In 2026, headlines about massive data breaches and targeted cyber attacks seem to pop up every week. For organizations large and small, network security monitoring is no longer a luxury—it’s a necessity to keep up with today’s fast-changing threats.
This essential guide will help you cut through the confusion around network security monitoring. We’ll walk you through what it is, why it matters, which data and technologies matter most, and how to put best practices into action.
Ready to take control of your digital security? Let’s dive in together, make sense of the evolving landscape, and empower your team to build a safer, more resilient future.
Understanding Network Security Monitoring in 2026
The digital world in 2026 is moving fast, and so are the threats against it. To keep up, organizations need to understand what network security monitoring truly means and why it is the backbone of modern cyber defense. Let’s break down the essentials and see how this approach fits into the bigger security picture.
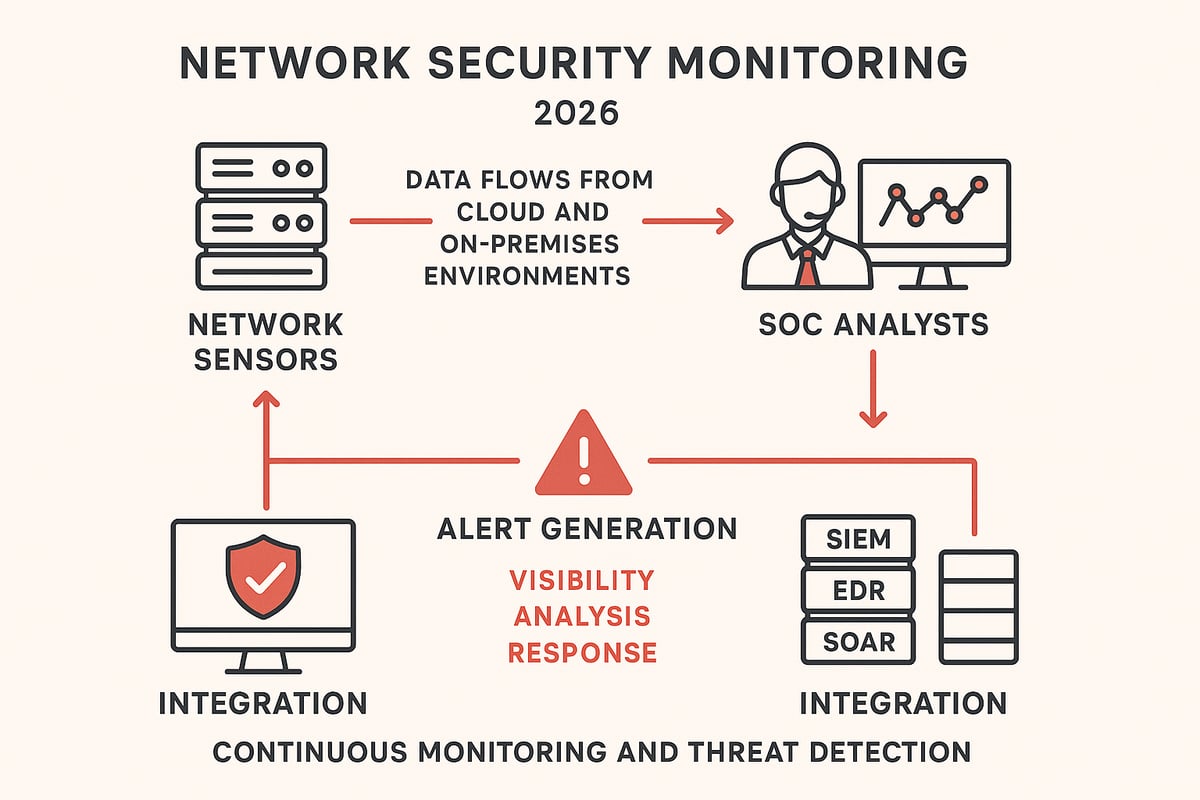
What is Network Security Monitoring?
Network security monitoring is the continuous collection, analysis, and escalation of network data to help organizations detect and respond to threats in real time. Unlike traditional monitoring or prevention tools, network security monitoring does not just look for known threats or performance issues. Instead, it captures rich network data, analyzes it for suspicious activity, and empowers security teams to act swiftly.
In modern Security Operations Centers (SOCs), network security monitoring is considered the foundation for threat detection and response, as noted by Corelight. For example, many organizations have used network security monitoring to uncover stealthy intrusions that older controls missed. If you want a deeper dive into the basics, check out this What is Network Security resource for foundational knowledge.
Why NSM is Critical in 2026
Cyber attackers are growing more sophisticated every year. Even the best preventive defenses can be bypassed, making network security monitoring essential for timely detection. The attack surface is expanding with cloud, IoT devices, and hybrid work setups, increasing the risk of undetected threats.
Regulatory and compliance pressures are also rising, requiring organizations to quickly identify and report incidents. The volume of encrypted traffic is surging, and advanced persistent threats are more common than ever. Network security monitoring provides the visibility needed to spot these threats before they cause serious harm.
Core Principles of NSM
At the heart of network security monitoring is the assumption that intruders might already be inside the network. This mindset shifts the focus from just finding vulnerabilities to actively looking for evidence of threats.
Key principles include:
- Prioritizing visibility and context across all environments
- Delivering actionable intelligence for faster response
- Supporting proactive threat hunting, not just reacting to incidents
For example, with network security monitoring, security teams can hunt for subtle signs of compromise and respond long before damage is done.
Key Benefits for Organizations
Network security monitoring offers organizations several critical advantages. Early detection of breaches and lateral movement helps reduce the impact of attacks. By improving mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR), teams can contain threats more efficiently.
Other benefits include:
- Enhanced visibility across cloud, on-premises, and hybrid setups
- Stronger support for compliance (SOC 2, ISO 27001, GDPR)
- Reduced business risk and less operational disruption
With network security monitoring, organizations gain confidence that they can meet both business and regulatory demands.
NSM in the Broader Security Ecosystem
Network security monitoring does not work in isolation. It integrates with SIEM, EDR, SOAR, and NDR solutions to create a unified defense. NSM data complements endpoint and cloud security tools, feeding valuable insights into automated response workflows.
For instance, network security monitoring data can trigger automated investigations or help SOC teams prioritize alerts, making the entire security ecosystem more effective.
Key Data Types and Technologies in NSM
Staying ahead of threats in 2026 means understanding what powers effective network security monitoring. Let’s explore the data, tools, and best practices that keep our digital environments secure and resilient.
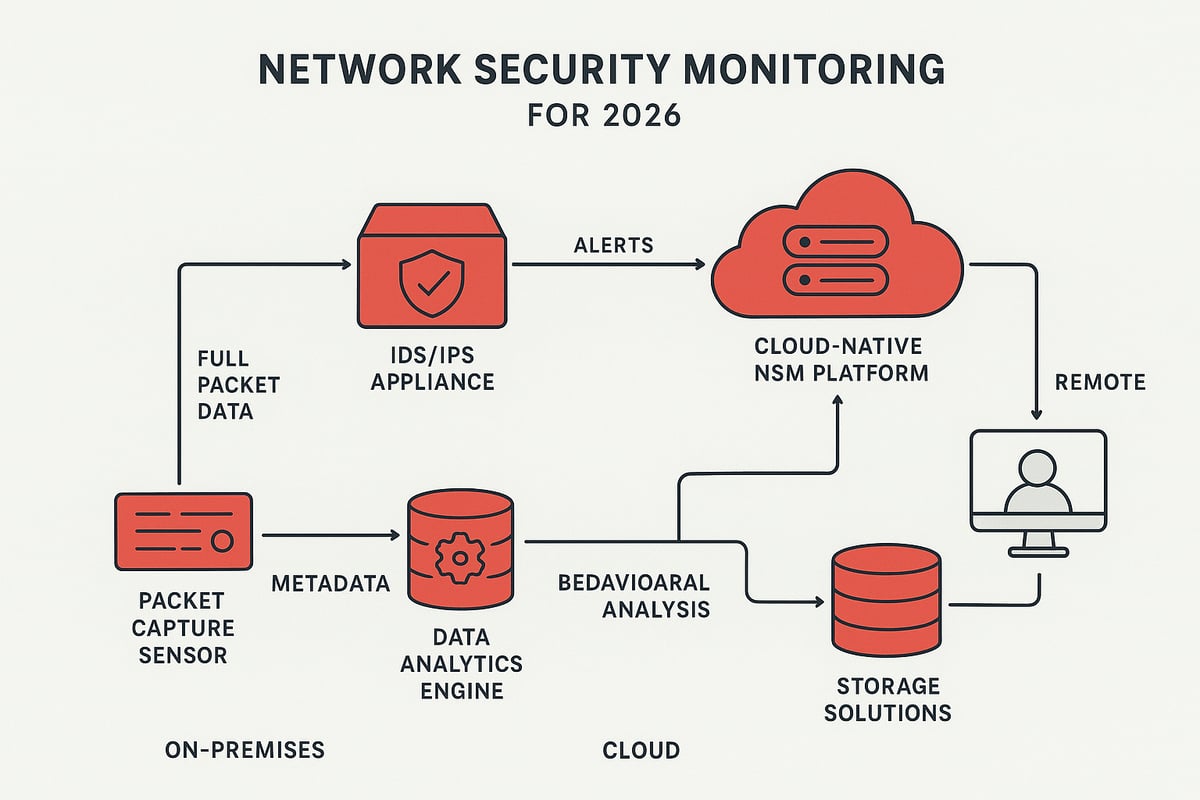
Essential Data Types for Effective Monitoring
Network security monitoring thrives on a diverse set of data types. Full content data, such as packet captures, allows deep inspection of network traffic. Extracted content, like files or executables, helps analysts reconstruct sessions and spot malicious payloads.
Transactional data records session metadata: timestamps, IP addresses, and ports, providing critical context for investigations. Alert data comes from intrusion detection systems or custom triggers, highlighting suspicious activities. Behavioral data tracks deviations from established baselines, giving early warning of novel or stealthy threats.
By combining these data types, network security monitoring delivers the visibility we need to detect and respond to evolving cyber risks.
Modern NSM Technologies and Tools
The technology powering network security monitoring has rapidly advanced. Today, organizations deploy network sensors and probes to capture traffic across on-premises, cloud, and hybrid environments. Integration with IDS/IPS systems, such as Suricata or Snort, supports real-time detection of known threats.
AI-driven analytics and machine learning now play a central role, helping us identify anomalies and automate threat detection. Cloud-native NSM solutions scale easily, making them perfect for dynamic infrastructures. For those evaluating their options, open-source platforms like Zeek or commercial offerings provide flexibility and advanced features.
To learn more about the role of IDS within network security monitoring, check out Intrusion Detection Systems Explained.
Data Collection and Analysis Best Practices
Success with network security monitoring starts with strategic sensor placement. Deploy sensors at the perimeter, inside the network, in cloud segments, and at remote branches for full coverage. Out-of-band deployment ensures monitoring does not disrupt business operations.
Prioritize data fidelity and completeness to avoid blind spots. Retain data long enough for thorough investigations. Enrich collected data with threat intelligence feeds to accelerate detection and response. Behavioral analytics tools help us spot insider threats and subtle attacks that bypass signature-based defenses.
By following these best practices, organizations build a monitoring program that is both robust and adaptable.
Integration with Other Security Technologies
Network security monitoring works best when integrated with other security tools. Feeding NSM data into SIEM platforms enables centralized analysis and correlation. Orchestrating with SOAR platforms streamlines response, automating repetitive tasks.
Pairing NSM with EDR solutions provides deep endpoint forensics and rapid containment of threats. Cloud security posture management (CSPM) and cloud workload protection platforms (CWPP) further extend visibility into cloud environments. For example, using NSM data alongside EDR helps investigate suspicious encrypted traffic that might otherwise go unnoticed.
This collaborative ecosystem strengthens defenses across every layer of the organization.
Challenges in Data Management
Managing data in network security monitoring is no small feat. The sheer volume of network data can strain storage and processing resources. Scalability is essential to keep pace as the network grows and evolves.
Privacy is another concern. Organizations must balance the depth of monitoring with regulatory and ethical obligations, ensuring sensitive information is protected. Careful planning helps us avoid overwhelming systems and teams, while still gaining the insight needed to defend against modern threats.
By addressing these challenges, network security monitoring stays effective and sustainable.
Deploying Network Security Monitoring: Steps and Best Practices
Rolling out network security monitoring can feel overwhelming, but breaking the process into clear steps makes it manageable for any organization. Whether your environment is on-premises, cloud, or hybrid, a thoughtful deployment ensures you get the visibility and protection you need. Let’s walk through each step together.
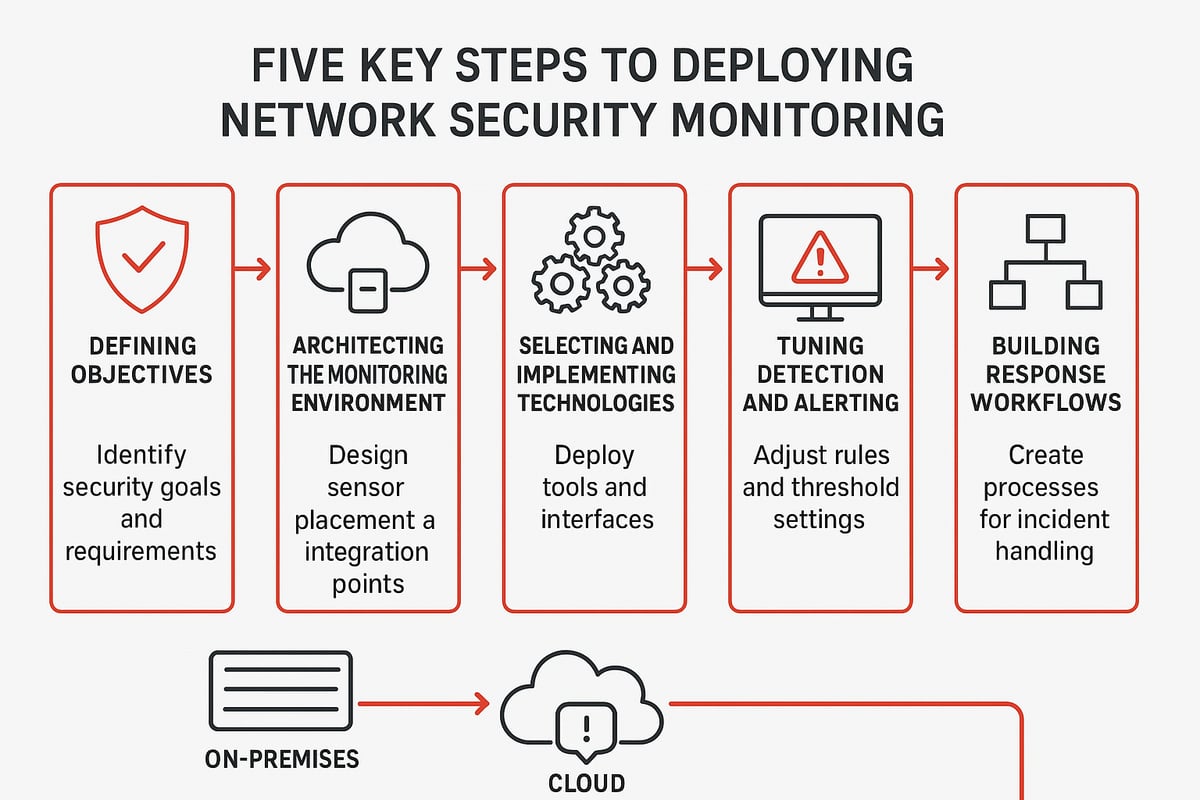
Step 1: Define Objectives and Scope
The first step in a successful network security monitoring program is clarifying what you want to achieve. Start by identifying your business-critical assets, such as financial databases or intellectual property, and mapping out any compliance requirements that apply to your industry.
Determine your main monitoring goals. Are you focused on threat detection, incident response, compliance, or simply gaining better visibility? By outlining these objectives, you can prioritize resources and avoid monitoring unnecessary network segments.
For example, if sensitive data flows between your headquarters and remote sites, these should be a top focus. Each organization’s needs are unique, so tailor your network security monitoring scope to your specific risks and goals.
Step 2: Architect Your Monitoring Environment
Next, it’s time to design how your network security monitoring will fit into your unique infrastructure. This involves mapping your network topology, including on-premises systems, cloud resources, and remote locations. Sensor placement is critical: aim to cover both north-south (incoming and outgoing) and east-west (lateral) traffic.
Consider future growth, scalability, and redundancy from the beginning. For organizations leveraging cloud services, integrating best practices is key. For more on this, check out Cloud Security Best Practices for guidance on aligning your monitoring with evolving cloud environments.
A well-architected network security monitoring setup ensures you don’t miss critical threats, regardless of where your assets reside.
Step 3: Choose and Implement NSM Technologies
With your architecture mapped, select the right tools for your network security monitoring program. Evaluate open-source solutions like Zeek or commercial platforms that offer advanced analytics and support for cloud-native environments.
Integration is another crucial factor. Make sure your chosen tools can work with your existing security stack and enable centralized visibility. Deploy sensors at strategic points, configure data collection, and set up alerting to ensure nothing slips through the cracks.
For example, using Zeek for deep packet inspection in a cloud environment can provide granular traffic visibility. The right technologies make network security monitoring both scalable and effective.
Step 4: Tune Detection and Alerting
Once your tools are in place, take the time to tune your detection rules and alerting logic. Out-of-the-box rules can generate noise, so customize them to match your organization’s risk profile and business context. This reduces false positives and helps your team focus on real threats.
Prioritize alerts based on asset criticality and regularly update detection logic with the latest threat intelligence. Share lessons learned across your security team to improve over time.
For instance, tailoring alerts for ransomware indicators can make your network security monitoring program more responsive to emerging threats and reduce analyst fatigue.
Step 5: Build Response and Investigation Workflows
Finally, create clear workflows for responding to incidents detected by your network security monitoring tools. Integrate your monitoring platform with incident response playbooks and automation tools like SOAR to streamline handling of critical alerts.
Establish clear escalation paths so that high-priority incidents are quickly addressed. Contextualized data and forensic capabilities enable rapid investigation, helping your team reconstruct attack timelines with confidence.
For example, using network security monitoring data during post-mortems can reveal how attackers moved through your environment and what steps to take to prevent future incidents.
Overcoming Common Network Security Monitoring Challenges
Staying ahead in network security monitoring means facing—and overcoming—a unique set of challenges. As threats evolve, organizations must adapt their monitoring strategies to maintain strong protection. Let’s explore common hurdles and practical solutions, so your team can gain the confidence and clarity needed to succeed.
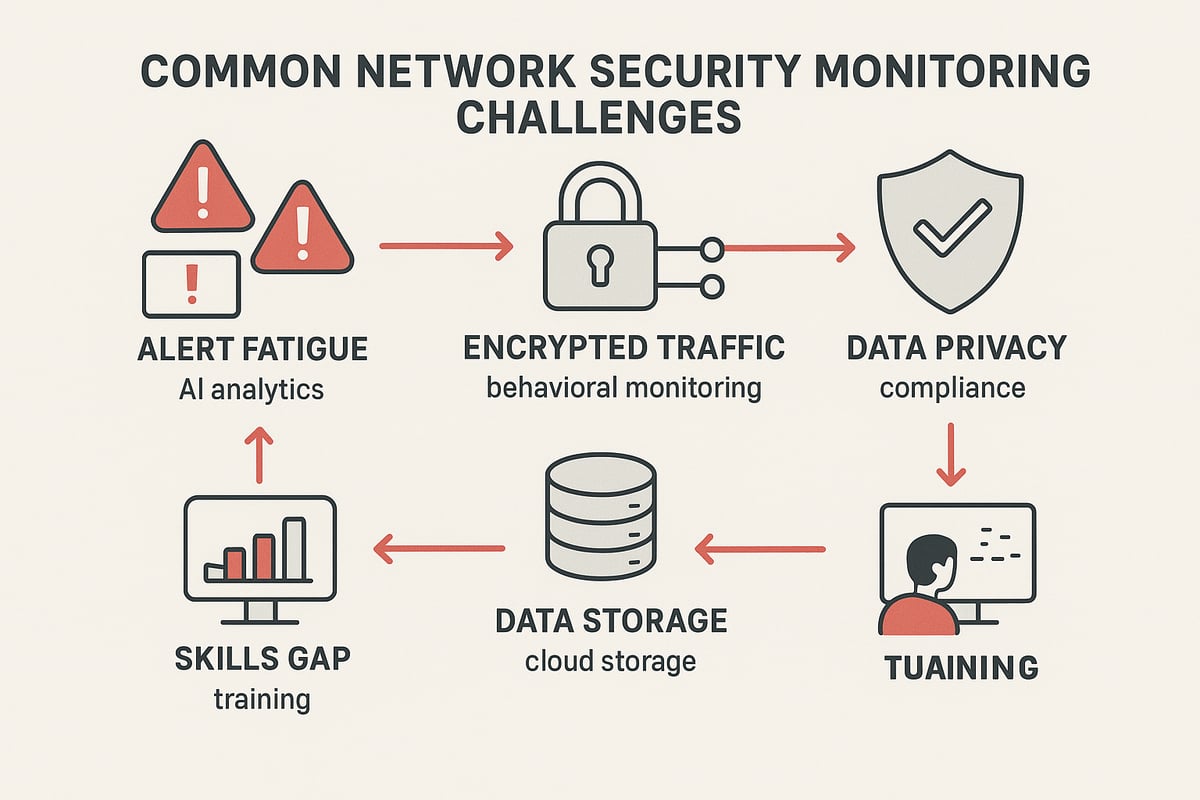
Alert Fatigue and Signal-to-Noise Ratio
High alert volumes are a real concern in network security monitoring. SOC teams can feel overwhelmed when hundreds of alerts compete for attention every hour. This overload makes it easy to miss genuine threats hiding in the noise.
To tackle this, it’s crucial to fine-tune detection rules and prioritize actionable alerts. Automation and AI-driven analytics can help filter out routine or low-risk activity, letting analysts focus on what really matters. Customizing detection logic, informed by resources like the Top 10 Network Security Threats in 2026, can reduce alert volume and improve response. Many organizations have seen up to a 40 percent reduction in false positives by tailoring their network security monitoring approach.
Encrypted Traffic and Visibility Gaps
With more network traffic encrypted than ever, visibility is a growing challenge for network security monitoring. Encrypted protocols like TLS and SSL protect privacy, but they also limit the ability to inspect payloads for threats.
Organizations can respond by analyzing metadata, such as connection patterns and session lengths, and using behavioral monitoring to detect anomalies. Selective decryption at trusted points, combined with advanced analytics, helps bridge visibility gaps. By focusing on transactional and behavioral data, teams can spot suspicious activity even in encrypted sessions.
Data Privacy and Compliance Concerns
Balancing robust network security monitoring with privacy requirements is essential. Regulations like GDPR and CCPA demand careful handling of sensitive data, especially when monitoring involves packet captures or deep traffic analysis.
To stay compliant, organizations should implement data minimization and masking techniques. Avoid collecting more data than necessary, and use anonymization wherever possible. In industries like healthcare, deploying NSM with privacy in mind supports both security and regulatory goals. Transparent policies and regular audits help maintain trust.
Data Storage, Analysis, and Scalability
Network security monitoring generates vast amounts of data every day. Without proper planning, storage costs and analysis workloads can quickly spiral out of control.
Leveraging cloud storage and big data platforms allows for better scalability and cost management. Set clear data retention policies to balance compliance with operational needs. Automated archiving and indexing make it easier to retrieve relevant information during investigations. For global organizations, distributed storage and analytics support hybrid and multi-cloud environments without sacrificing performance.
Skills Gap and Analyst Enablement
A shortage of skilled analysts is a common obstacle in network security monitoring. Interpreting complex network data requires experience and training, but not every team has access to seasoned professionals.
To empower analysts, invest in user-friendly dashboards and AI-assisted analytics that simplify alert triage and investigation. Ongoing training programs build confidence, while clear documentation and playbooks accelerate onboarding. By fostering a culture of continuous learning and collaboration, organizations can close the skills gap and make the most of their monitoring investments.
NSM vs. Other Security Technologies: What Sets It Apart?
When navigating the modern security landscape, it’s easy to feel overwhelmed by the variety of solutions available. Let’s break down how network security monitoring stands out when compared with other major cybersecurity technologies. This clarity will help us all make smarter decisions about building a resilient defense.
NSM vs. Endpoint Detection and Response (EDR)
Network security monitoring offers comprehensive visibility across all network traffic, while EDR zooms in on activity happening right on endpoints. NSM excels at spotting suspicious movement between devices, such as lateral attacks, that might slip past endpoint-only defenses. EDR, on the other hand, provides powerful forensic tools and can block threats directly at the device level.
By combining network security monitoring with EDR, organizations gain a layered defense that covers both broad network activity and detailed endpoint behavior. For example, NSM might detect unusual data transfers, prompting EDR to investigate affected systems more deeply. For a deeper dive into evolving threats and why this layered approach matters, check out Cybersecurity Threats and Prevention.
NSM vs. Intrusion Detection and Prevention Systems (IDS/IPS)
Intrusion Detection and Prevention Systems focus mainly on identifying known threats through signature-based rules. While valuable, IDS/IPS can miss subtle or novel attacks that don’t match existing patterns. Network security monitoring goes further by collecting and analyzing a wider range of data, adding context and enabling more thorough investigations.
NSM can validate, enrich, and escalate alerts from IDS/IPS, ensuring that nothing important slips through the cracks. For instance, if an IDS flags a suspicious packet, NSM can reconstruct the full session to determine the real impact. This partnership means organizations can respond faster and more effectively to threats.
NSM vs. Network Performance Monitoring (NPM)
Network Performance Monitoring is all about ensuring systems run smoothly and efficiently. It focuses on metrics like uptime, latency, and bandwidth usage, not on security risks. In contrast, network security monitoring zeroes in on detecting threats, investigating incidents, and meeting compliance requirements.
Interestingly, these two solutions can work hand in hand. NPM might spot unusual spikes in traffic or unexpected downtime, which could signal an attack. NSM then steps in to analyze the traffic for signs of compromise. Together, they offer a well-rounded view of both health and security.
NSM and Cloud Security Tools (CSPM/CWPP)
Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platforms (CWPP) are designed to secure cloud configurations and workloads. However, many cloud-native tools lack deep visibility into network traffic, especially as organizations embrace hybrid and multi-cloud environments. Network security monitoring fills this gap by providing detailed analysis of cloud traffic patterns.
Integration between NSM and cloud security tools brings greater visibility and control. For example, NSM can detect suspicious east-west movement between cloud resources, alerting teams to potential breaches. For expert insights on how organizations are prioritizing monitoring and Zero Trust in cloud spaces, see the KPMG Cloud Monitor 2025 Report.
Future-Proofing Your NSM Program for 2026 and Beyond
Staying ahead in network security monitoring is not just a technical challenge, it’s a mindset. As we look toward 2026, the landscape is shifting rapidly, with new threats, technologies, and business models reshaping how we protect our digital environments. Let’s explore how organizations can keep their network security monitoring resilient and effective in the face of constant change.
Adapting to Evolving Threats and Technologies
Attackers are becoming more creative, often leveraging AI and automation to launch sophisticated campaigns. This means network security monitoring programs must evolve continually. Staying up-to-date with emerging protocols, encrypted traffic patterns, and advanced persistent threats is essential.
Organizations should invest in solutions that use machine learning to spot unknown threats. Regularly updating detection logic and analytics ensures that new vulnerabilities and attack vectors are not missed. Industry research shows the demand for real-time visibility and AI-driven analytics is fueling rapid market growth, as highlighted in the Network Monitoring Market Growth Projections.
By fostering a culture of curiosity and adaptability, teams can better anticipate and counter emerging threats.
Embracing Cloud, IoT, and Hybrid Work Environments
Today’s networks are everywhere—spanning on-premises, cloud, IoT, and remote endpoints. This decentralization creates both visibility challenges and opportunities for network security monitoring. Flexible, cloud-native NSM solutions are now crucial for organizations managing dynamic and distributed environments.
Monitoring IoT traffic is especially important, as connected devices often lack traditional security controls. By extending network security monitoring to SaaS applications and remote users, organizations can spot unusual device behavior and mitigate risks early.
Success in this area means embracing tools that can scale quickly and adapt to shifting network boundaries. This approach helps protect critical assets, no matter where they reside.
Automation, Orchestration, and AI in NSM
Manual analysis alone can’t keep pace with the volume and complexity of today’s security alerts. That’s why automation and AI are transforming network security monitoring. SOAR platforms enable automated response workflows, reducing the time threats linger undetected.
Machine learning models can triage alerts, detect anomalies, and even suggest investigation paths. Research into frameworks like NetMoniAI: AI Framework for Network Security shows how AI can automate many aspects of network monitoring, making programs more responsive and less reliant on manual intervention.
By integrating AI and orchestration, teams free up analysts to focus on complex investigations, ultimately improving detection and response.
Continuous Improvement and Metrics
No network security monitoring program is ever “done.” Continuous improvement is vital for long-term success. Metrics such as mean-time-to-detect (MTTD), mean-time-to-respond (MTTR), false positive rates, and coverage levels should be tracked and reviewed regularly.
Teams should routinely update detection rules, review incident workflows, and invest in ongoing analyst training. Cross-team collaboration is also key—sharing lessons learned and adapting to new threats as a group.
Quarterly reviews and open communication foster a proactive mindset, ensuring that network security monitoring remains effective as threats and technologies evolve.
We’ve covered a lot about the ins and outs of network security monitoring in 2026, and I hope you feel more confident about where to start and how to keep your organization safe. Remember, you’re not alone on this journey—there’s a whole community of security leaders and IT pros facing the same challenges, asking the same questions, and sharing real-life lessons.
If you want to keep building your skills, swap stories, and get practical guidance that actually works, I’d love for you to Join CISO Launchpad Community. Let’s tackle the future of security together!







