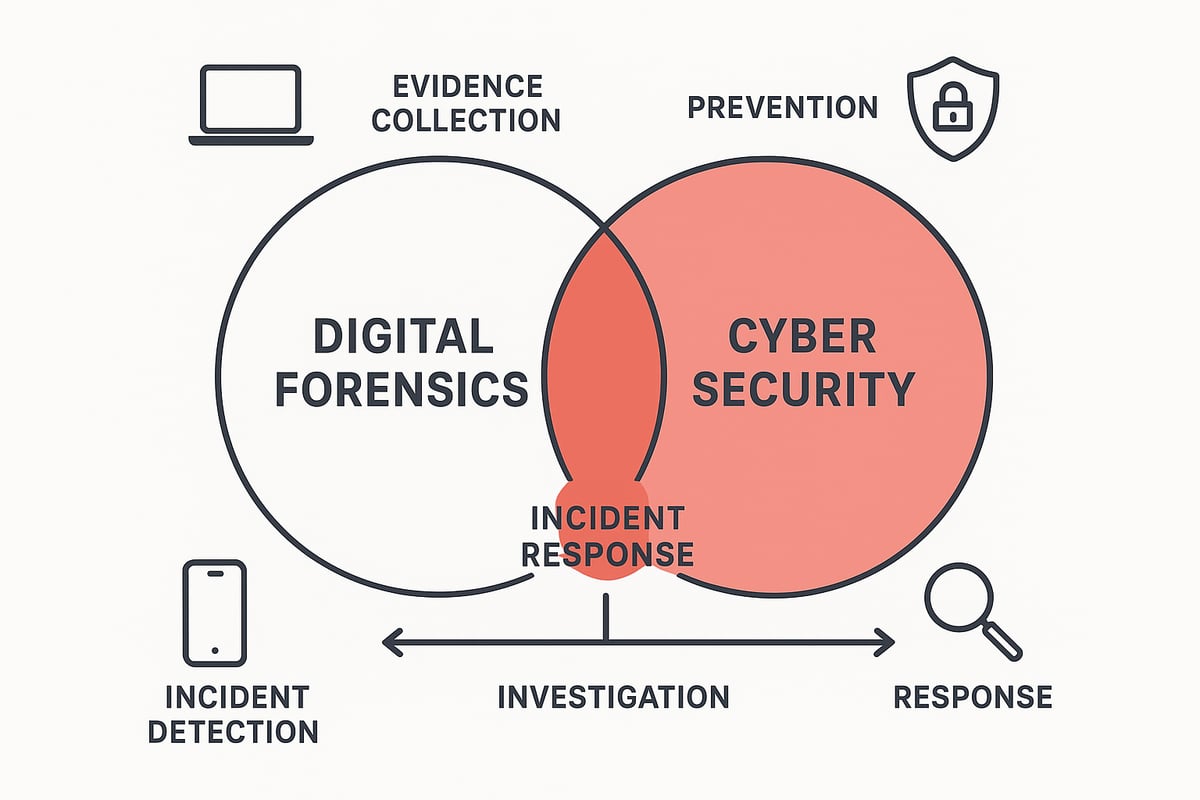
While digital forensics often reacts to incidents, cyber security works to stop them in the first place. However, the two are closely linked, especially in areas like incident response. Key concepts include firewalls, intrusion detection, and robust security policies. For example, setting up a firewall can prevent unauthorized access, while regular scans help find weaknesses.
The Convergence of Forensics and Cyber Security
In today’s world, digital forensics and cyber security are converging more than ever. Organizations and educators now recognize the benefits of blending investigative and defensive skills for a holistic approach.
This integration means teams can respond faster to incidents, using forensic techniques to analyze breaches and improve future defenses. For instance, an incident response team may leverage digital forensics to trace a cyber attack, then use those insights to strengthen their security posture.
Importance in 2026
The demand for experts in digital forensics and cyber security is skyrocketing in 2026. According to the Bureau of Labor Statistics, cyber security analyst jobs are projected to grow by 31 percent—much faster than most other fields.
Digital forensics plays a vital role in fighting sophisticated cybercrime, as more legal and corporate cases rely on digital evidence. Whether it’s law enforcement tracing ransomware or companies investigating insider threats, these skills are indispensable for keeping people and organizations safe.
Real-World Applications
The practical uses of digital forensics and cyber security are all around us. Law enforcement agencies use digital forensics to track down cyber criminals and gather evidence for prosecution. In the corporate world, security teams rely on these disciplines to investigate breaches and protect sensitive data.
Government agencies also depend on digital forensics and cyber security to secure critical infrastructure and respond to attacks quickly. These real-world examples remind us of the fields’ powerful impact.
The Digital Forensics Process: Step-by-Step
Understanding the digital forensics and cyber security process is essential for anyone wanting to safeguard digital assets or investigate incidents effectively. This step-by-step approach ensures that evidence is handled correctly, investigations are thorough, and outcomes are reliable. Let’s walk through each stage together.
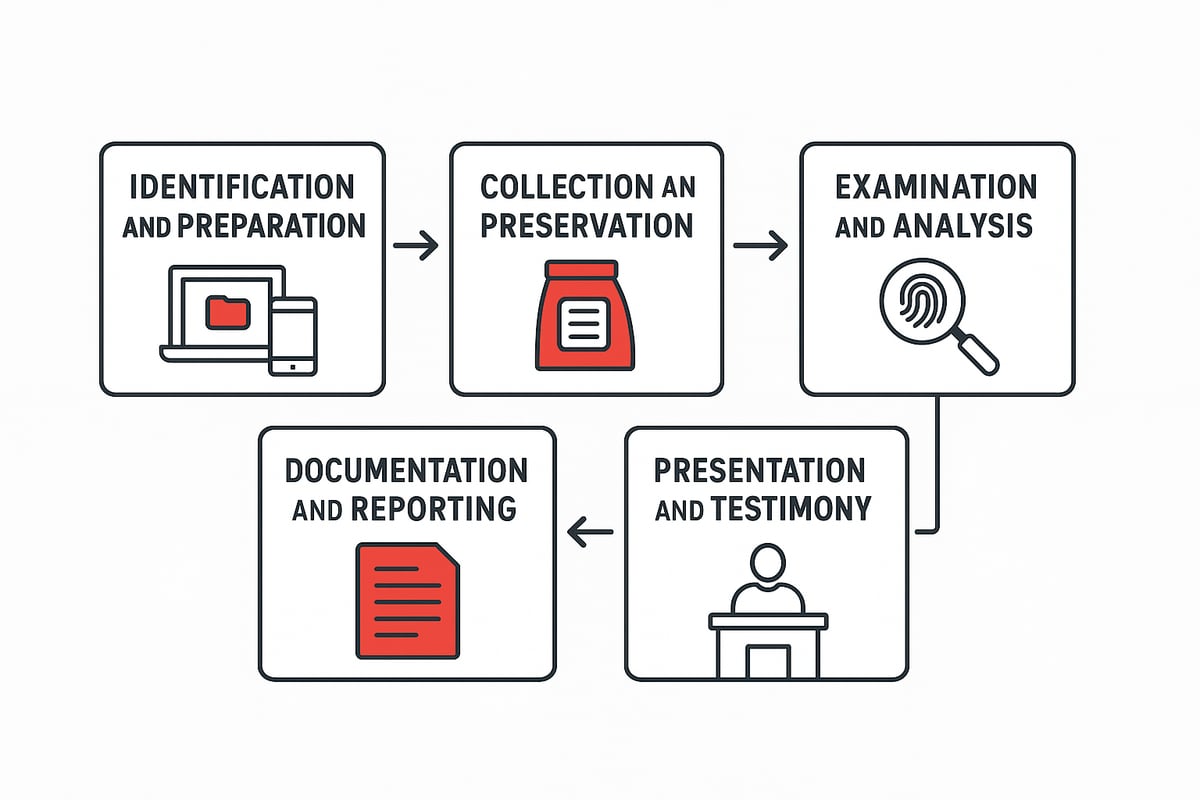
Step 1: Identification and Preparation
The first step in digital forensics and cyber security investigations is identifying when an incident requires a forensic response. This means knowing what to look for—suspicious activity, unexplained system changes, or unauthorized access attempts.
Being prepared is just as important as spotting incidents. Organizations need clear policies, incident response plans, and trained team members ready to act fast. Keeping everyone informed helps reduce confusion when time is critical.
For example, if an employee notices unusual login times or data transfers, quick identification can prevent further damage. Preparation turns chaos into order, allowing digital forensics and cyber security teams to act with confidence.
Step 2: Collection and Preservation of Evidence
Once an incident is identified, the next step in digital forensics and cyber security is collecting and preserving electronic evidence. This must be done carefully to ensure the data remains unaltered and admissible in legal proceedings.
Key actions include:
- Imaging hard drives to create exact copies
- Capturing volatile memory before a system shuts down
- Securing mobile devices and network logs
Using specialized tools and maintaining a strict chain of custody are vital. Each person handling evidence documents their actions, ensuring accountability.
For instance, collecting a suspect’s computer and properly sealing it helps maintain the integrity of the investigation and supports effective digital forensics and cyber security outcomes.
Step 3: Examination and Analysis
With evidence in hand, digital forensics and cyber security professionals move to examination and analysis. This step involves detailed inspection using forensic software, manual techniques, and a keen eye for anomalies.
Common activities include:
- Recovering deleted files
- Analyzing log files for suspicious activity
- Uncovering hidden or encrypted data
Tools like EnCase or FTK accelerate the process, but expert judgment remains irreplaceable. Analysts piece together timelines and identify the root cause of incidents.
For example, by examining storage media, investigators may discover malware traces or unauthorized data transfers, revealing the full picture behind the breach.
Step 4: Documentation and Reporting
Throughout every investigation, documentation is the backbone of digital forensics and cyber security. Every step, observation, and finding must be recorded with precision. This creates a clear trail for legal and internal purposes.
Effective documentation includes:
- Detailed notes on every action taken
- Screenshots, logs, and evidence tags
- Chronological reports outlining the investigative process
Reporting is equally important. Professionals must present findings in a way that is clear and understandable to non-technical audiences, including managers or legal teams.
For example, preparing a report for court or an internal review ensures that digital forensics and cyber security efforts stand up to scrutiny.
Step 5: Presentation and Testimony
The final step brings digital forensics and cyber security investigations into the spotlight. Experts may be called to present findings to company leadership, law enforcement, or in courtrooms.
Key skills here include:
- Explaining complex evidence in simple language
- Answering questions from non-technical stakeholders
- Providing testimony as an expert witness
Confidence and clarity are crucial. The ability to translate technical jargon into relatable terms helps juries, judges, and executives understand the significance of the evidence.
For instance, a forensic analyst might testify about how a cyber attack unfolded, supporting legal action and driving future improvements in digital forensics and cyber security.
Key Cyber Security Threats and Challenges in 2026
Staying ahead in digital forensics and cyber security requires constant vigilance. The threat landscape is shifting faster than ever, and we all need to be ready to adapt. Let’s explore the most pressing challenges facing us in 2026 and how we can build resilience together.
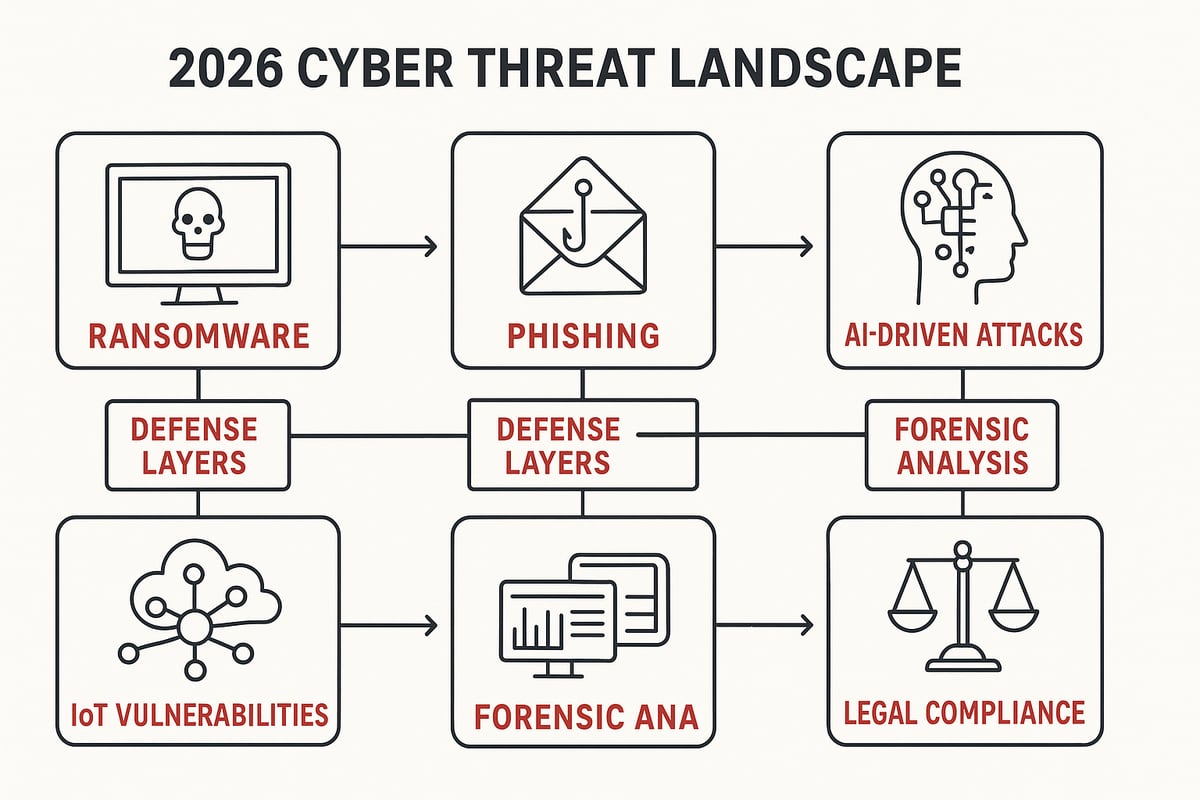
Evolving Threat Landscape
In 2026, the digital forensics and cyber security environment faces a wave of sophisticated threats. Ransomware is more targeted, phishing campaigns are smarter, and advanced persistent threats (APTs) lurk in critical infrastructure. Healthcare and government sectors are especially vulnerable, with cyber attacks rising sharply each year.
Organizations and individuals alike are feeling the pressure. The sheer volume and complexity of attacks demand a proactive mindset. For example, a hospital network might face a ransomware attack that threatens patient records, requiring immediate digital forensics and cyber security intervention.
As we move forward, it’s essential to anticipate these evolving dangers. By staying informed, we can strengthen our ability to respond and recover.
Advanced Attack Techniques
Attackers are raising the stakes with new methods. AI-driven attacks can adapt in real time, making detection tougher. Deepfakes and manipulated media threaten to undermine trust and spread misinformation. Supply chain compromises are on the rise, where attackers target vendors to infiltrate larger organizations.
Nation-state actors and organized cybercriminals are growing more sophisticated. For instance, APTs may operate undetected for months, quietly exfiltrating data. Digital forensics and cyber security teams must evolve, learning to spot subtle signs of compromise and react quickly.
Staying current with attack trends is not just helpful, it’s essential for everyone invested in digital safety.
Defensive Strategies and Controls
A layered defense is our best ally in digital forensics and cyber security. Firewalls, intrusion detection systems, and endpoint protection form the foundation. Proactive steps like threat hunting, vulnerability scanning, and anomaly detection add deeper defense.
Teams are increasingly turning to SIEM platforms for real-time monitoring and rapid response. By integrating forensics into daily operations, organizations can spot and stop threats sooner. For actionable guidance on countering these threats, see Cybersecurity Threats and Prevention.
These strategies, when combined with a culture of awareness, help us build a stronger, more resilient digital environment.
Incident Response and Recovery
When incidents strike, speed and coordination matter. Digital forensics and cyber security professionals must work together to identify, contain, and eradicate threats. Rapid containment prevents further damage, while forensic analysis uncovers the root cause.
A well-practiced incident response plan is a must. After containment, restoring systems and learning from the event ensures we’re better prepared next time. For example, tracing a ransomware attack from initial entry to payload delivery helps organizations close security gaps.
Clear communication and teamwork empower us to bounce back stronger after every challenge.
Regulatory and Legal Considerations
The legal landscape is keeping pace with digital forensics and cyber security challenges. Regulations like GDPR and CCPA set strict standards for data protection, breach notification, and evidence handling. Organizations must know their obligations, especially when collecting and preserving digital evidence.
Failing to follow protocols can result in penalties or lost court cases. For instance, mishandling evidence may render it inadmissible, impacting criminal or civil proceedings. Staying compliant not only protects organizations but also builds trust with clients and partners.
Understanding these requirements is vital for everyone committed to safeguarding digital assets.
Skills, Education, and Career Pathways
Exploring the world of digital forensics and cyber security opens up a wealth of opportunities for us as professionals, students, and organizations alike. Whether you are just starting or looking to advance your expertise, understanding the right mix of skills, education, and career pathways is crucial in 2026.
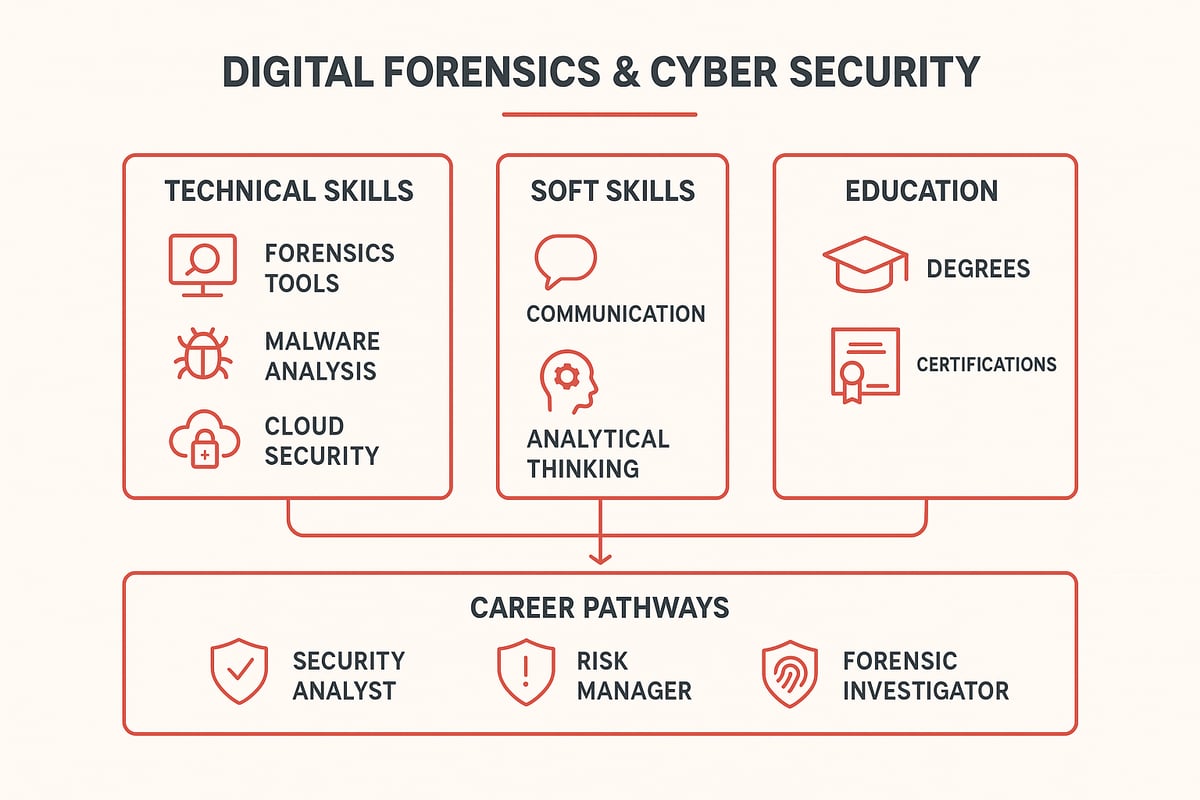
Essential Skills for 2026
To thrive in digital forensics and cyber security, you need a blend of technical and soft skills. Technical abilities like using forensic tools, conducting malware analysis, securing networks, and managing cloud environments are vital. Equally important are soft skills such as analytical thinking, clear communication, and a keen eye for detail.
- Proficiency with tools like EnCase or FTK
- Knowledge of network protocols and incident response
- Strong written and verbal communication
Mastering these skills helps you write clear reports, explain findings to stakeholders, and tackle complex investigations with confidence.
Education and Certifications
Investing in education is the foundation for a career in digital forensics and cyber security. Degree programs, including Bachelor’s and Master’s in cybersecurity or digital forensics, provide essential knowledge. Industry-recognized certifications such as CISSP, CEH, and GCFA open doors and demonstrate your commitment.
Choosing an accredited program is important. Look for institutions designated as National Centers of Academic Excellence. For a deeper dive into educational routes and certifications, check out Cybersecurity Education Pathways.
Coursework often covers computer forensics, cyber law, and penetration testing, helping you stay current with evolving threats and technologies.
Career Opportunities and Outlook
The career outlook for digital forensics and cyber security experts is bright. In-demand roles include security analyst, forensic investigator, risk manager, and incident responder. You will find opportunities in government, finance, healthcare, law enforcement, and consulting.
Graduates in digital forensics and cyber security enjoy high placement rates, especially those with security clearance. The field is expanding rapidly, with new roles emerging each year. This growth means you can shape your career in a direction that matches your strengths and interests.
Professional Development and Networking
Building a successful path in digital forensics and cyber security goes beyond formal education. Internships, hands-on labs, and real-world projects provide invaluable experience. Joining professional communities like ISACA or (ISC)² keeps you connected and informed.
Networking with peers and attending industry events can open doors to mentorship and job opportunities. Many professionals gain experience through internships at organizations like the FBI, Deloitte, or major corporations, giving them an edge in the job market.
LarsBirkeland.com: Strategic Guidance for Cybersecurity Leaders
For IT professionals and security leaders seeking actionable frameworks, LarsBirkeland.com offers expert-driven guides, templates, and a supportive community. The platform helps translate technical skills in digital forensics and cyber security into strategic impact, risk communication, and building resilient security programs.
If you are ready to take your expertise to the next level, exploring resources like this can make all the difference for your career and your organization.
Building a Resilient Digital Security Program
Creating a resilient digital forensics and cyber security program is essential for organizations determined to stay protected in 2026. A strong program not only defends against evolving threats but also empowers teams to respond with confidence when incidents occur. Let us break down how you can build, maintain, and improve a robust digital forensics and cyber security foundation.
Designing a Comprehensive Security Framework
Every successful digital forensics and cyber security strategy starts with a well-designed framework. Begin by conducting a thorough risk assessment to identify your organization’s unique vulnerabilities and threats. Next, develop clear security policies and governance structures that align with your business goals.
Implementing recognized frameworks such as NIST or ISO 27001 provides a solid foundation for your security program. For a deeper dive into the benefits and implementation of these models, check out Cybersecurity Frameworks Explained. These frameworks help unify your approach and ensure everyone knows their roles and responsibilities.
Integrating Forensics into Cyber Security Operations
Embedding forensic readiness into your organization’s cyber security operations is a proactive way to prepare for incidents. This means planning for evidence collection and analysis before an attack occurs. Integrate forensic processes into your incident response plans so your team can react quickly and efficiently.
Continuous monitoring of systems enables rapid forensic triage when threats are detected. By making forensic capabilities an everyday part of digital forensics and cyber security operations, you increase your chances of minimizing damage and recovering evidence that is critical for investigations.
Training and Awareness Programs
Building a resilient digital forensics and cyber security culture requires ongoing training for all staff, both technical and non-technical. Regular security awareness programs empower employees to recognize and report threats like phishing or social engineering.
Hands-on workshops, such as simulated phishing campaigns or forensics labs, increase engagement and retention of best practices. When everyone understands their role in the security ecosystem, your organization becomes much more resistant to attacks.
Technology and Tool Selection
Selecting the right technology is a cornerstone of any digital forensics and cyber security program. Look for tools that offer scalability, compliance features, and automation to streamline processes. Professional-grade software and hardware, such as EnCase, FTK, SIEM platforms, and endpoint detection tools, provide robust support for both prevention and investigation.
Evaluate tools regularly to ensure they meet your evolving needs and regulatory requirements. Investing in the right technology empowers your team to stay ahead of advanced threats and conduct effective forensic analysis when incidents arise.
Measuring and Improving Security Posture
Continuous improvement is key to resilience. Use clear metrics, like incident response times, audit results, and employee awareness scores, to evaluate your digital forensics and cyber security program’s effectiveness. Collect feedback after every incident and update your processes based on lessons learned.
Regular security assessments and penetration testing help identify new vulnerabilities and keep your defenses sharp. By embracing a mindset of ongoing learning and adaptation, your organization will be better prepared for whatever the future holds.
Future Trends and Innovations in Digital Forensics and Cyber Security
As we look ahead to 2026, the landscape of digital forensics and cyber security is undergoing rapid transformation. The pace of innovation is both exciting and challenging, bringing new opportunities for professionals and organizations. Let’s explore the trends and breakthroughs shaping our field, so we can prepare together for what’s next.
The Impact of AI and Automation
Artificial intelligence is revolutionizing digital forensics and cyber security. Machine learning tools are now essential for detecting threats, analyzing evidence, and automating repetitive investigative tasks. These smart systems can spot anomalies in massive datasets, flag suspicious behavior, and even classify new types of malware.
The benefits are clear: faster incident response, improved accuracy, and the ability to handle the growing scale of cyber threats. However, automation also brings risks, such as overreliance on algorithms or adversaries using AI to launch sophisticated attacks. Staying informed about cybersecurity trends reshaping 2026 is key to unlocking the full potential of these technologies.
As AI evolves, professionals in digital forensics and cyber security must adapt by learning to interpret automated findings and ensure ethical use of intelligent tools.
Cloud and IoT Security Challenges
The shift to cloud computing and the explosion of Internet of Things devices are redefining digital forensics and cyber security practices. Forensics experts now face unique challenges when investigating incidents across distributed cloud platforms and remote smart devices.
Key strategies include:
- Developing cloud-specific forensic techniques for data recovery and log analysis
- Securing IoT devices with continuous monitoring and strong authentication
- Collaborating with service providers to ensure evidence is preserved
As organizations rely more on cloud and IoT, the ability to secure and investigate these environments is a must-have skill for anyone in digital forensics and cyber security.
Privacy, Ethics, and Legal Evolution
With privacy regulations and ethical standards evolving worldwide, digital forensics and cyber security professionals must carefully balance investigation needs with personal rights. Laws like GDPR and CCPA shape how evidence is collected, stored, and shared.
This means:
- Adhering to strict data retention and consent rules
- Ensuring transparency in investigations
- Respecting privacy while pursuing justice
The changing legal landscape requires ongoing education and a commitment to ethical decision-making in digital forensics and cyber security work.
Workforce Development and Diversity
The future of digital forensics and cyber security depends on a skilled, diverse workforce. There is a growing demand for experts with interdisciplinary knowledge, strong technical abilities, and fresh perspectives.
To address the talent gap, organizations and educators are:
- Partnering to create hands-on training and mentorship programs
- Encouraging women and underrepresented groups to join the field
- Supporting lifelong learning and professional certifications
Embracing diversity helps us solve complex cyber challenges and strengthens the digital forensics and cyber security community.
Preparing for the Unknown: Resilience and Adaptability
No one can predict every cyber threat on the horizon, but we can build resilience into our organizations and careers. Staying agile, embracing continuous learning, and fostering a proactive security culture will help us adapt to whatever the future brings.
By working together, we can ensure digital forensics and cyber security remain strong, innovative, and ready for the next wave of challenges.
After walking through what it really takes to thrive in digital forensics and cyber security in 2026, you might be thinking, “How do I keep up and stay connected with others on this journey?” You’re not alone—navigating this fast-changing space is much easier when we share insights, swap stories, and support each other.
If you’re ready to take your learning further, build connections with like-minded pros, and get that extra edge in your career, I’d love for you to join us at the Join Cyber Launchpad Community. Let’s grow together and help shape the future of cyber security!